Bas Westerbaan
@bwesterb
Software-engineering mathematician. Post-quantum cryptography @cloudflare
ID:23593
https://bas.westerbaan.name 26-11-2006 21:43:49
567 Tweets
950 Followers
148 Following



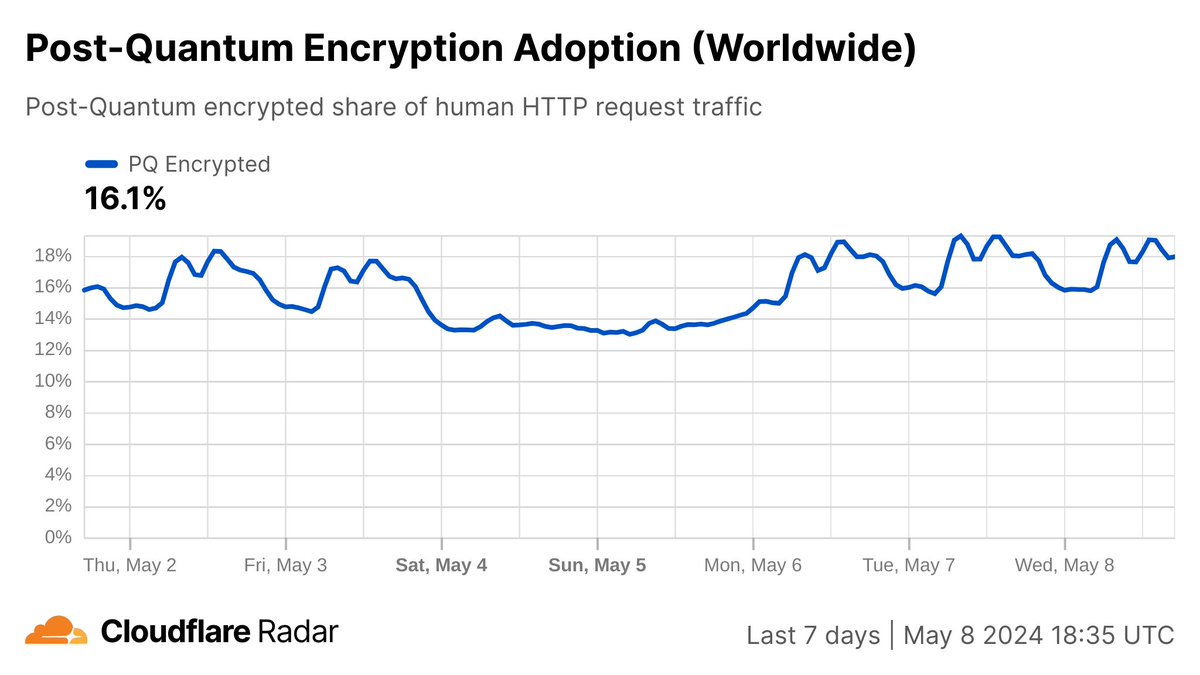
Since the release of Chrome 124 on April 17, we've been tracking post-quantum encrypted requests as a share of Cloudflare global HTTPS request traffic. Now you can too, in the new Post-Quantum Encryption Adoption graph in the Adoption & Usage section of CloudflareRadar.


Halfway through the return journey and I have something concrete to say about it: sam-jaques.appspot.com/static/files/5…
I didn't make it past step 4, but I tried to give some intuition on complex gaussians and Karst waves
(ICYMI others discovered a critical flaw; see the updated eprint)