Beta Systems
@betasystems
Supporting complex #IT systems for 40+ years. Experts in #SoftwareSolutions for #Automation, #ITSecurity, #IAM, #Compliance & #Mainframe.
ID: 41155930
http://www.betasystems.com 19-05-2009 16:57:10
817 Tweet
887 Takipçi
22 Takip Edilen















Wir sind dabei – it-sa - Home of IT Security 2025 in Nürnberg! Vom 7. bis 9. Oktober dreht sich auf Europas größter IT-Security-Messe alles um die neuesten Trends und Lösungen rund um Cybersecurity. 👉 Besuchen Sie bei uns am TeleTrusT-Gemeinschaftsstand „IT Security made in Germany“ –




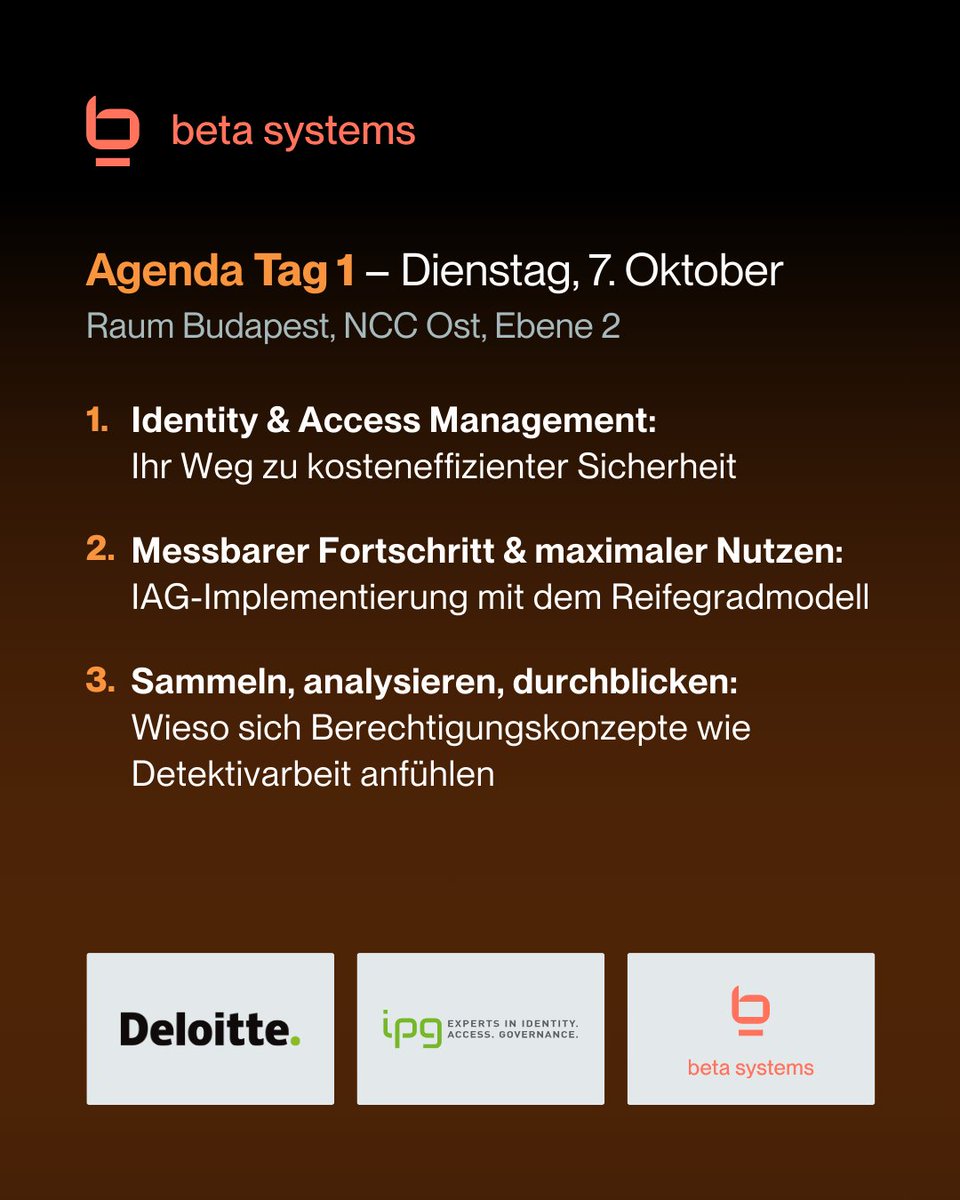
Neben unserem Messeauftritt auf der it-sa - Home of IT Security 2025 in Nürnberg haben wir auch ein spannendes Vortragsprogramm für Sie vorbereitet. 🎤 📍 Tag 1 – Dienstag, 7. Oktober | Raum Budapest, NCC Ost 🕜 14:30 – 15:05 „Identity & Access Management: Ihr Weg zu kosteneffizienter