DiasS
@0xDiasS
CyberSec Boy | Founder of @P4Hacking
ID:829799534003884032
09-02-2017 21:10:00
71 Tweets
80 Followers
421 Following


Bipin Jitiya 1/5: There is a quick explanation about this payload for the people who are asking: Certainly, here's a more detailed tweet comment explaining the payload:
This payload is an attempt to bypass WAF.
It disguises 'echo' and uses '$IFS' to evade detection.




The Security Reference Guide by s0cm0nkeysec is an excellent, well-curated and well-organised repository of cybersecurity resources! 👇
s0cm0nkey.gitbook.io/s0cm0nkeys-sec…

My talk is now available on youtube. Thanks owasplisboa, for giving me the opportunity to share my experience.
youtube.com/watch?v=l_ODT7…




Excellent introduction to Linux kernel exploitation
Series by I write about security stuff
Debugging with QEMU: blog.k3170makan.com/2020/11/linux-…
Stack Overflows: blog.k3170makan.com/2020/11/linux-…
RIP control: blog.k3170makan.com/2021/01/linux-…
#cybersecurity



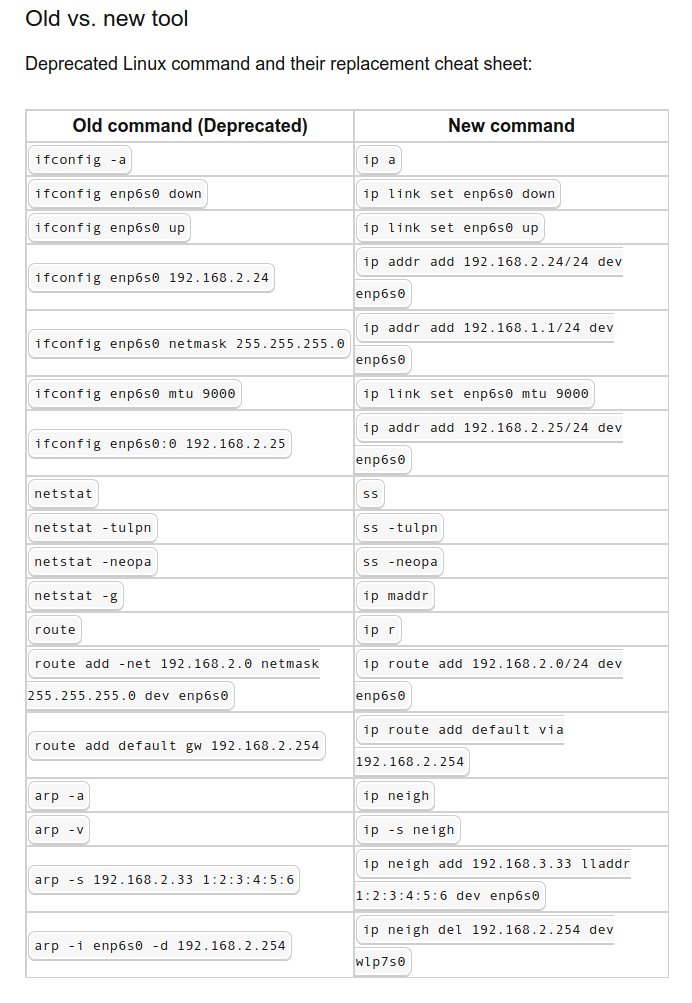
Old vs New Linux Commands
#infosec #cybersecurity #cybersecurity tips #pentesting #oscp #redteam #informationsecurity #cissp #CyberSec #networking #networksecurity #CheatSheet #infosec urity #cyberattacks #security #linux #hacker #vulnerabilities #bugbounty #bugbounty tips