PortSwigger Research
@portswiggerres
Web security research from the team at @PortSwigger
ID: 1177545689460592640
https://portswigger.net/research 27-09-2019 11:29:18
973 Tweet
103,103K Takipçi
7 Takip Edilen


The recording of my recent AMA with the Burp Suite Discord community has just landed on YouTube! 40 minutes of unscripted Q&A on security research, AI, and Burp Suite: youtu.be/mgmUZ9odkvU



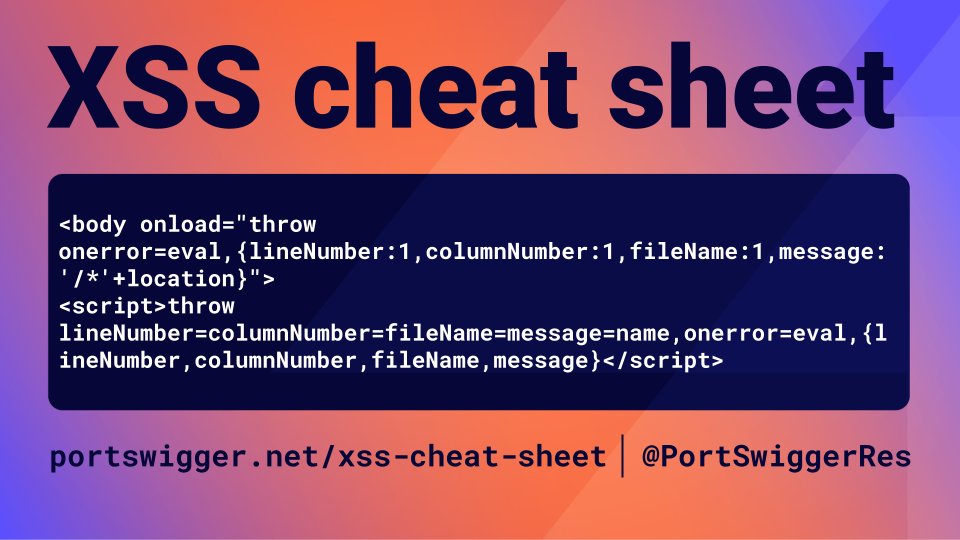
Epic Firefox XSS vectors by Masato Kinugawa. Now available on our XSS cheat sheet including variants found by me. Link to vectors👇




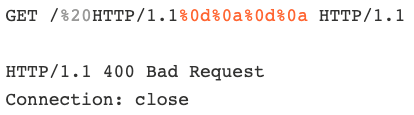
"Funky chunks: abusing ambiguous chunk line terminators for request smuggling" - quality research by Jeppe Weikop! Also thankfully it doesn't overlap with my upcoming presentation 😅 w4ke.info/2025/06/18/fun…



When HTTP/1.1 Must Die lands at DEFCON we’ll publish a Web Security Academy lab with a new class of desync attack. One week later, I’ll livestream the solution on air with Off By One Security! You’re invited :) youtube.com/live/B7p8dIB7b…

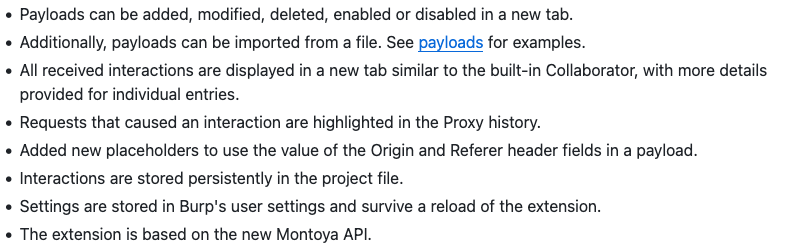
We've just released a massive update to Collaborator Everywhere! This is a complete rewrite by Compass Security which adds loads of features including in-tool payload customization. Massive thanks to Compass for this epic project takeover. Check out the new features:








🚨 New Web Security Academy lab: 0.CL request smuggling Based on HTTP/1 Must Die, presented at #BHUSA Solve it, write it up, and you could: ✅ Get featured on the PortSwigger blog 🎁 Win a 1-year Burp Suite Pro license 🧢 Score some swag portswigger.net/web-security/r…