Fabius
@fabiusartrel
🎭
ID: 2565666116
13-06-2014 17:41:19
259 Tweet
510 Takipçi
438 Takip Edilen

Maybe Miroslav Stampar would enjoy this? A sqlmap tamper script for exploiting a multi-step 2nd order sqli in moodle muffsec.com/blog/moodle-2n…

The following non-malicious request can be used to test susceptibility to the Spring Framework 0day RCE. An HTTP 400 return code indicates vulnerability. $ curl host:port/path?class.module.classLoader.URLs%5B0%5D=0 #SpringShell #Spring4Shell #infosec







New blogpost by b33f | 🇺🇦✊ and I! Patch Tuesday -> Exploit Wednesday: Pwning Windows afd.sys in 24 Hours. We reverse engineer a bug + write an exploit using a cool new primitive. We also find out that it's been exploited in the wild (previously unknown). securityintelligence.com/posts/patch-tu…


We've been able to trigger CVE-2023-21554 AKA #QueueJumper, a recently patched RCE in Microsoft’s Message Queueing Service reported by Check Point Research. We can confirm it appears exploitable. IOCs and more: randori.com/blog/vulnerabi…

In collaboration with Fabius and Aaron Portnoy we conducted a post mortem of the QueueJumper MSMQ RCE patch. We do an in depth RCA, identify variants, create exploit primitives, evaluate exploitability, and make some interesting new discoveries! securityintelligence.com/posts/msmq-que…



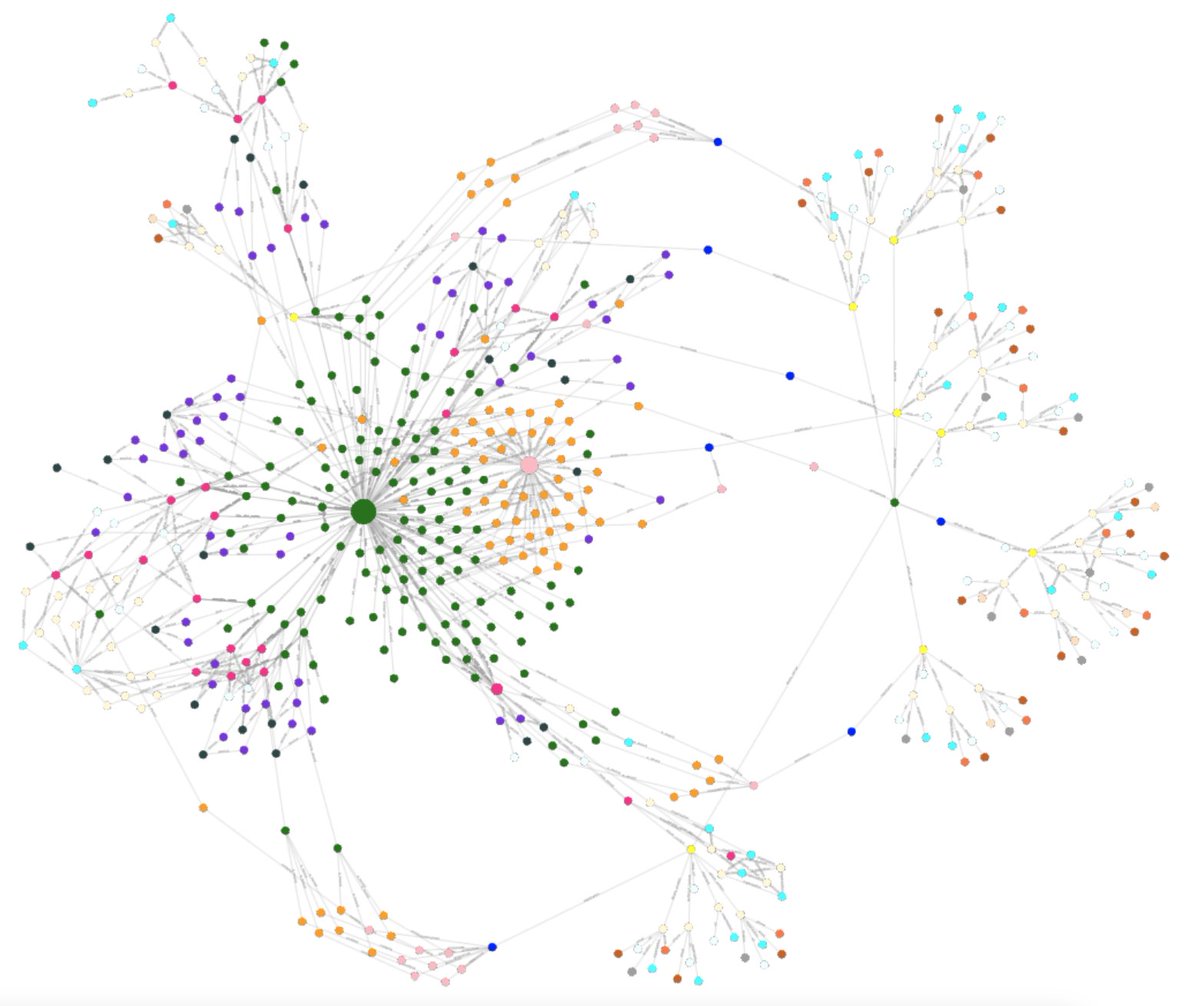
The OWASP Amass project paints a more complete picture of externally exposed attack surfaces these days! The first official release of our #opensource platform will be available soon. Stay tuned! #osint #recon #security #infosec #bugbounty OWASP® Foundation

Exciting news! I’m starting X-Force’s new offensive research team (XOR) and hiring a security researcher. Want to work with researchers (like b33f | 🇺🇦✊ and I) to find bugs, exploit popular targets, and share your work? Apply for this unique (remote) role 😊careers.ibm.com/job/21219320/s…