Swissky
@pentest_swissky
RedTeam | Pentest
Author of PayloadsAllTheThings & SSRFmap
github.com/swisskyrepo
ID: 791188064
https://linktr.ee/swissky 30-08-2012 09:10:37
12,12K Tweet
19,19K Takipçi
1,1K Takip Edilen



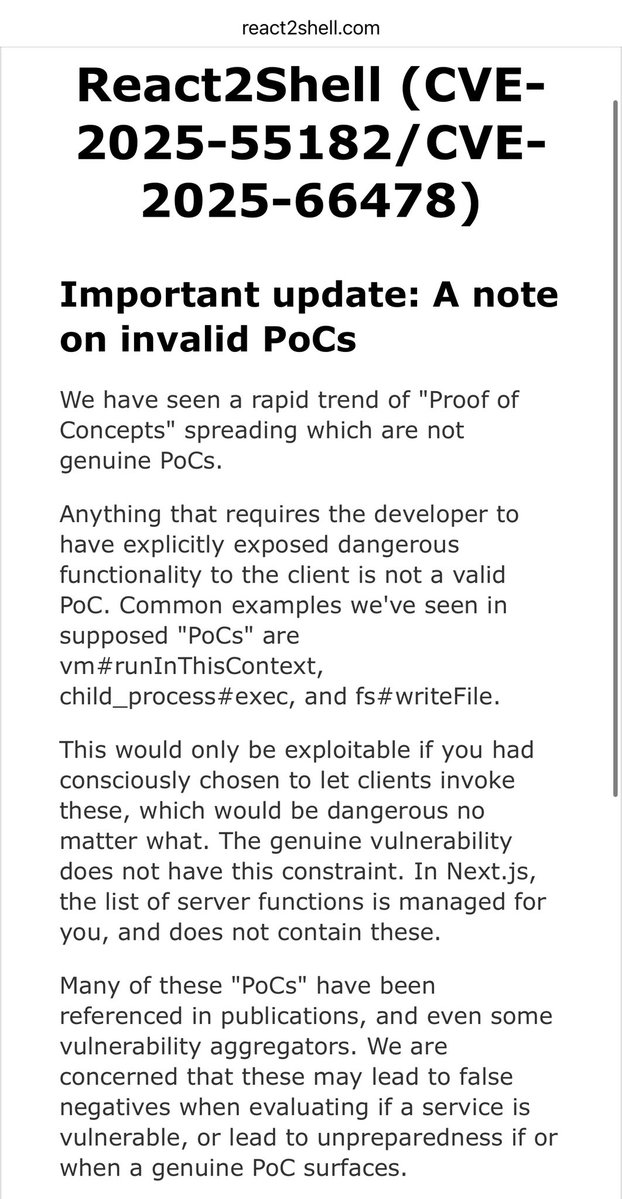
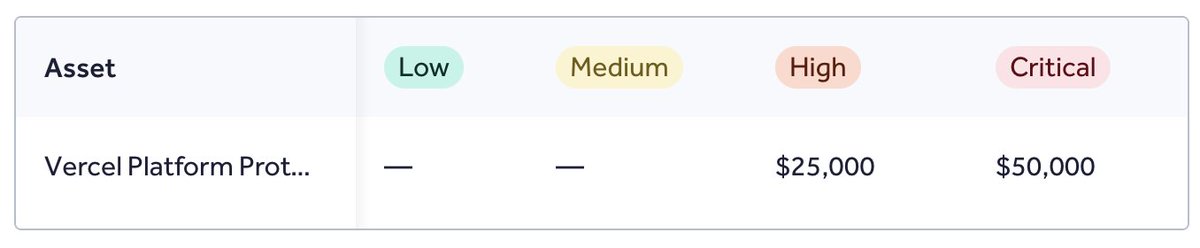
Our Security Research team at Searchlight Cyber just published a high-fidelity detection mechanism for the Next.js/RSC RCE (CVE-2025-55182 & CVE-2025-66478) - slcyber.io/research-cente…. There are a lot of PoCs on GitHub that are adding noise to the problem; I hope this helps people!



SupaPwn: Hacking Our Way into Lovable's Office and Helping Secure Supabase - s1r1us (mohan) Harsh Jaiswal hacktron.ai/blog/supapwn





Grafana Dashboard for my Blackstone Smoker - Paul Sec.jpeg .exe paulsec.github.io/posts/grafana-…


TROOPERS25: The Crypto Game of North Korea Stealing Money with Chrome 0 days - Boris Larin youtu.be/5ezmnd6Z96o

Guess what was vulnerable to the new React RCE? All my side projects created with Google's AI Studio, including BugBountyDaily.com! Logan Kilpatrick, any way to avoid this in the future? Maybe automated patches or daily builds that automatically update imported packages to




Hack-cessibility: When DLL Hijacks Meet Windows Helpers - Oddvar Moe trustedsec.com/blog/hack-cess…