Aurélien Chalot
@defte_
Hacker, sysadmin and security researcher @OrangeCyberdef 💻
Calisthenic enthousiast 💪 and wannabe philosopher t.ly/9NPk0 📖
🔥 Hide&Sec 🔥
ID: 934863293625270273
https://blog.whiteflag.io 26-11-2017 19:15:52
1,1K Tweet
3,3K Followers
452 Following


Some weeks ago, TrustedSec has posted a really interesting blog post about the MDT shares, and credentials that can be found inside. But one question remained unanswered: where are they? I have tried to answer this question: hideandsec.sh/books/windows-…

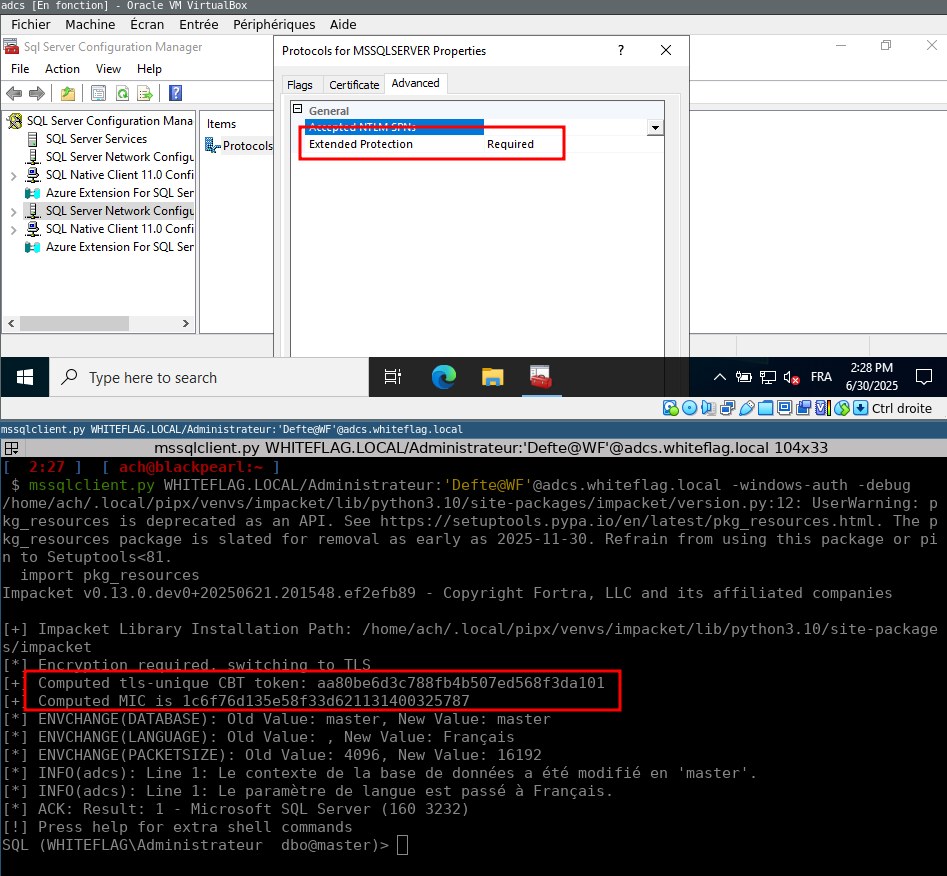
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (Aurélien Chalot), including instructions for reproducing the test environment yourself. (link below)