Nick Carr
@ItsReallyNick
Lead, Cyber Crime Intelligence @Microsoft ☠🏛️ Former Incident Response + Threat Research @Mandiant 🦅 Former Chief Technical Analyst @CISAgov 🛡️
ID:73195179
http://linkedin.com/in/itsreallynick 10-09-2009 19:15:18
12,1K Tweets
38,4K Followers
3,5K Following




It's LIVE - Permiso Security's #CloudConsoleCartographer has now been released by Andi Ahmeti & myself at Black Hat #BHASIA here in beautiful Singapore.
Andi Ahmeti - Gëzuar miku! 1st conference in the bag :)
Tool: github.com/Permiso-io-too…
Blog: permiso.io/blog/introduci…





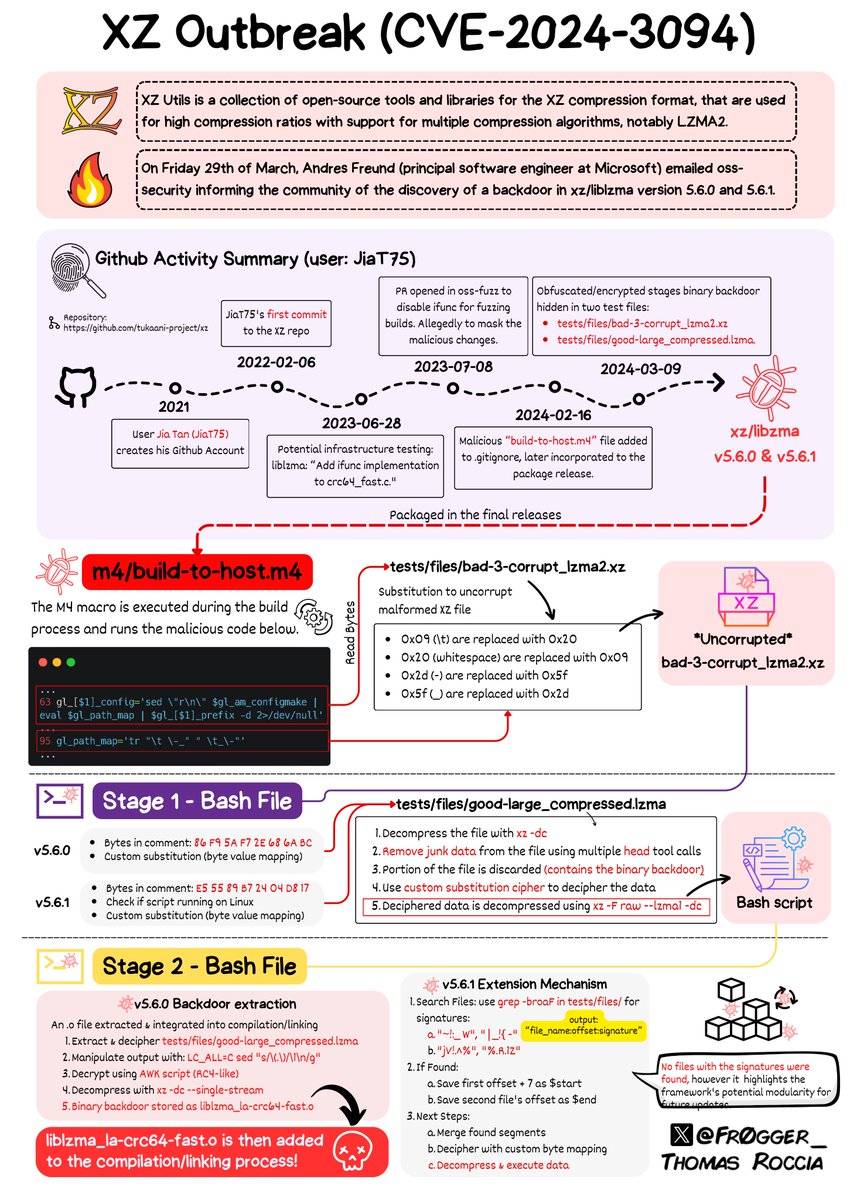
Binni Shah FWIW, I didn't actually start looking due to the 500ms - I started looking when I saw failing ssh logins (by the usual automated attempts trying random user/password combinations) using a substantial amount of CPU. Only after that I noticed the slower logins.