Tract0r
@tract0r_
Offensive Security
Windows Intrernals
Active Directory
Initial Access
Malware Dev
ID: 548239876
08-04-2012 07:49:44
2,2K Tweet
266 Followers
158 Following









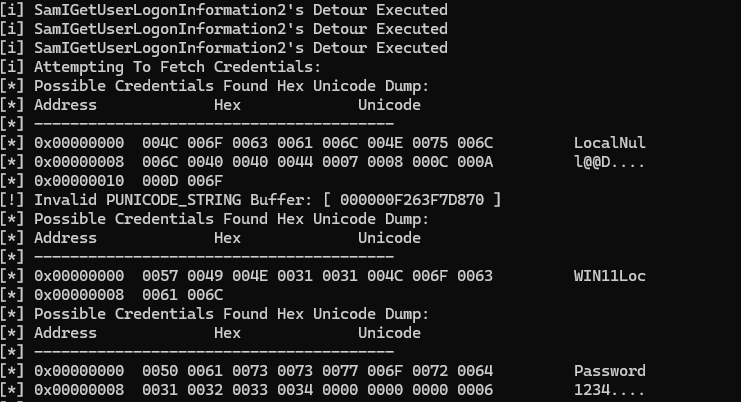
With some guidance from DebugPrivilege I've found a way to easily dump clear text implants even while they sleep. Bad day for sleep obfuscation 💤 blog.felixm.pw/rude_awakening…