
Forrest Kasler
@fkasler
Climber, Penetration Tester, Code Junkie, Malware Enthusiast @specterops
ID: 45474010
08-06-2009 01:49:16
188 Tweet
512 Takipçi
390 Takip Edilen


Blending in is the key to staying 'stealthy' in network traffic. In this week's installment of the #Phishing School blog series, Forrest Kasler details how you can hide your C2 implant w/ stealthy callback channels. Read more ⤵️ ghst.ly/4ciTBrS

You never know when some Windows legacy knowledge will help you succeed in an engagement. In our new #blog, Oddvar Moe reveals a new #phishing technique implemented by creating an empty file with the .udl extension. Read it now! hubs.la/Q02Lqb4s0

New blog post just dropped! 😎 In this installment of our blog series on Identity-Driven Offensive Tradecraft, Elad Shamir shares a framework he developed for discovering known & unknown Attack Paths. posts.specterops.io/navigating-the…



Ghostwriter 💜 Tool Integration! Ghostwriter v3.0.0 features a powerful GraphQL API, making tool integration a breeze. Alexander Sou's latest blog post showcases the API's capabilities using our Operation Log Generator. Learn more ⤵️ghst.ly/4dCohWE





I and Fred Heiding published a human study on AI spear phishing: We use AI agents built from GPT-4o and Claude 3.5 Sonnet to search the web for available information on a target and use this for highly personalized phishing messages. achieved click-through rates above 50%




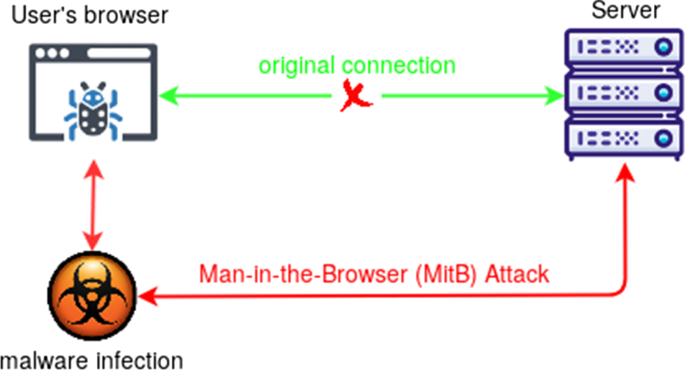
cuddlephish : Weaponized multi-user browser-in-the-middle (BitM) for penetration testers : github.com/fkasler/cuddle… Details : link.springer.com/article/10.100… credits Forrest Kasler




MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. Chris Thompson unpacks this new feature in his blog post. 👇 ghst.ly/4leRFFn

