William MacArthur
@anti_expl0it
Director of Threat Research & Intelligence @InQuest: All views expressed are from my own brain. “Sharing is caring”
ID: 778763839974232065
https://InQuest.net 22-09-2016 01:12:23
173 Tweet
1,1K Takipçi
387 Takip Edilen

Seeing a lot of low score #Dridex docs right now... lots of various lures again. labs.inquest.net/dfi/sha256/bde… Joe Roosen William MacArthur James Nick Chalard


This is an odd one here with extreme uri length + directory traversal flavor a+ .dotm file suffix. AS37963 - ALIBABA (US) TECHNOLOGY. Note labs.inquest.net/dfi/sha256/167… James Joe Roosen William MacArthur dao ming si



We are sharing this visual for tracking threat actors/groups related to the current #ukraine conflict. The content was collected from various sources within the #infosec community. Special thanks to all involved. William MacArthur Nick Chalard J. A. Guerrero-Saade



An update our previous graphic we shared on the cyber-front of the #ukraine conflict. This content was collected from various sources and collaborations within the #infosec community. Special thanks to all involved. William MacArthur Nick Chalard J. A. Guerrero-Saade Jon Gorenflo 🇺🇦🌻


#Hancitor run looks like using Efax Lure - Password is 44 labs.inquest.net/dfi/sha256/3a2… James William MacArthur Cryptolaemus


Interesting Doughnut 0 VT Score for a "Test?" Doc leading to #Metasploit labs.inquest.net/dfi/sha256/e40… FYI: We heard some others seeing some waves of this week. James William MacArthur ExecuteMalware Nick Chalard

As a follow up to the previous graphic outlining threats affecting #Ukraine, here is a high level blog on observed threats. Big thanks to the #infosec community for making this possible, #SlavaUkraini William MacArthur Nick Chalard J. A. Guerrero-Saade Jon Gorenflo 🇺🇦🌻 inquest.net/blog/2022/04/0…


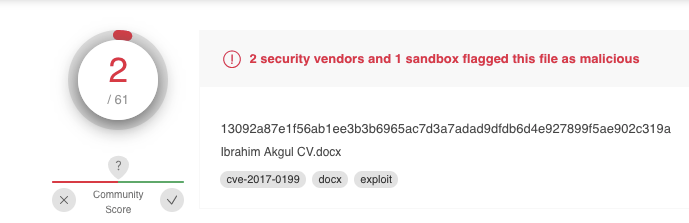
Low scoring #maldoc using OhioHealth, protected file in the lure. labs.inquest.net/dfi/sha256/130… William MacArthur James ExecuteMalware

Looks like #Qbot is back in action. Green Lure seen at least, where is the blue :P labs.inquest.net/dfi/sha256/637… 5.254.118.]198 91.194.11.]15 146.70.87.]163 James Cryptolaemus William MacArthur Nick Chalard
![InQuest (@inquest) on Twitter photo Looks like #Qbot is back in action. Green Lure seen at least, where is the blue :P
labs.inquest.net/dfi/sha256/637…
5.254.118.]198
91.194.11.]15
146.70.87.]163
<a href="/James_inthe_box/">James</a>
<a href="/Cryptolaemus1/">Cryptolaemus</a>
<a href="/Anti_Expl0it/">William MacArthur</a>
<a href="/Autow00t/">Nick Chalard</a> Looks like #Qbot is back in action. Green Lure seen at least, where is the blue :P
labs.inquest.net/dfi/sha256/637…
5.254.118.]198
91.194.11.]15
146.70.87.]163
<a href="/James_inthe_box/">James</a>
<a href="/Cryptolaemus1/">Cryptolaemus</a>
<a href="/Anti_Expl0it/">William MacArthur</a>
<a href="/Autow00t/">Nick Chalard</a>](https://pbs.twimg.com/media/FSV3kDZX0AYEwME.jpg)








InQuest and Zscaler ThreatLabz have analyzed #MysticStealer, a new malware family that extracts data from various sources, including web browsers and cryptocurrency wallets, through its obfuscation techniques ➡️ bit.ly/3N7IHe1 #Malware #CyberSecurity #Cryptocurrency