Matt Biedronski
@gonski47
ID: 1642567481117081601
02-04-2023 16:40:01
193 Tweet
247 Takipçi
199 Takip Edilen











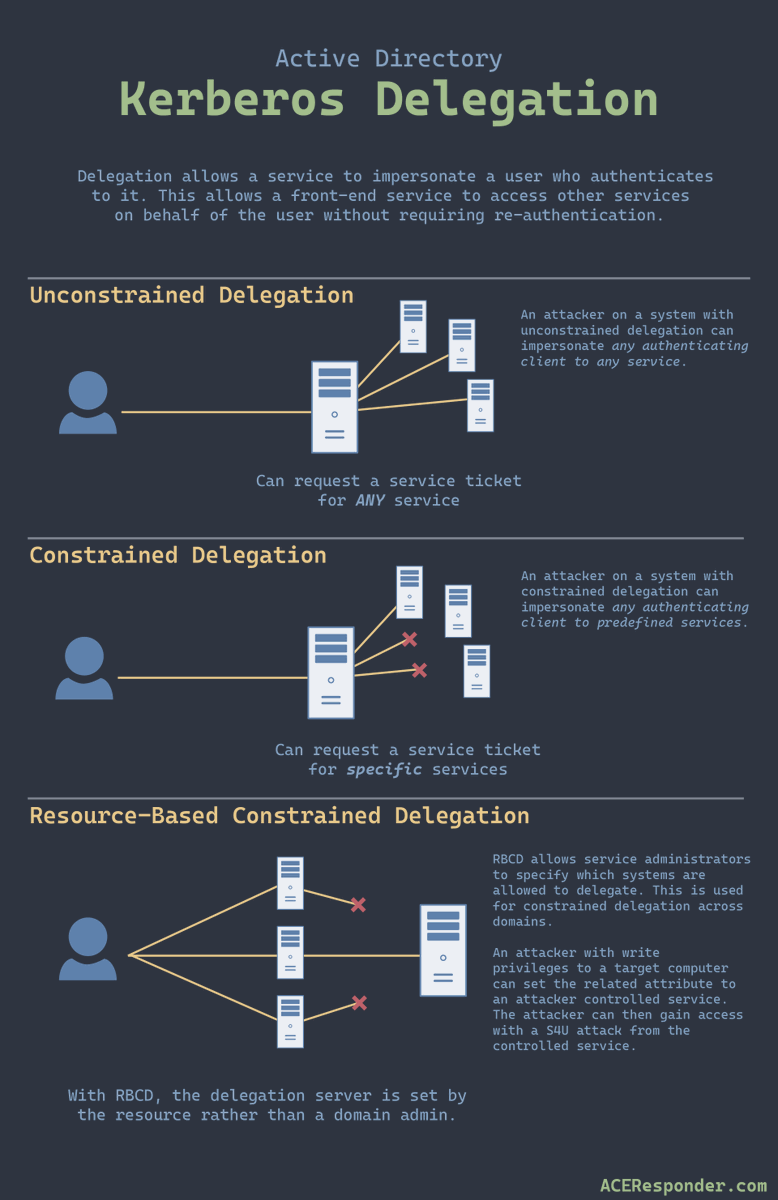
CypherHound github.com/fin3ss3g0d/cyp… now supports ALL traversable AD edges in BloodHound CE! There have been a lot of traversable edges added by SpecterOps over the last year, my project is providing prebuilt queries for you to use with the latest edges! Don't miss out!