
Adli Wahid
@adliwahid
Tweets are personal. Bee photos on Instagram instagram.com/adliwahid
ID: 44102641
http://my.linkedin.com/in/adliwahid 02-06-2009 11:36:55
11,11K Tweet
2,2K Followers
2,2K Following


The documentary that the BBC refused to air showing the targeting, detainment and torture of medics in Gaza by Israeli authorities was broadcast by Channel 4 last night. Amnesty International researcher, Budour Hassan, explains the use of secret sites by the Israeli authorities.



OVER x SLIDES & VIDEOS 📣 #pts25 is now over, thanks so much to all 🙏 🚨 As always, due to the 🔥 work of the team, you can browse/follow *all* talks: 📖 Slides: archives.pass-the-salt.org/Pass%20the%20S… 🎦 Videos : passthesalt.ubicast.tv/channels/#2025 Thanks again & we wish you a fantastic summer ❤️ 😎







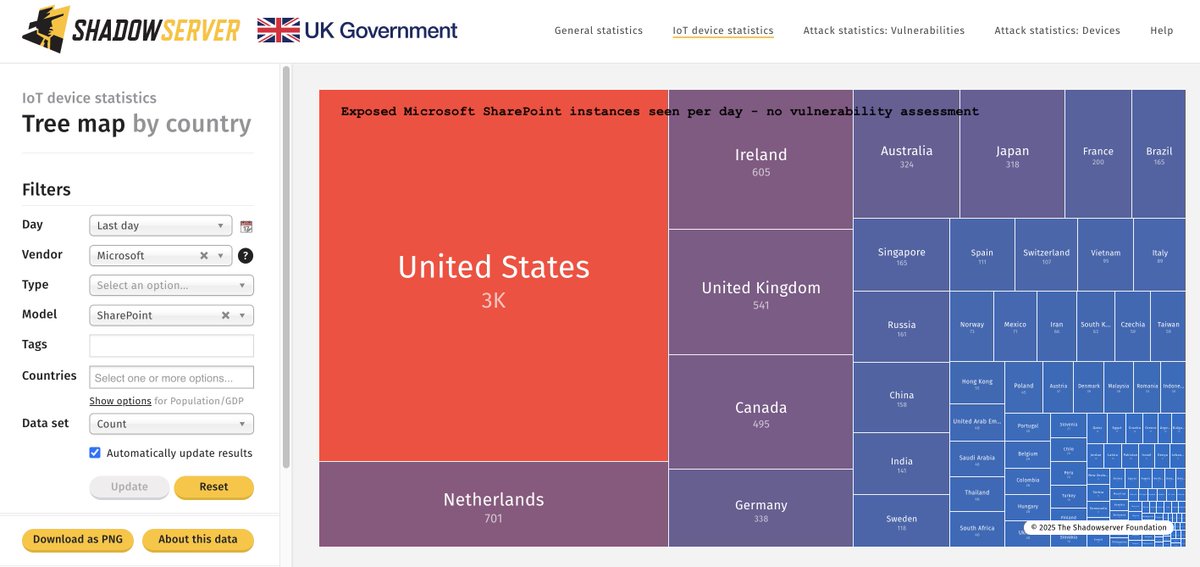
Alert: SharePoint CVE-2025-53770 incidents! In collaboration with Eye Security & watchTowr we are notifying compromised parties. Read: research.eye.security/sharepoint-und… ~9300 Sharepoint IPs seen exposed daily (just population, no vulnerability assessment): dashboard.shadowserver.org/statistics/iot…



Thanks to a scan conducted by LeakIX, we have shared SharePoint IPs confirmed vulnerable to CVE-2025-53770, CVE-2025-53771. 424 SharePoint IPs found on 2025-07-23. One-off data in our Vulnerable HTTP report - shadowserver.org/what-we-do/net… Tree map: dashboard.shadowserver.org/statistics/com…







A North Korean Linux stealth rootkit was revealed in the latest issue of Phrack Zine. We analyzed it and discuss detection techniques to help security teams see if they are affected. Read more below for tips on how to find this and related threats: sandflysecurity.com/blog/leaked-no…






