
Dee
@viriback
#Malware C2 hunter #infosec passionate. Tweets are my own.
ID: 3101795085
https://viriback.com 21-03-2015 13:41:00
1,1K Tweet
9,9K Followers
1,1K Following





C2 panel of Mave Stealer https[://web.]maveproj3ct[.lol/ #MAVESTEALER #PANEL #CTI #STEALER Who said what? Mikhail Kasimov Dee
![Coral Jasmine (@fact_finder03) on Twitter photo C2 panel of Mave Stealer
https[://web.]maveproj3ct[.lol/
#MAVESTEALER #PANEL #CTI #STEALER
<a href="/g0njxa/">Who said what?</a> <a href="/500mk500/">Mikhail Kasimov</a> <a href="/ViriBack/">Dee</a> C2 panel of Mave Stealer
https[://web.]maveproj3ct[.lol/
#MAVESTEALER #PANEL #CTI #STEALER
<a href="/g0njxa/">Who said what?</a> <a href="/500mk500/">Mikhail Kasimov</a> <a href="/ViriBack/">Dee</a>](https://pbs.twimg.com/media/GtpLfZ0XMAA3jM_.jpg)




AIRAVAT RAT web panel url : https://rat.riyajchowdhury[.]xyz/ Not detected on VirusTotal more AIRAVAT RAT web panels detected by #C2Watcher on github.com/Xanderux/C2wat…
![Xanderux (@xanderuxsf5) on Twitter photo AIRAVAT RAT web panel
url : https://rat.riyajchowdhury[.]xyz/
Not detected on <a href="/virustotal/">VirusTotal</a>
more AIRAVAT RAT web panels detected by #C2Watcher on github.com/Xanderux/C2wat… AIRAVAT RAT web panel
url : https://rat.riyajchowdhury[.]xyz/
Not detected on <a href="/virustotal/">VirusTotal</a>
more AIRAVAT RAT web panels detected by #C2Watcher on github.com/Xanderux/C2wat…](https://pbs.twimg.com/media/GvUp29EXIAA04s-.jpg)





Odyssey Stealer C2 Panel http[://185.93.89[.63/login http[://sdojifsfiudgigfiv[.to/login #Threathunting #Odyssey #Stealer #ThreatIntel #Panel MalwareHunterTeam Dee Who said what? RussianPanda 🐼 🇺🇦 Mikhail Kasimov




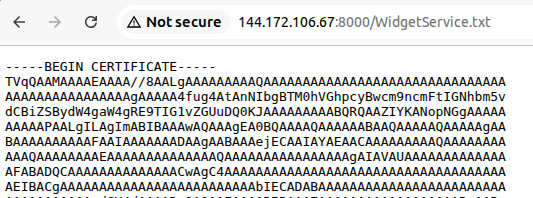

![Germán Fernández (@1zrr4h) on Twitter photo 🚩 Website impersonating AnyDesk on anydeske[.]icu, downloads a .NET loader which then launches a stealer, both unknown to me 🤔
Nexts stages:
- https://pastebin[.]com/raw/YwvHhwUk
- https://pastebin[.]com/raw/WrgrtxSu
- http://45.145.7[.]134/hook/upgrade.php
- 🚩 Website impersonating AnyDesk on anydeske[.]icu, downloads a .NET loader which then launches a stealer, both unknown to me 🤔
Nexts stages:
- https://pastebin[.]com/raw/YwvHhwUk
- https://pastebin[.]com/raw/WrgrtxSu
- http://45.145.7[.]134/hook/upgrade.php
-](https://pbs.twimg.com/media/GtRDtqHXwAAqWlK.png)
![Germán Fernández (@1zrr4h) on Twitter photo + Panel: http://45.145.7[.]134/login.php
<a href="/ViriBack/">Dee</a> + Panel: http://45.145.7[.]134/login.php
<a href="/ViriBack/">Dee</a>](https://pbs.twimg.com/media/GtRmqorXIAA0Ef-.jpg)


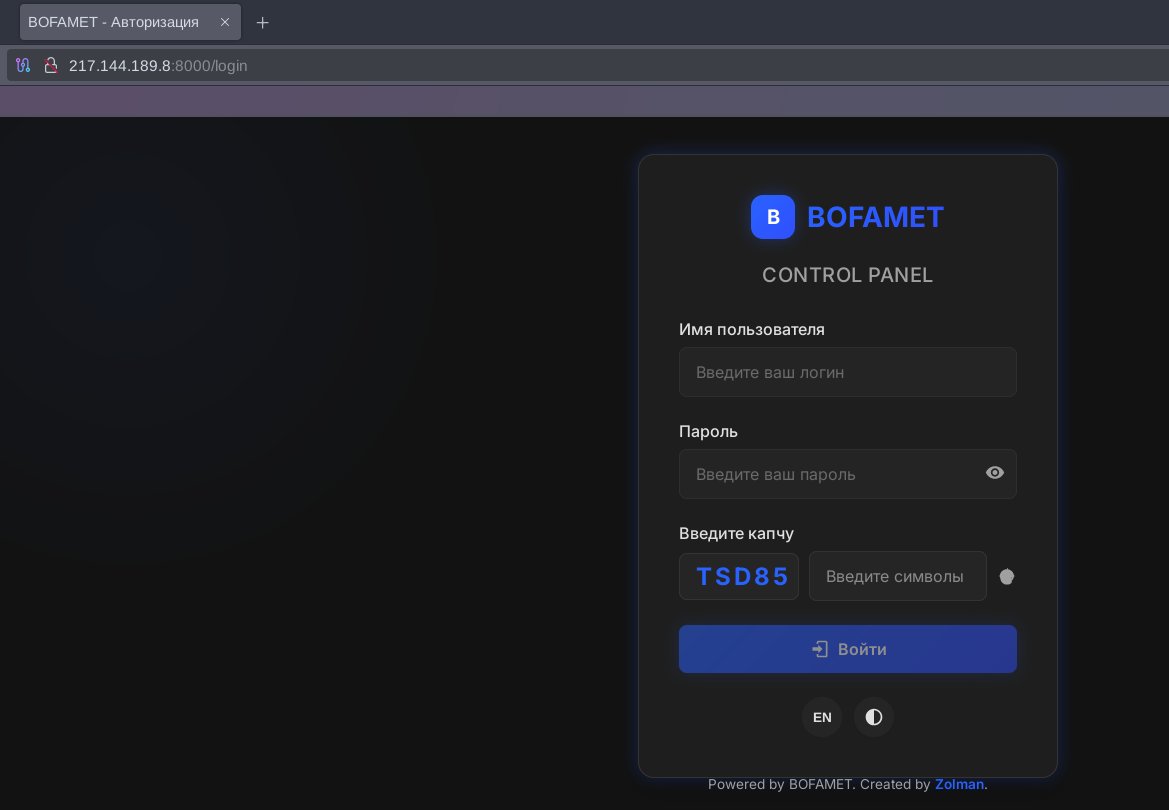


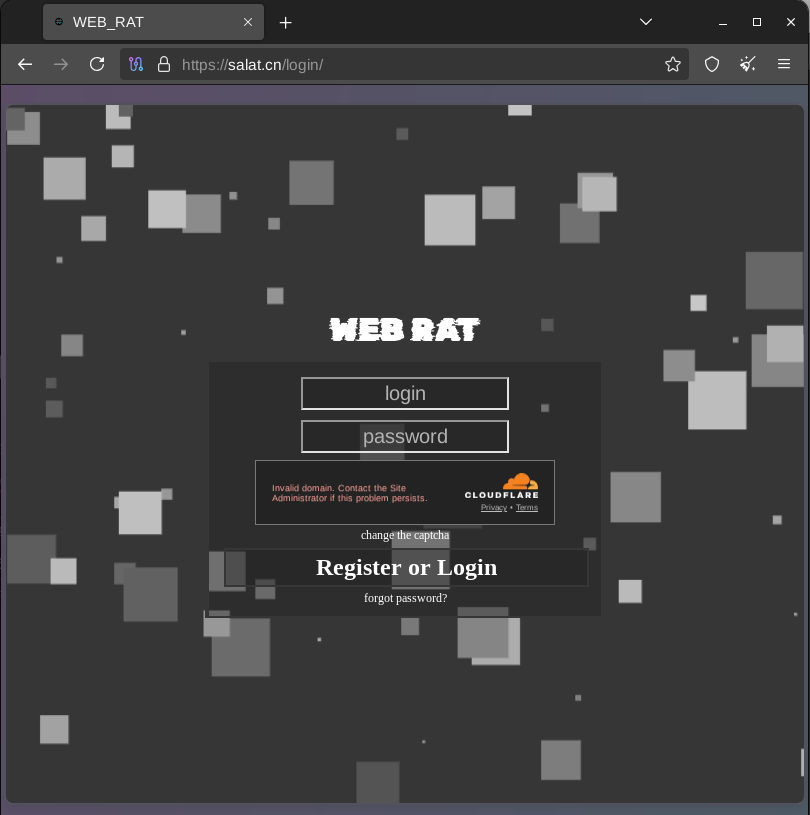
![Dee (@viriback) on Twitter photo #malware #TinyLoader C2 Panel
176.46.152[.]46/zyxic/login.php
See: app.any.run/tasks/e2dbfe51…
cc: <a href="/ET_Labs/">ET Labs</a> #malware #TinyLoader C2 Panel
176.46.152[.]46/zyxic/login.php
See: app.any.run/tasks/e2dbfe51…
cc: <a href="/ET_Labs/">ET Labs</a>](https://pbs.twimg.com/media/Gxq9EfUWgAAxrxh.png)