Netlas.io
@Netlas_io
Stay ahead with updates on high-profile vulnerabilities, expert tutorials, essential safety tips, and the latest Netlas developments.
ID:1329396092409143296
http://netlas.io 19-11-2020 12:09:00
257 Tweets
3,8K Followers
10 Following








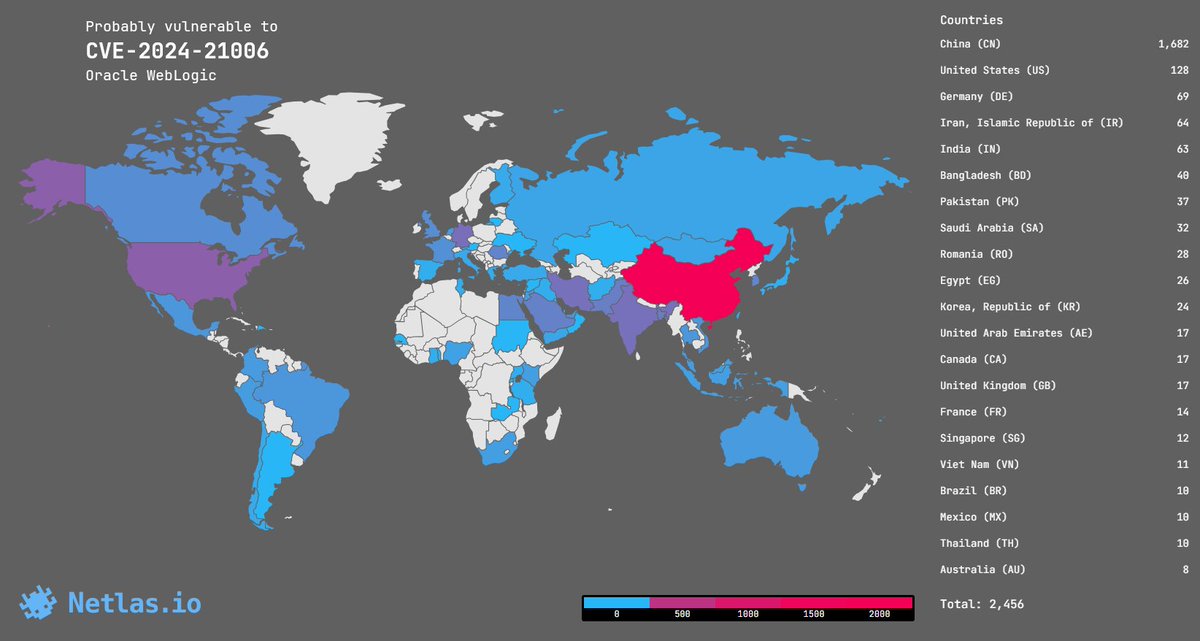
How to find all root domains during reconnaissance with Netlas.io:
registrant.organization:'Organization name'
👉 Read more about recon with Netlas: nt.ls/recon
#cybersecurity #bugbounty #pentest #tips
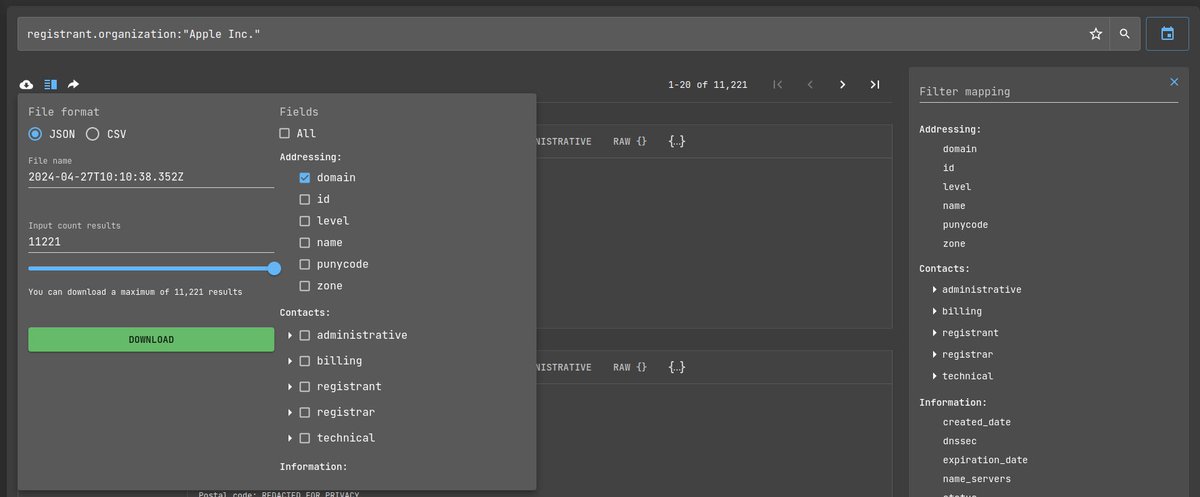





Business-focused OSINT with Netlas.io 🔎
Our new article is devoted to researching company resources using Netlas tools.
It shows how to collect contacts, files, explore subnets and much more. Read it quickly!
👉 Read here: nt.ls/osint
#cybersecurity




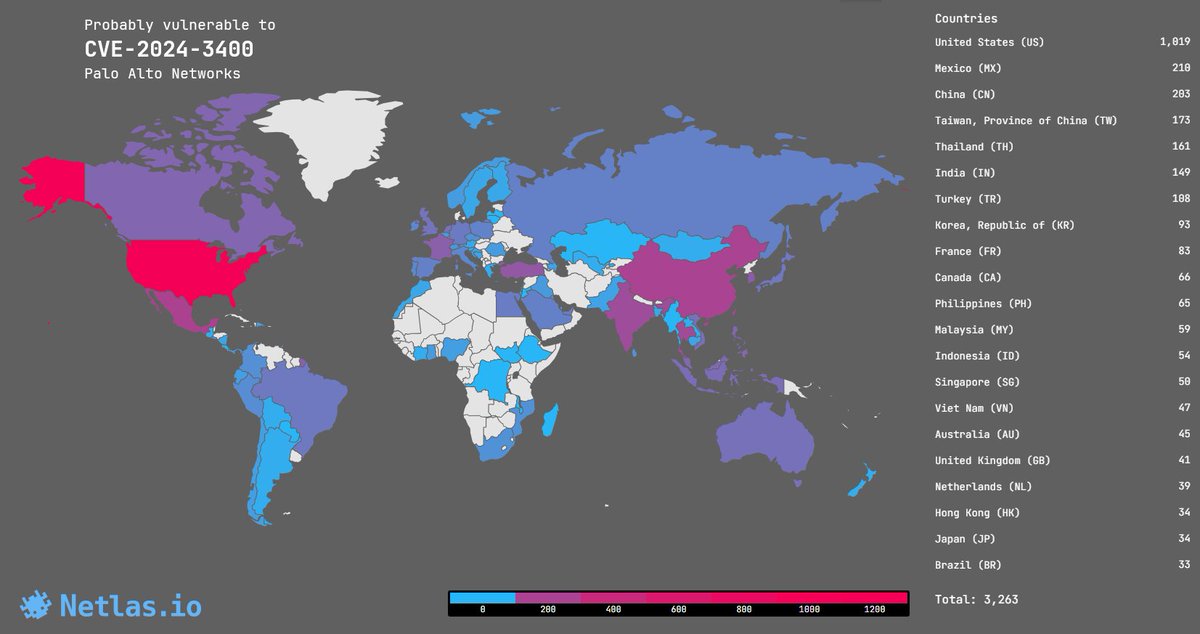
CVE-2024-3400: command injection in Palo Alto Networks PAN-OS, 10.0 rating 🔥🔥🔥
A 0-day vulnerability in PAN-OS that allows an unauthenticated attacker to execute arbitrary code on the firewall with root rights. According to Palo Alto Networks, attacks have already been carried