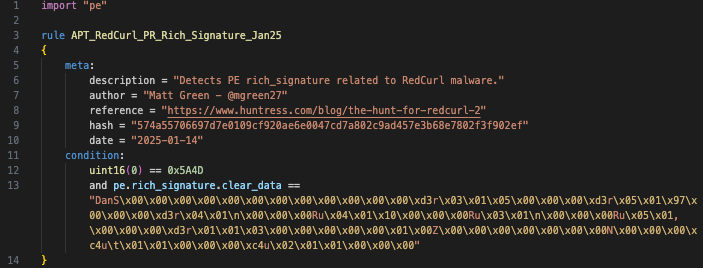
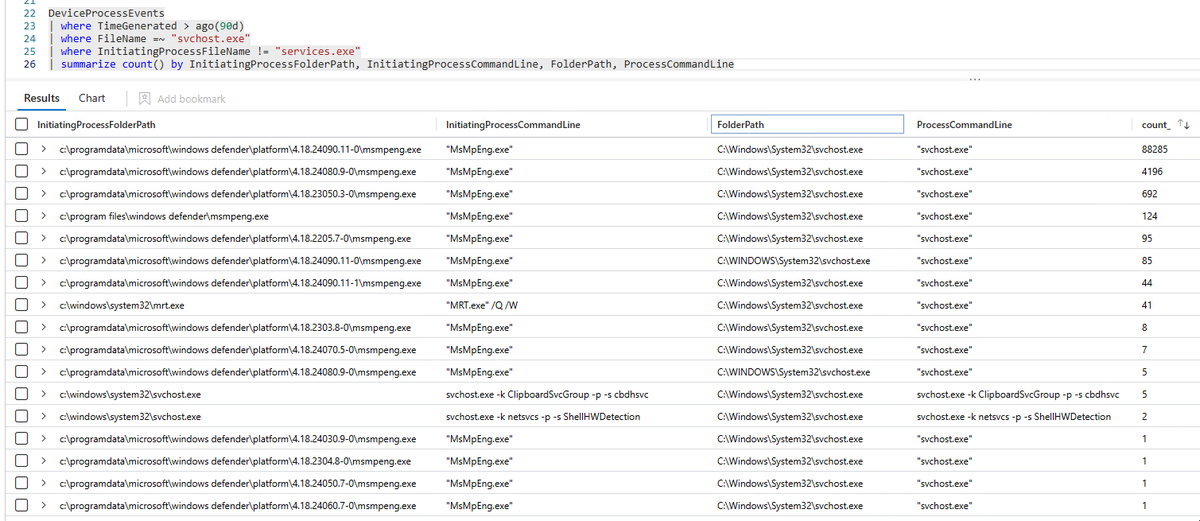
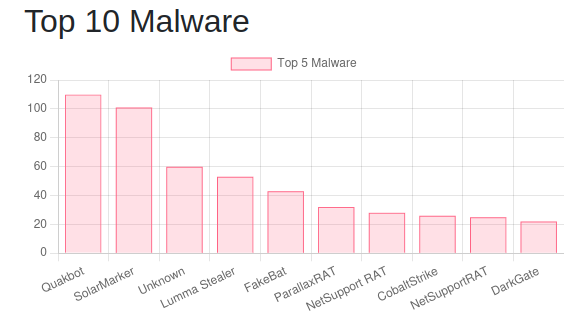
Tony Lambert
@forensicitguy
Recovering sysadmin that now chases adversaries instead of uptime. Sr Malware Analyst @redcanary
ID: 417640257
https://forensicitguy.github.io 21-11-2011 06:06:13
3,3K Tweet
5,5K Followers
1,1K Following



Following the release of volatility 2.11, VolWeb 3.13.3 is now available including most of the new plugins and a bunch of new features. github.com/k1nd0ne/VolWeb…


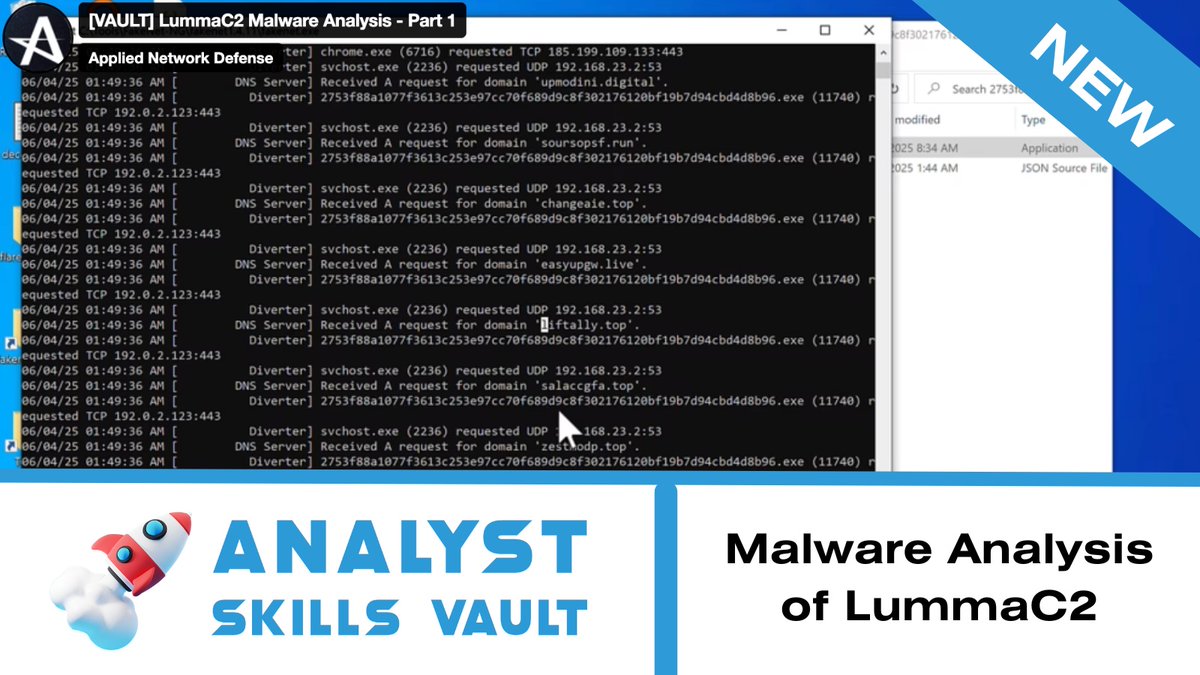
In our latest Analyst Skills Vault lesson, Tony Lambert breaks down how to analyze and decode the Meduza stealer malware's network communication traffic.


A cool new #threatdetection blog by Phil Hagen and Tony Lambert which uses #synapse to analyze network tunneling behavior of a few malware families! 🎉 redcanary.com/blog/threat-de…





Threat Detection Highlights Webinar series – April Edition: This month’s session is extra special. zoom.us/webinar/regist… We're excited to welcome Tony Lambert Tony Lambert , Senior Malware Analyst at Red Canary, known for his sharp research and impactful community



In our latest Analyst Skills Vault lesson, Tony Lambert walks through a dynamic analysis of the Meduza Stealer Malware, focusing on host-based artifacts.






Not only is Huntress a generous supporter of our Foundation, they also consistently publish top-notch research on emerging macOS threats 🤩 Their latest (by alden & Stuart Ashenbrenner 🇺🇸 🇨🇦): "Feeling Blue(Noroff): Inside a Sophisticated DPRK Web3 Intrusion": huntress.com/blog/inside-bl…