Kevin Perlow
@KevinPerlow
RE and CTI. Feel free to take a gander at my past presentations: https://t.co/iWUyecnxC6
ID:245055616
30-01-2011 19:38:30
138 Tweets
1,3K Followers
19 Following



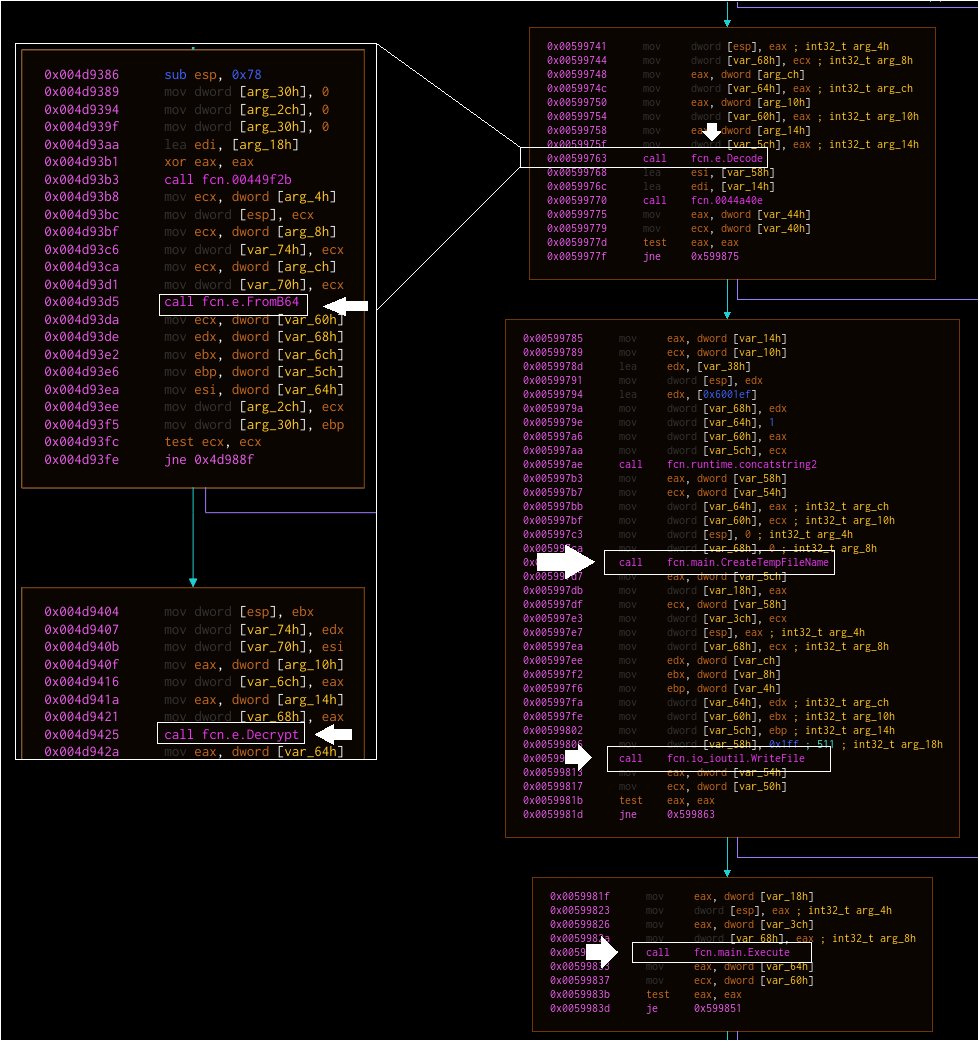
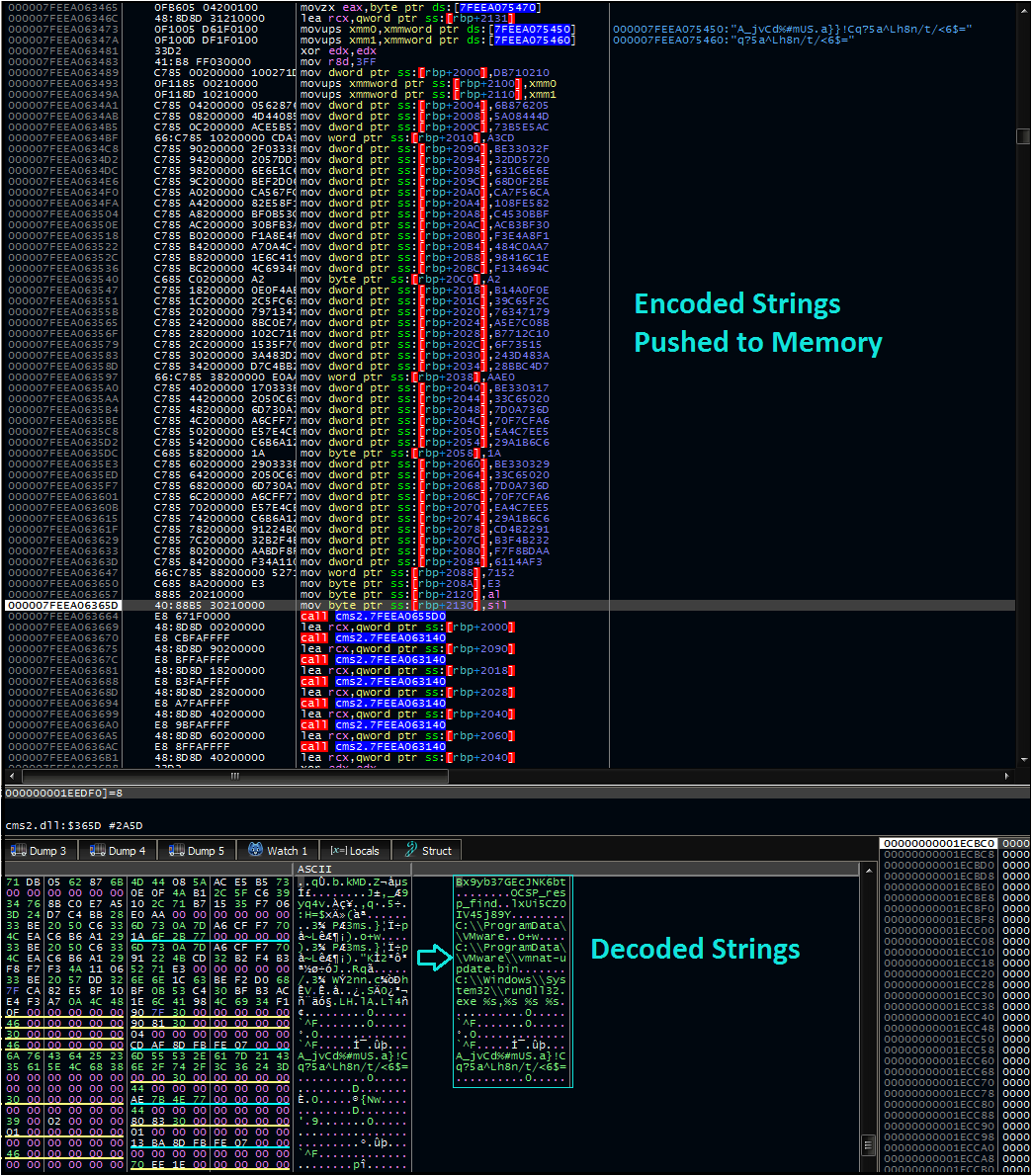
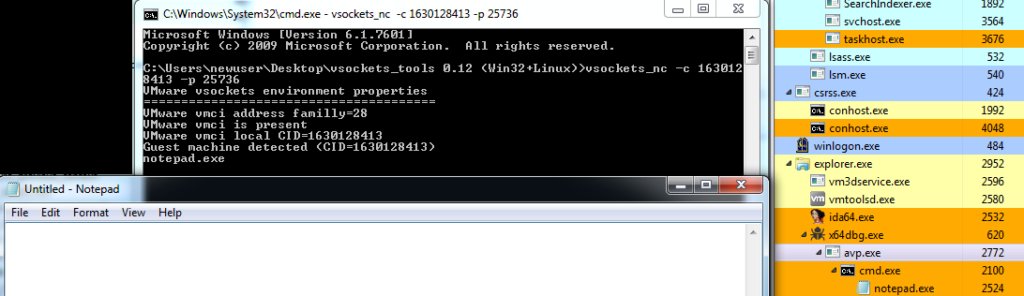
Some notes and testing on (what I think is) a #VIRTUALGATE sample, following Mandiant's ESXI report:
norfolkinfosec.com/some-notes-on-…
MD5 3c7316012cba3bbfa8a95d7277cda873
-Opens VMCI listener on 25736
-Listens
-Runs what it receives via cmd
Post shows RE + how to test it. Cool malware

.ATT&CK v9 is out!!! A big shout out 🙌 to Patrick Wardle, Thomas Reed, Cody Thomas , and Chris [email protected] for helping us update changes to macOS🍎. There is more to come...but let's take a moment to appreciate my new favorite gif, which summarizes this release perfectly!

Also, my personal favorite talk from the conference was from James Pavur - A fantastic presentation on eavesdropping on satellite internet conversations.
youtu.be/d5Sbwlu6f8o
No technical satellite knowledge required (I barely know how they get up there)





Interesting possible relationship between #TinyPOS + #ProLocker
norfolkinfosec.com/tinypos-and-pr…
I lean towards, 'would makes sense if it's the same group,' but far from definitive. Was trying to find infrastructure.
Drunk Binary (for the hashes)
Florian Roth (for code segments and YARA)




My April Fool's present: Incident Response, the 'Bored' Game. Please verb responsibly.
Drunk Binary Vitali Kremez mark Jacob Denne
*Might be worth playing with blank squares and a 'dungeon master' who tracks the rolls and reads the squares.


Golang walkthrough - A look back at some old (2017) #Dragonfly / #DYMALLOY 'Goodor' using newer tools:
norfolkinfosec.com/a-new-look-at-…
Always how Goodor *actually* worked. Redress from Joakim Kennedy helps answer that question.
CC Drunk Binary