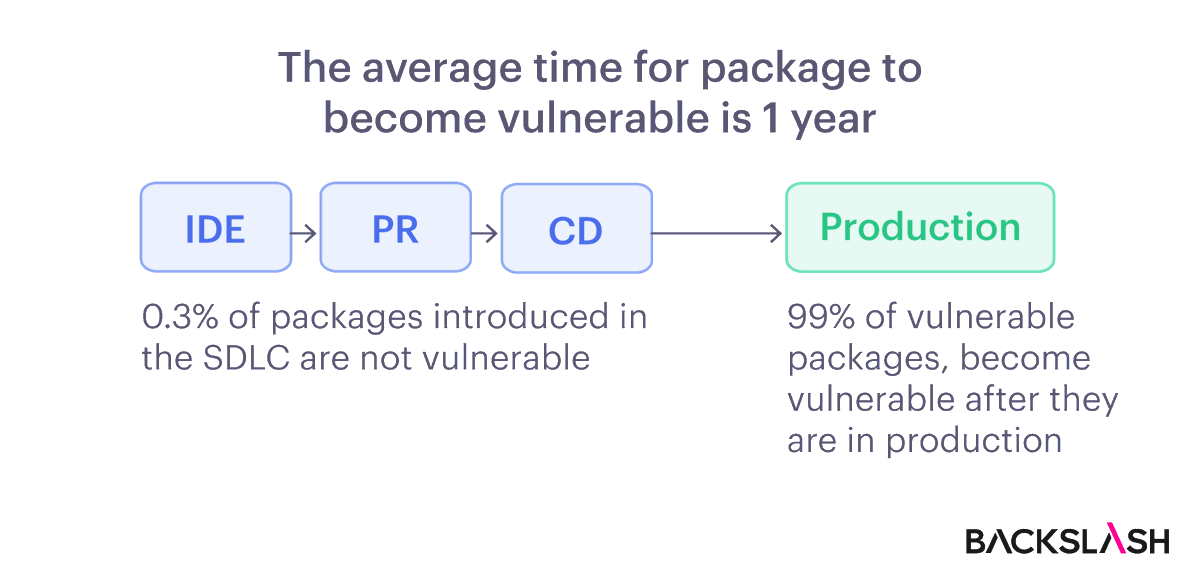
Backslash Security
@backslashsec
The first Cloud-Native #ApplicationSecurity solution for enterprise #AppSec teams to provide unified security and business context to cloud-native code risk.
ID: 1633728181839581191
http://backslash.security 09-03-2023 07:15:40
341 Tweet
93 Followers
36 Following




🏆🏆🏆 Backslash Security just won Most Innovative Application Security Solution at the 2024 InfoSec Innovator Awards by CyberDefenseMagazine ! We’re redefining AppSec from the ground up—not just “next-gen” but a truly fresh approach. See it in action: backslash.security/demo




Shahar Man, Backslash CEO, shares with The Hacker News his take on breathing fresh life into stagnant AppSec initiatives. Check it out here: thehackernews.com/expert-insight…












𝗙𝗿𝗲𝘀𝗵 𝗔𝗽𝗽𝗦𝗲𝗰 𝗶𝗱𝗲𝗮𝘀, 𝗮𝗻𝘆𝗼𝗻𝗲? Our CEO’s, Shahar Man latest The Hacker News article explores how to revitalize application security practices for today’s challenges. Dive in: thehackernews.com/expert-insight…