F5
@F5
a force for cybersecurity frontliners.
for the people they protect.
for some well-earned peace.
ID:15136500
https://www.F5.com 16-06-2008 17:42:12
31,8K Tweets
45,3K Followers
9,5K Following

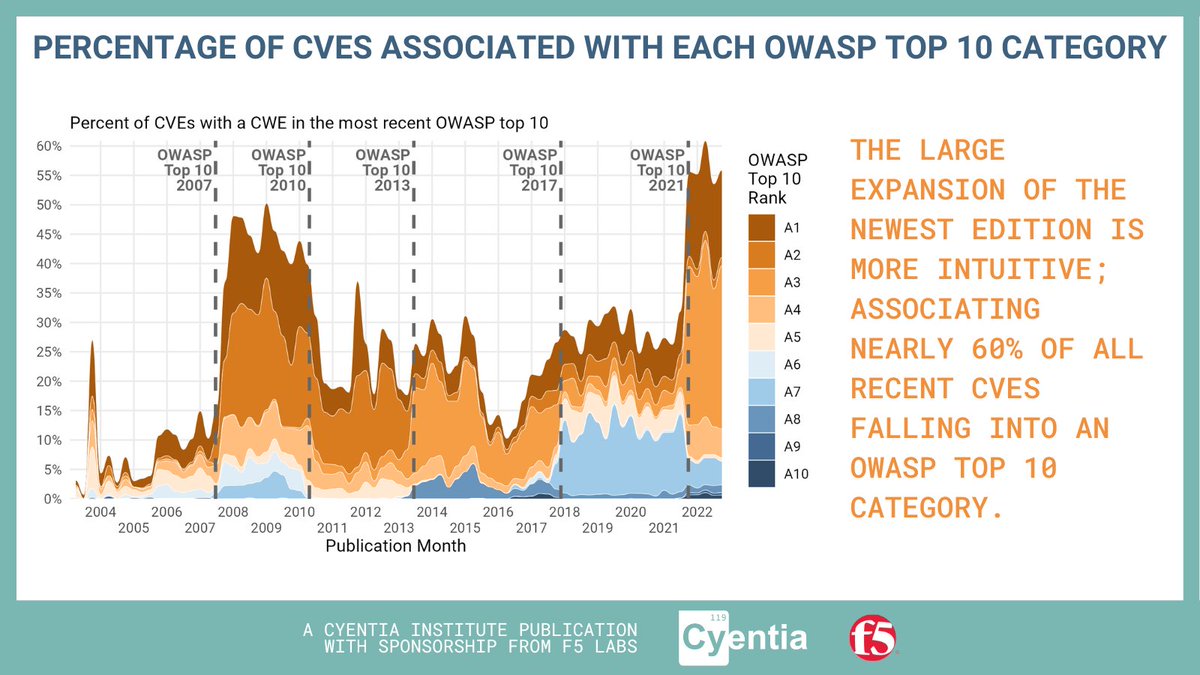
In the latest Report from Cyentia & F5 𝑇ℎ𝑒 𝐸𝑣𝑜𝑙𝑣𝑖𝑛𝑔 𝐶𝑉𝐸 𝐿𝑎𝑛𝑑𝑠𝑐𝑎𝑝𝑒 see which category in the Open Web Application Security Project Top 10 comprises the highest CVEs in each era: f5.com/labs/articles/… #vulnerabilitymanagement #vulnerabilities #cybersecurity

While technology continues to improve at pace, individuals are often the weakest link in the cybersecurity chain. We caught up with Mark T. Hofmann, guest speaker at #AppWorld2024 in Berlin, to find out how we can all become 'human firewalls' to stay safe out there 🔐





In our latest report - sponsored by F5 Labs - we take a step back and examine the universe of vulnerabilities & how it’s changed in the last 20 years. f5.com/labs/articles/… #vulnerabilitymanagement #vulnerabilities #cybersecurity


Learn how to assemble security for APIs across clouds. Sandy Carielli, Principal Analyst at @Forrester, joins F5 experts in an on-demand webinar about securing APIs in whatever architecture you have. #CyberSecurity go.f5.net/7ioh3571



There's no one-size-fits-all blueprint for #APISecurity , but that doesn't mean good security is shrouded in mystery. #Forrester breaks down key approaches and best practices in this report: go.f5.net/0g4qi19p