0xor0ne
@0xor0ne
| CyberSecurity | Reverse Engineering | C and Rust | Exploit | Linux kernel | PhD | My Tweets, My Opinions :) |
ID: 1293289704843075586
https://github.com/0xor0ne 11-08-2020 20:54:59
2,2K Tweet
62,62K Followers
528 Following











FortiGate firewalls: bare metal firmware encryption reverse engineering bishopfox.com/blog/breaking-… Credits Jon Williams (Bishop Fox) #cybersecurity #Fortinet


A few notes on dealing with binaries for embedded devices research.nccgroup.com/2024/06/05/cro… Credits Domen Puncer Kugler (NCC Group Research & Technology) #infosec #Linux



Musl c library Heap allocator exploitation (CVE-2022-24834) research.nccgroup.com/2024/06/11/pum… Credits Aaron Adams (NCC Group Research & Technology) #exploit #cybersecurity



Two part series on security analysis and exploitation of the Phoenix Contact CHARX SEC-3100 charging controller Part 1: blog.ret2.io/2024/07/17/pwn… Part 2: phoenixcontact.com/en-us/products… Credits RET2 Systems #automotive #cybersecurity


Useful guide on Linux page cache, memory management, mmap and cgroups biriukov.dev/docs/page-cach… Credits Viacheslav Biriukov #Linux #cybsersecurity


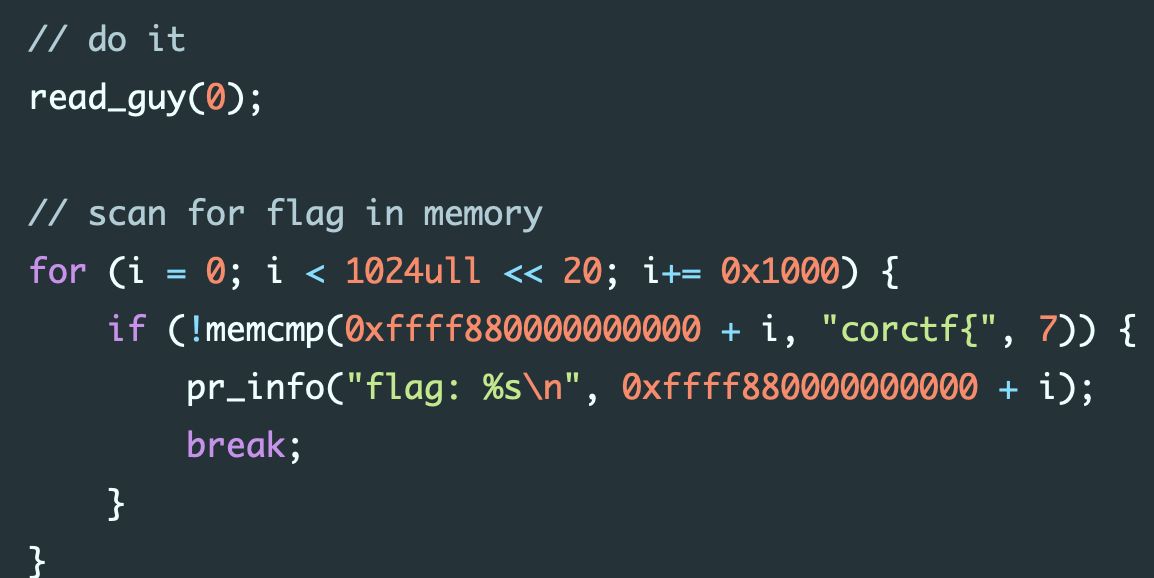
KVM escape CTF challenge (corCTF 2024) solution writeup zolutal.github.io/corctf-trojan-… Credits Justin Miller #Linux #cybersecurity

Beginners intro to x64 Linux Binary Exploitation (Dimitrios 🪼🪼 🇺🇦) Basic: valsamaras.medium.com/introduction-t… Return into lib: valsamaras.medium.com/introduction-t… RoP Chains: valsamaras.medium.com/introduction-t… Stack Canaries: valsamaras.medium.com/introduction-t… ASLR: valsamaras.medium.com/introduction-t… #exploit #infosec