Matt Creel
@tw1sm
Adversary Simulation @ SpecterOps | OSCP | CRTO | tw1sm.bsky.social
ID: 981613211685400578
https://blog.tw1sm.io 04-04-2018 19:23:21
236 Tweet
1,1K Followers
220 Following

Many in the Mythic Community have asked for a way to standardize BOF/.NET execution within Mythic Agents. Today I'm releasing Forge, a new Mythic container to do just that: posts.specterops.io/forging-a-bett… We're starting off with default support for Apollo and Athena. Check it out! :)



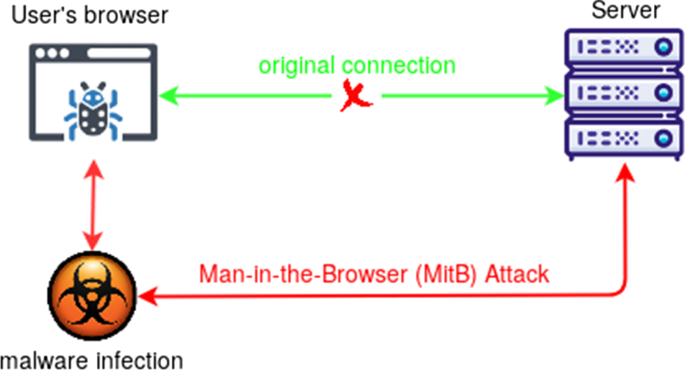
cuddlephish : Weaponized multi-user browser-in-the-middle (BitM) for penetration testers : github.com/fkasler/cuddle… Details : link.springer.com/article/10.100… credits Forrest Kasler



I'm super happy to announce an operationally weaponized version of Yuval Gordon's BadSuccessor in .NET format! With a minimum of "CreateChild" privileges over any OU it allows for automatic escalation to Domain Admin (DA). Enjoy your inline .NET execution! github.com/logangoins/Sha…


So excited to see this one come out! Awesome post from Julian Catrambone on why IdP's should still be scrutinized! (tl;dr: OneLogin leaked random customer logs with info valid to generate JWT's) 👀 specterops.io/blog/2025/06/1…




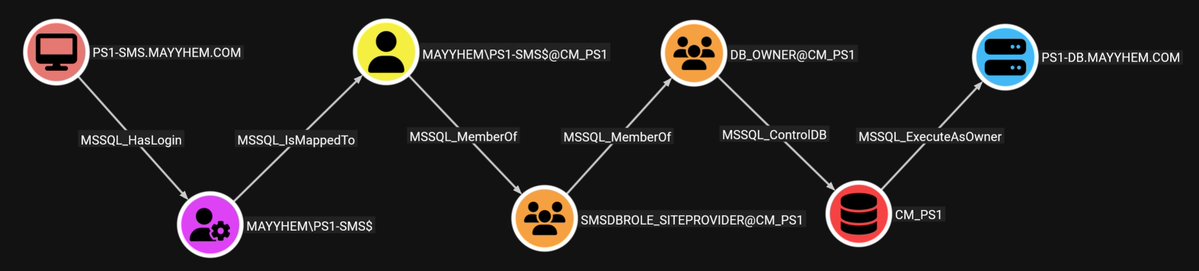
Made some changes to SoaPy to allow ADWS recon to be ingested into Matt Creel 's BOFHound offline for upload to BloodHound. A blog detailing an operational perspective of ADWS collection from Linux with BloodHound is coming soon. For now, the changes are here: github.com/logangoins/Soa…

My first SpecterOps blog! Ever wanted to collect Active Directory information from LDAP for a Red Team? Using LDAP's more OPSEC-considerate cousin: ADWS can be used to improve upon the already present advantages of using smaller-scaling LDAP queries. specterops.io/blog/2025/07/2…