David Ledbetter
@ledtech3
System Repair, Windows system tools ,Security research.
IDA Challenged.
ID: 4579549601
https://pcsxcetrasupport3.wordpress.com/ 23-12-2015 15:03:49
31,31K Tweet
3,3K Takipçi
291 Takip Edilen






🏭 In May, SentinelLabs has investigated a supply-chain attack against the Rust development community that we refer to as ‘CrateDepression’. Learn more sentinelone.com/labs/cratedepr… SentinelLabs #infosec #cybersecurity #supplychain


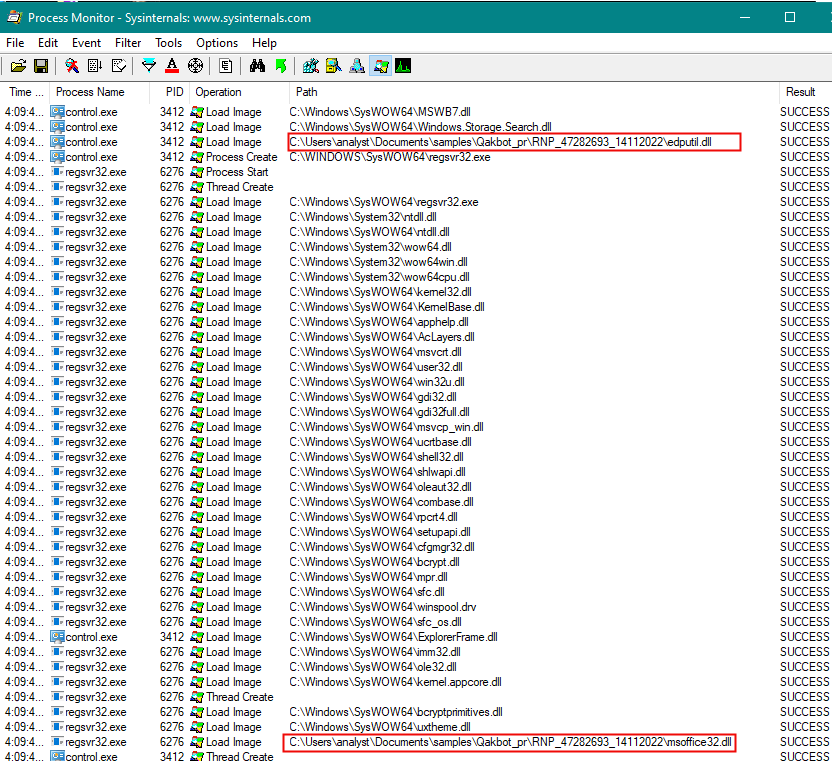
Also an few #Emotet today. James proxylife Ne0ne | Igal 0n3 Cryptolaemus Joe Roosen All of the sheets are visible in this one and each is the same as sheet 1? Did Ivan do a drunk again? tria.ge/221107-xd7raac…












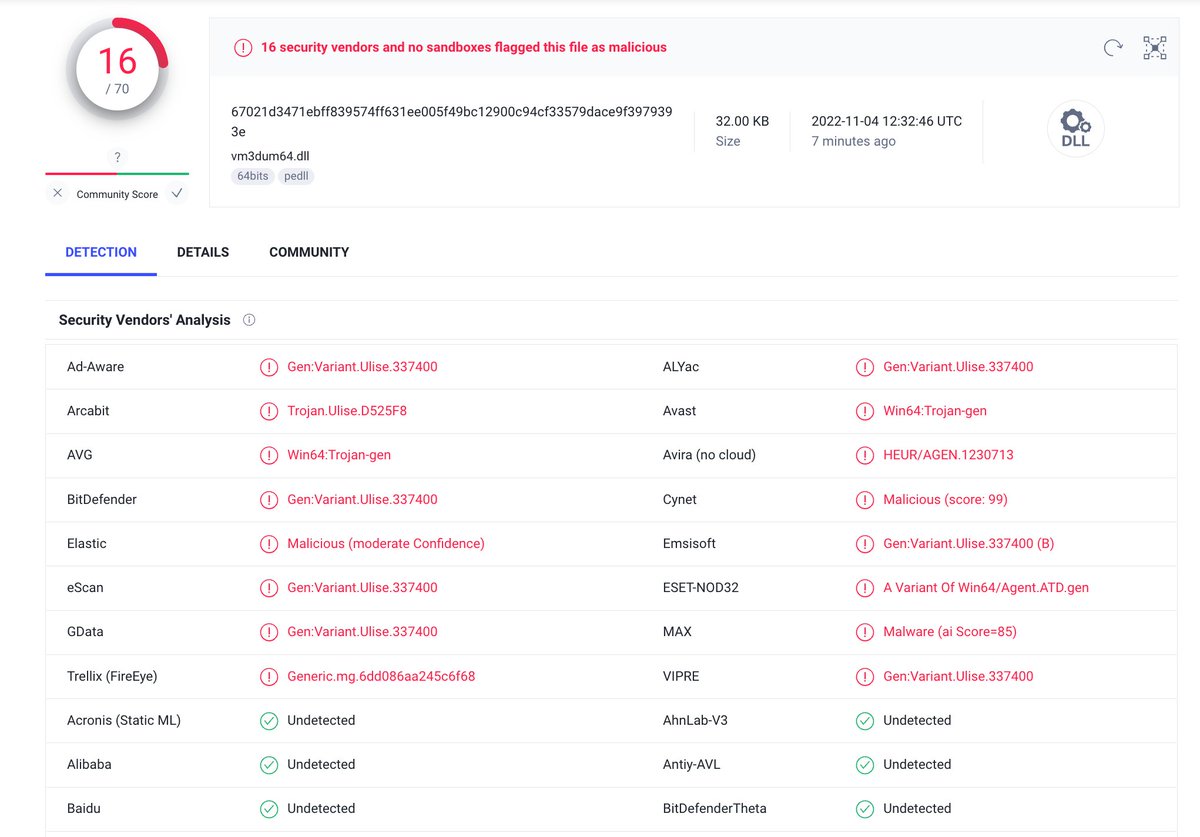
![Filescan.io (@filescan_itsec) on Twitter photo [UPDATE] Here's a #maldoc with (still) live C2 that is quite evasive and shows the detection capability ex-OSINT. Download URL has a "ski" gTLD. Download the sample with a user account (it's not on VT) for free: filescan.io/uploads/636586… // #DFIR #malware #analysis [UPDATE] Here's a #maldoc with (still) live C2 that is quite evasive and shows the detection capability ex-OSINT. Download URL has a "ski" gTLD. Download the sample with a user account (it's not on VT) for free: filescan.io/uploads/636586… // #DFIR #malware #analysis](https://pbs.twimg.com/media/Fgwe7YsXkAAFjh1.png)