
The Hacking Lab
@thehackinglab
Online Cyber Security Lab
ID: 835220414
https://www.hacking-lab.com/ 20-09-2012 09:58:50
964 Tweet
2,2K Followers
86 Following




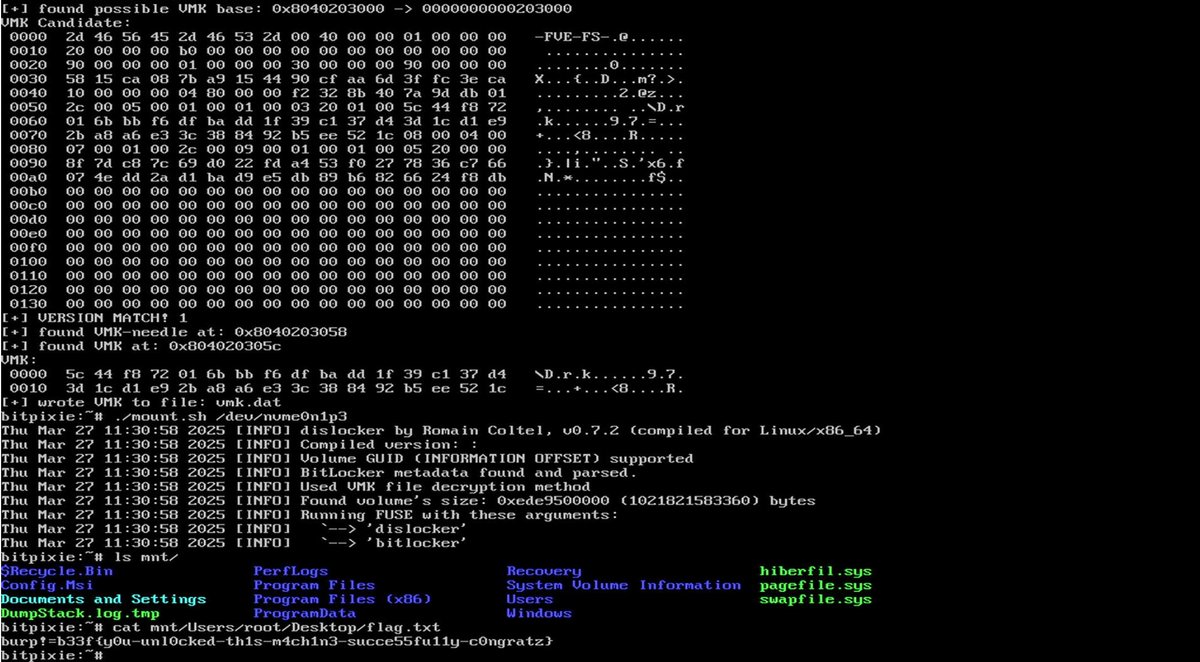
In his latest blog post, Marc Tanner Marc André Tanner shows how to bypass BitLocker using BitPixie (CVE-2023-21563) and signed Microsoft components only. Check out the blog post for a PoC and a demo. #BitLocker #redteam blog.compass-security.com/2025/05/bypass…



LLM-based vuln hunting just leveled up with xvulnhuntr - a fork of vulnhuntr with support for: C#, Java, Go. Read Nicolò Fornari's blog post and go grab the project on GitHub. blog.compass-security.com/2025/07/xvulnh…






We use James Kettle’s (James Kettle) Burp extension Collaborator Everywhere daily. Now our upgrades are in v2: customizable payloads, storage, visibility. Perfect for OOB bugs like SSRF. Find out more here: blog.compass-security.com/2025/09/collab… #AppSec #BurpSuite #Pentesting








Learn about a FortiProxy Domain Fronting Protection bypass discovered by our analyst @[email protected] . Details in the advisory: compass-security.com/en/news/detail… Curious how web filters are evaded? Read his blog series: blog.compass-security.com/2025/03/bypass… #cve #pentest #bypass









