Dave Aitel
@daveaitel
Cyber Security Researcher | Policy Analyst | Partner at https://t.co/OpZchMm8Sz | @[email protected]
ID:8371802
http://www.aitelfoundation.org 23-08-2007 00:57:41
92,5K Tweets
28,8K Followers
1,6K Following

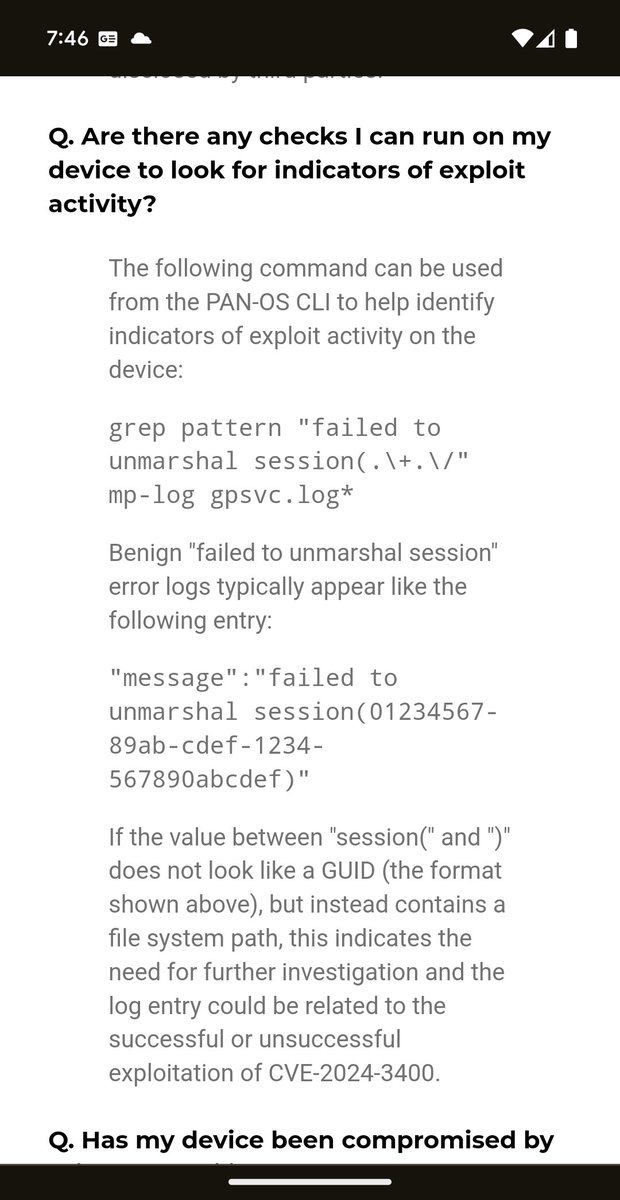
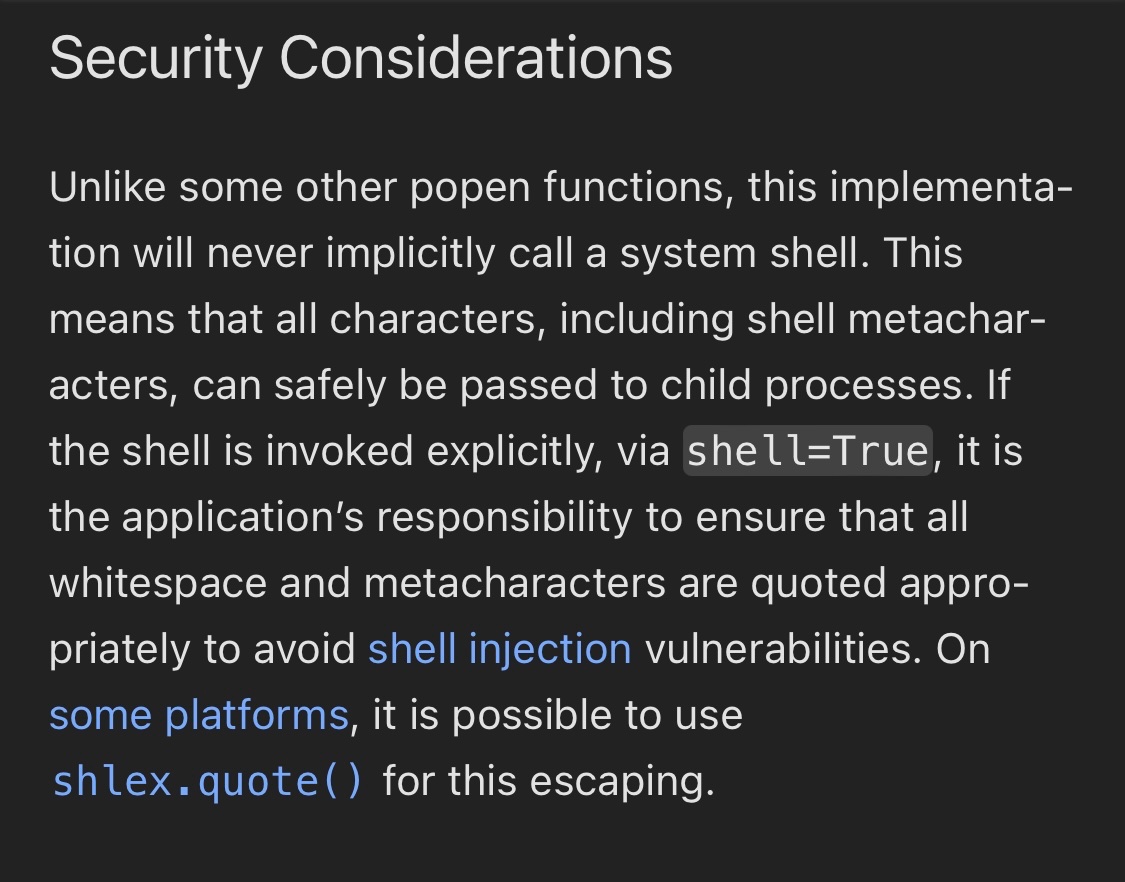
Dave Aitel Yes and also time to recognize most of the vulnerable functionality in these edge devices is implemented in memory safe languages. I’m good with the push on memory safety but maybe time for a USG campaign for “no more shelling out for developer convenience”.








Brian in Pittsburgh Dave Aitel I love how they use the language that it 'is no longer an effective mitigation'
As in, it used to block the vulnerability at the time of writing it.
But somehow the world changed to make them now wrong.