
APTzatziki
@gekarantzas
George Karantzas. - Est. 2001. - BSc Student@UniPi. - Sr. Dev@Morphisec - Opinions are my own.
ID: 1231778705271410689
24-02-2020 03:11:53
1,1K Tweet
1,1K Followers
2,2K Following


New 0 day dropped: jhftss.github.io/Parallels-0-da… Conclusion: 1. Don’t trust Trend Zero Day Initiative , they are too late to handle our reports. One of my reports was submitted in 2024 Jan, but it is still not disclosed to the vendor. No reply from the ZDI yet! 2. Don’t trust the Parallels security!


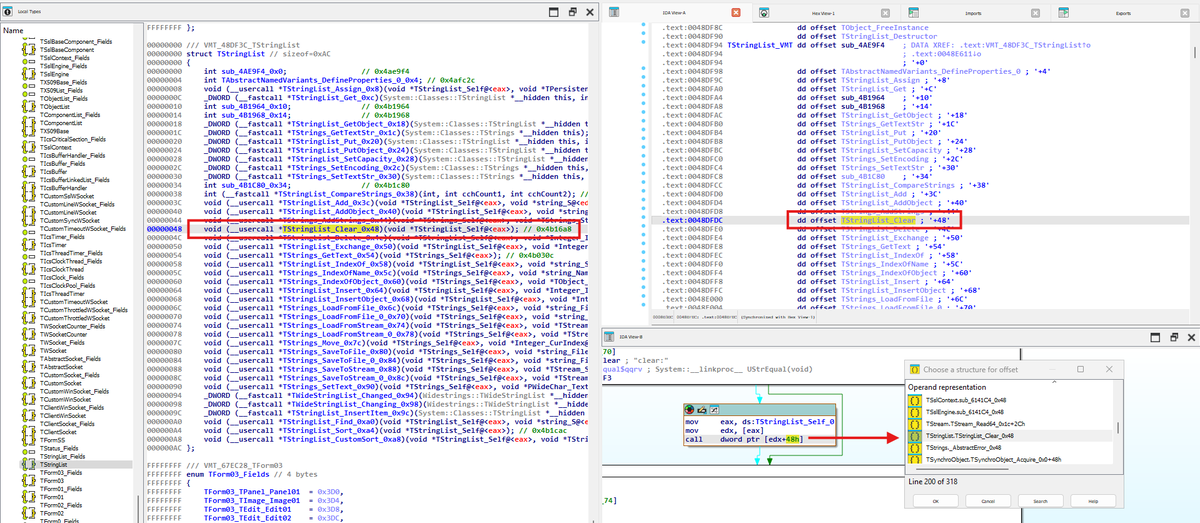
#ESETresearch has released DelphiHelper, a plugin for #IDAPro that aids in analyzing Delphi binaries. Check it out on ESET’s GitHub: github.com/eset/DelphiHel…. Proud to be recognized among the notable submissions of the 2024 Hex-Rays SA Plugin Contest: hex-rays.com/blog/2024-plug…

Chrome Browser Exploitation: from zero to heap sandbox escape by matteo malvica ⭕ youtube.com/watch?v=RL2po1…








Dug into Riot Vanguard's kernel driver's dispatch table hooks. The article took an unexpected turn half way through, as I found some not yet documented stuff, such as the complete list of system calls hooked by the driver. Article link: archie-osu.github.io/2025/04/11/van…


Thread Execution Hijacking is one of the well-known methods that can be used to run implanted code. In this blog we introduce a new injection method, that is based on this classic technique, but much stealthier - Waiting Thread Hijacking. Read More : research.checkpoint.com/2025/waiting-t…






