Jb Aviat
@jbaviat
Democratizing security at @datadoghq. Former @SqreenIO CTO & co-founder. Former Apple security team. Kind.
ID: 403004157
https://datadoghq.com 01-11-2011 21:52:53
1,1K Tweet
1,1K Followers
440 Following


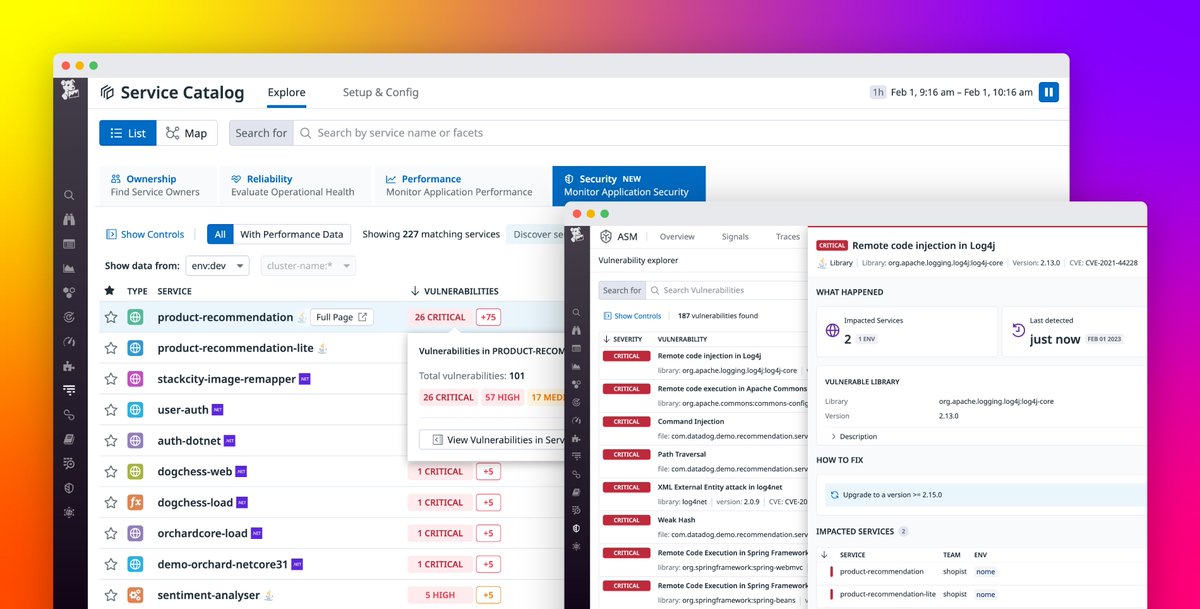
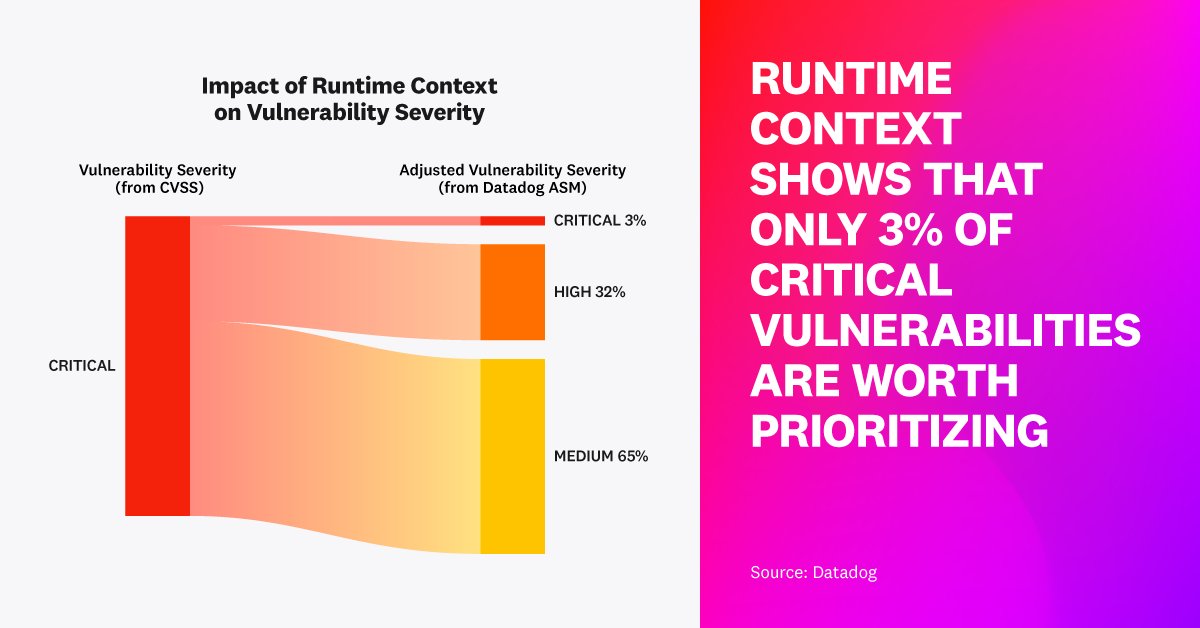
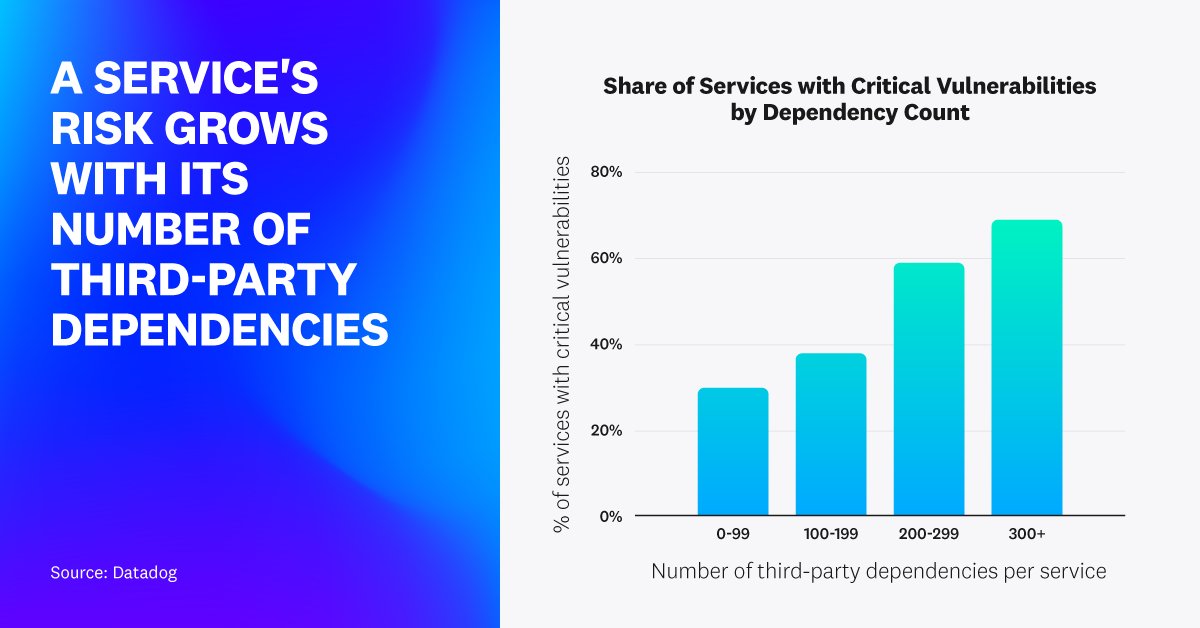
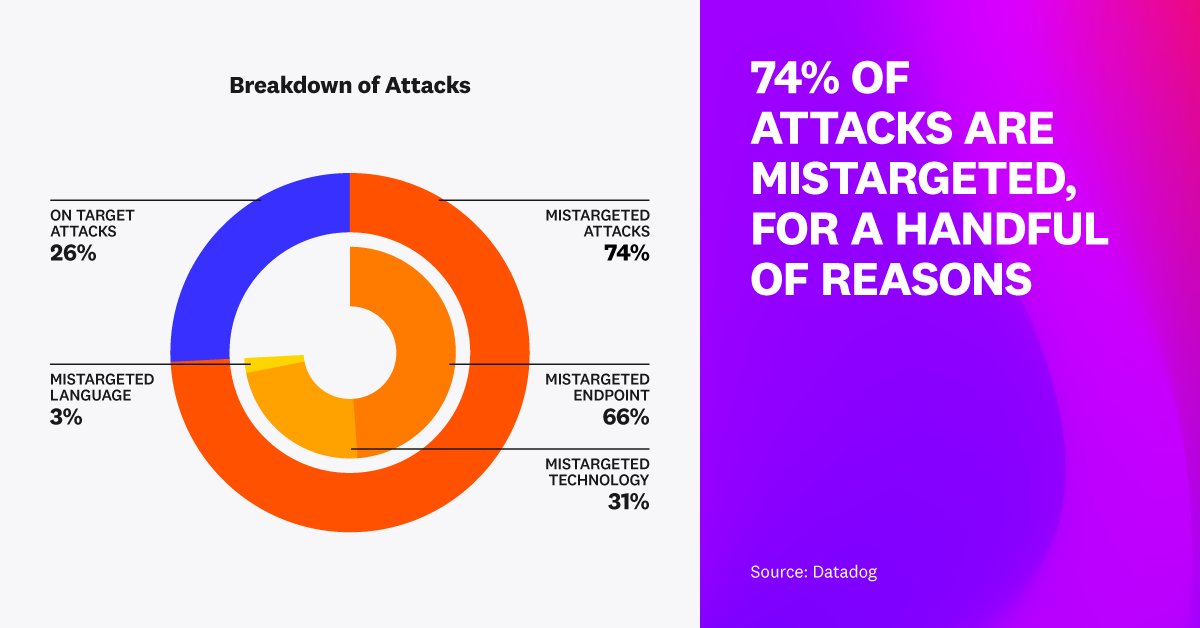
We just released Datadog, Inc. “State of Application Security” report! Discover how Datadog in-app context helps to better prioritize vulnerabilities (reducing count of critical by 97%) or to drastically increase signal to noise ratio (proving that 74% attacks are harmless)!





I had an insightful discussion last week with Sacha Faust about security inventories. They enable engineering accountability from a security standpoint. I'll release it this week, stay tuned!

Cloud Security Lounge #3 is out! I discuss security inventories with Sacha Faust, director of security engineering @Grammarly. He open sourced one of the first Lyft with alex chantavy. Cloud and graph databases made them possible, spread security accountability made them useful!

Tune in to our newest episode of Cloud Security Lounge! This week, we are joined by Michael Dawson and exploring security in the Node.js ecosystem: dtdg.co/3C3pbtW #appsec #nodejs #cloudsecurity

Thanks Chris Romeo and the The Application Security Podcast - always a pleasure to chat with security experts about this: we've been surprised by the same data points! Hint: 3/4 of attacks are mistargeted!


Curious about the most common ways for attackers to initiate cloud breaches? Chris Farris (@[email protected]) chats with us about the latest trends in cloud security, especially those reflected at #fwdcloudsec! Tune in here: youtube.com/watch?v=swoT2t…

We interviewed Chris Farris (@[email protected]) days before fwd:cloudsec about cloud security. Our key takeaways: The lines are blurring: beyond infra security towards business logic. Chris best cloud security advice: get rid of your access keys! Concrete case: the LastPass breach. tune in here 👇

CVSS powers any vulnerability and yet most people don't get it. The version 4 of CVSS now makes it more intelligible! We discussed it with Matthew Coles, along with other ways to spot what vulnerabilities really matter to your context using CVSS.

Another episode of the Datadog, Inc. Cloud Security Lounge with Matthew Coles, Izar Tarandach and Jb Aviat . No BS, no hidden agenda, just great folks and great security chats! youtube.com/watch?v=AC6x9J…

This was a lot of fun! Tune in to this wonderful conversation with Jb Aviat and Izar Tarandach on the Datadog, Inc. podcast. We chatted about all things LLMs, security, Gandalf, and everything in between.