BleepingComputer
@BleepinComputer
Breaking cybersecurity and technology news, guides, and tutorials that help you get the most from your computer. DMs are open, so send us those tips!
23-06-2009 16:41:34
31,3K Tweets
212,8K Followers
175 Following

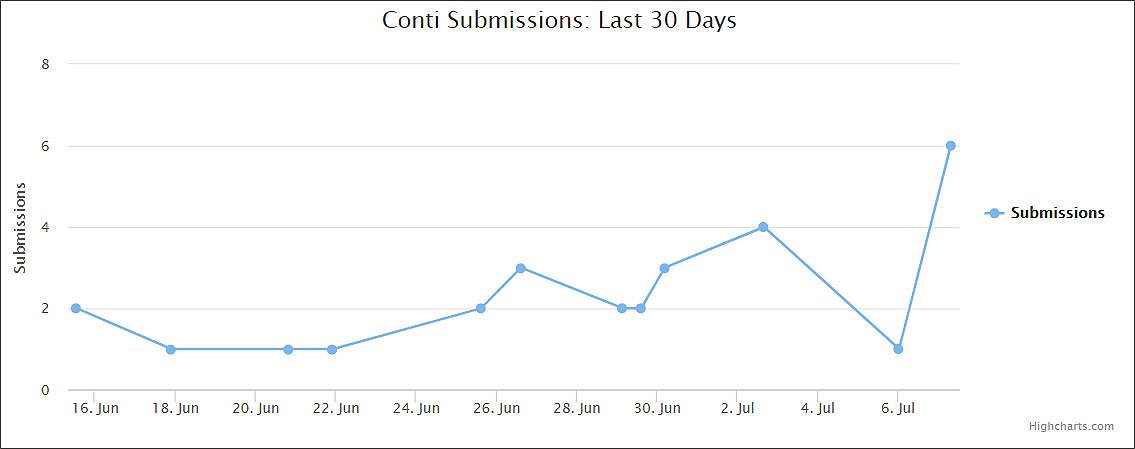
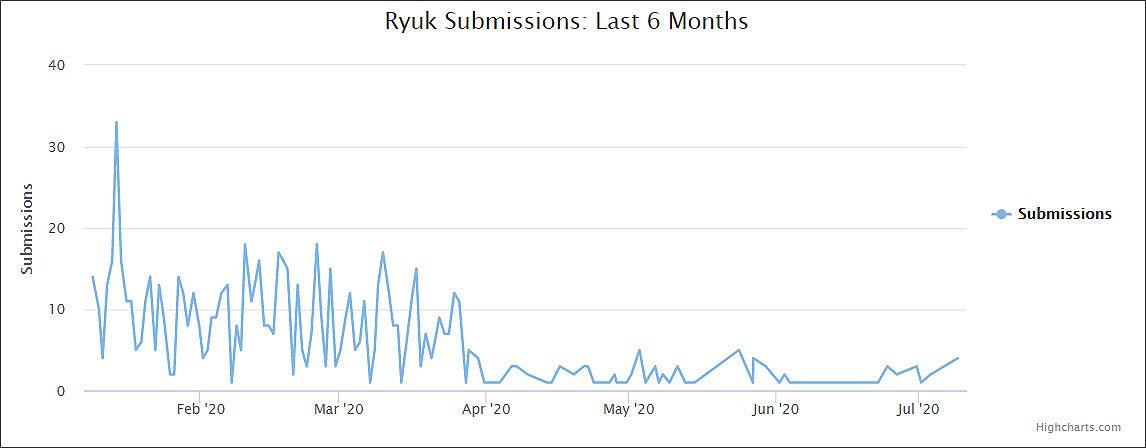
Conti ransomware shows signs of being a Ryuk successor - Lawrence Abrams
bleepingcomputer.com/news/security/…



Advanced Intel's Vitali Kremez has told BleepingComputer that Conti and Ryuk share similar code and that Conti is believed to be based off of Ryuk version 2.



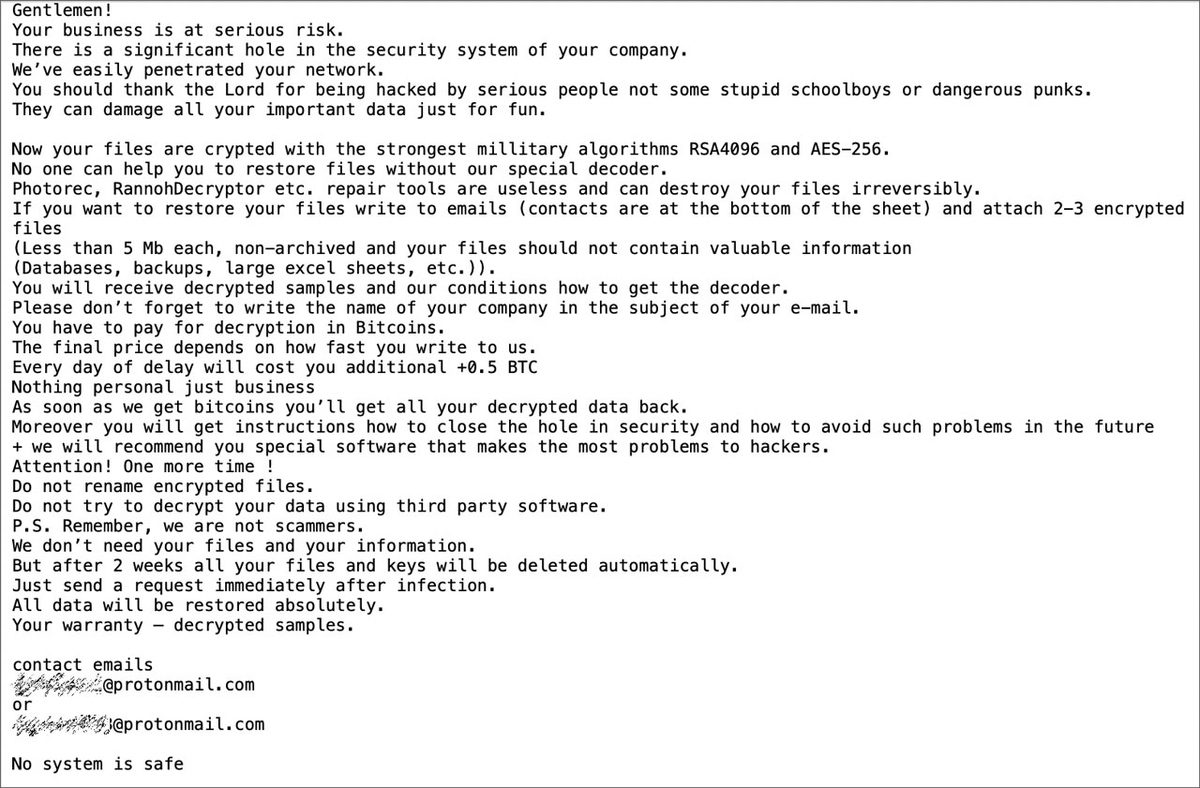
A new report by vmw_carbonblack adds further insight into how the Conti Ransomware operates.
carbonblack.com/blog/tau-threa…