Chriss_0x01
@Chriss_0x01
Proud #EthicalHacker
#CyberCrime🖥️#Investigator
#BugBounty🏆#Hunter
#ThreatHunter
(#InfoSec & #CyberSec) #Expert🧑💼
&& _I_AM_: CEO @EthiclSecAgency 👀
ID:1639508251766136833
https://linktr.ee/chriss_0x01 25-03-2023 06:04:35
564 Tweets
903 Followers
3,8K Following


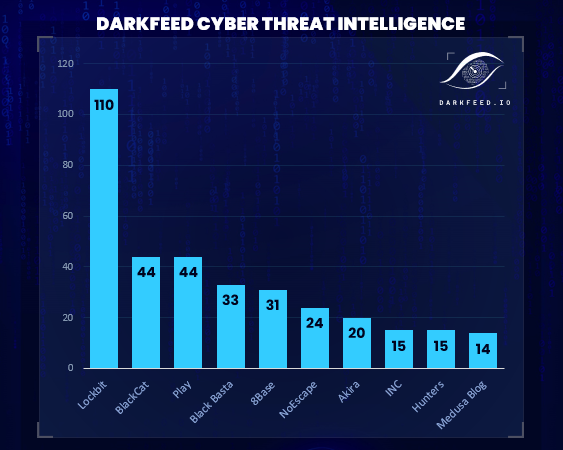
Top Active #Ransomware Groups November🎯
-Lockbit: 110 🔺
-BlackCat: 44 🔺
-Play: 44 🔺
-Black Basta: 33 🔺
-8Base: 31 🔺
-No Escape: 24 🔻
-Akira: 20 🔺
-INC: 15 🔺
-Hunters: 15 🆕
-Medusa Blog: 14 🔺
Total Victims: 467 💥
More Info: DARKFEED.IO

Hackers breach US govt agencies using Adobe ColdFusion exploit - Bill Toulas
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…




A weaponized #MicrosoftWord doc disguised as talking points to support Ukraine entry into #NATO was employed by pro-Russian APT #Storm -0978. In this article, we analyze the complex exploit chain used — and reveal #CVE202336584 — a new vulnerability. bit.ly/3QTuNze





FBI: Ransomware gangs hack casinos via 3rd party gaming vendors - Bill Toulas
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…






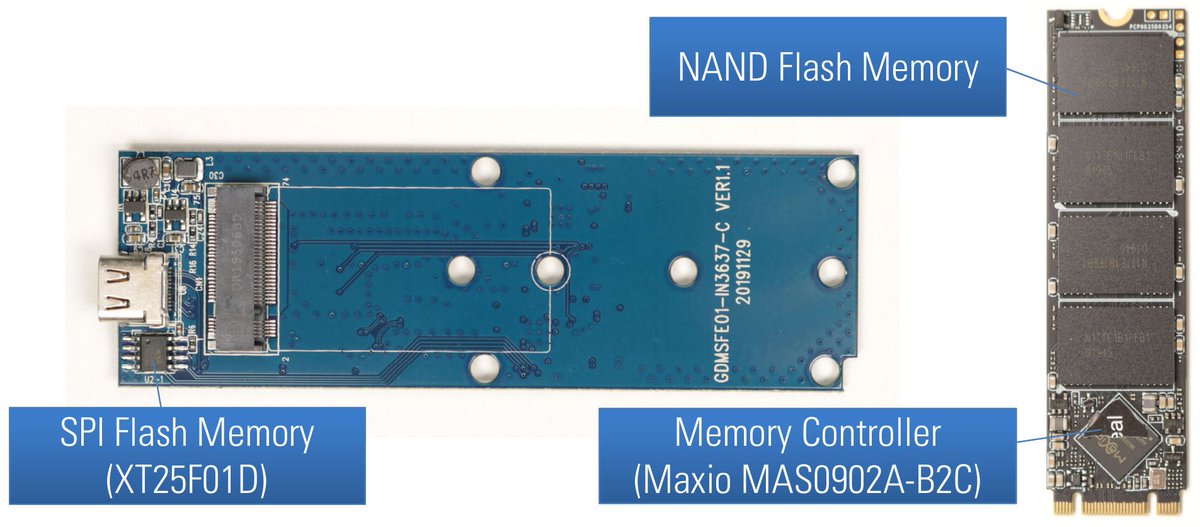
Reverse engineering of USB flash drives with AES hardware encryption
Credits Matthias Deeg
blog.syss.com/posts/hacking-…
blog.syss.com/posts/hacking-…
#embedded #hardware #infosec #cybersecurity



![crep1x (@crep1x) on Twitter photo 2023-12-04 11:34:43 New user-agent used by #Raccoon Stealer: 'MrBidenNeverKnow' (as mentioned by the Raccoon operator interviewed by @g0njxa) Recent C2 servers: 178.20.41.]15 193.233.132.]15 23.227.196.]198 37.49.230.]54 94.103.93.]70 New user-agent used by #Raccoon Stealer: 'MrBidenNeverKnow' (as mentioned by the Raccoon operator interviewed by @g0njxa) Recent C2 servers: 178.20.41.]15 193.233.132.]15 23.227.196.]198 37.49.230.]54 94.103.93.]70](https://pbs.twimg.com/media/GAgCSrSWUAErjMj.jpg)