Unit 42
@Unit42_Intel
The latest research and news from Unit 42, the Palo Alto Networks (@paloaltontwks) Threat Intelligence and Security Consulting Team covering incident response.
ID:4487645412
https://unit42.paloaltonetworks.com/ 07-12-2015 16:30:42
2,3K Tweets
50,7K Followers
88 Following

2024-04-30 (Tuesday): We've found several seemingly legitimate websites hosting JavaScript-based #webskimmers . List of associated file hashes for examples of skimmer code and domains used by endpoints collecting the stolen data are available at bit.ly/3Wn4apC

The XQL queries for hunting for known IoCs have been updated in our threat brief on #CVE20243400 : bit.ly/43YOECb



Our threat brief on #CVE20243400 has been substantially updated. Updated sections include Current Scope of the Attack and the section on Operation MidnightEclipse activity. bit.ly/43YOECb

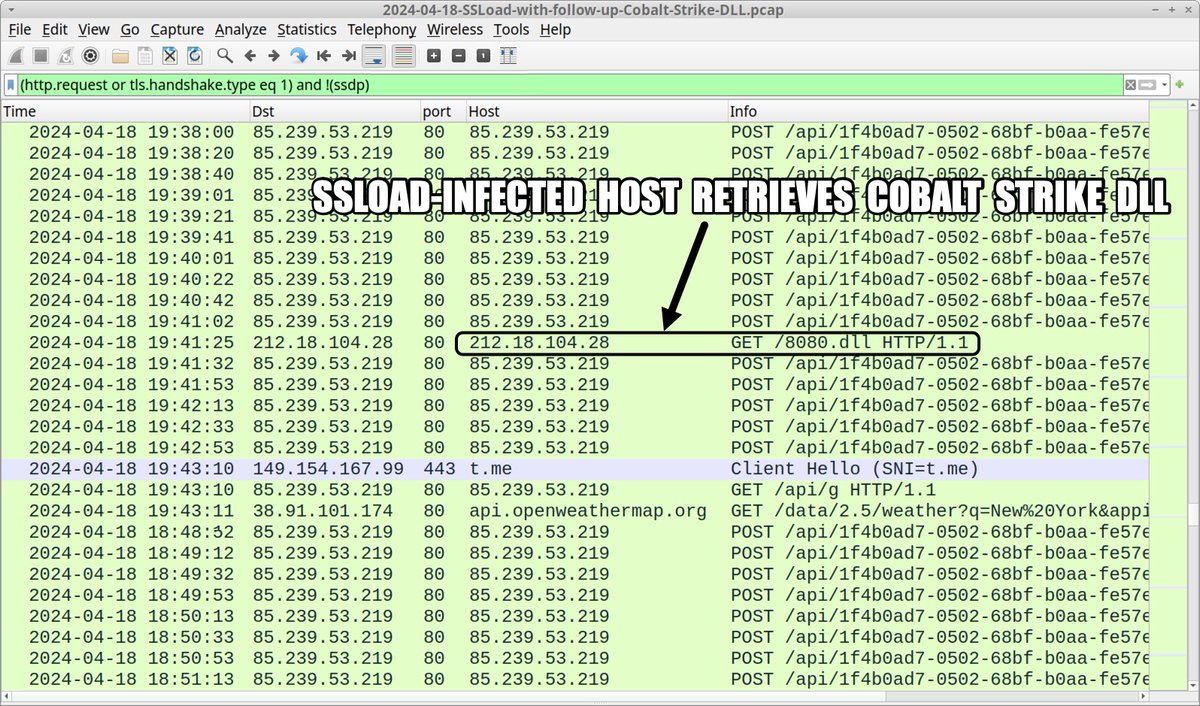
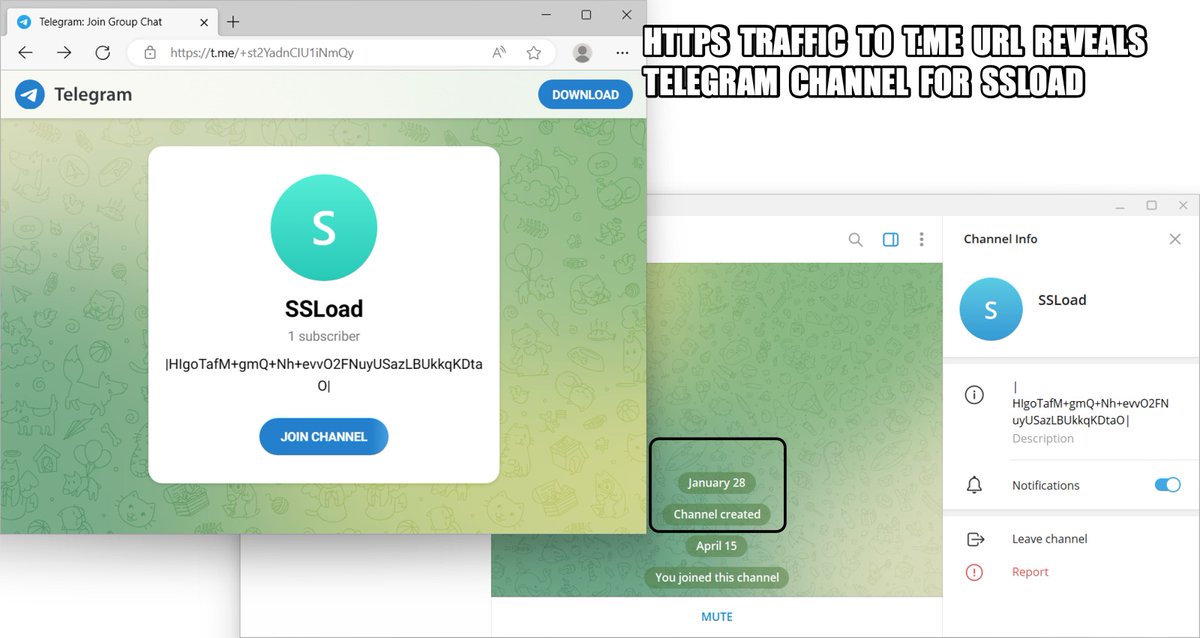
2024-04-18 (Thursday): #SSLoad infection leads to #CobaltStrike DLL. In this case we saw no follow-up Cobalt Strike C2 traffic. List of indicators available at bit.ly/3Q9SORR
#TimelyThreatIntel #Unit42ThreatIntel #Wireshark #InfectionAnalysis

We've updated interim guidance as well as new information on coming fixes in our threat brief tracking exploitation of #CVE20243400 : bit.ly/43YOECb


Our threat brief on Operation MidnightEclipse, tracking exploitation of #CVE20243400 , now has new indicators as well as lists of commands seen in exploitation attempts: bit.ly/43YOECb


2024-04-15 (Monday): #ContactForms campaign pushing #SSLoad malware as early as Thursday, 2024-04-11. List of indicators available at bit.ly/49Cz1kL
#Wirshark #Unit42ThreatIntel #TimelyThreatIntel #InfectionTraffic


Malicious activity tracked under the campaign #OperationMidnightEclipse is targeting CVE-2024-3400, which exploits a vulnerability in certain versions of PAN-OS software. This threat brief covers mitigations and product protections: bit.ly/3vPUngM



#MuddledLibra , a financially-motivated group, is now exploiting both SaaS and CSP environments for data exfiltration. We detail common exploits and tactics seen — showing a pattern analysts can identify. Read more: bit.ly/43VgH5s
#CloudThreatLandscape #Cybercrime



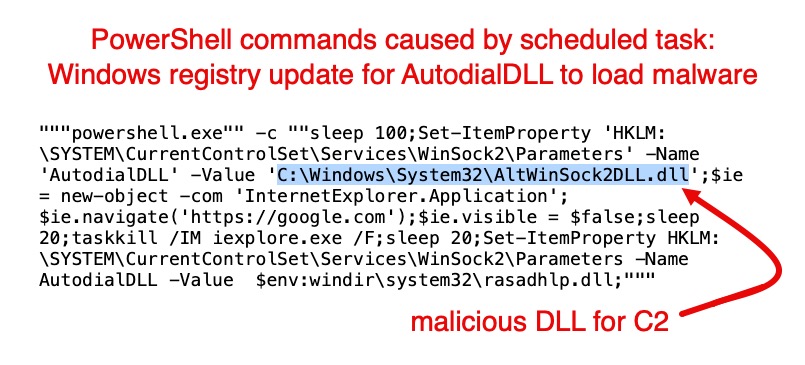
Our telemetry revealed an interesting case of #BoggySerpens ( #MuddyWater ) against a Middle East target: Persistence through scheduled task that runs PowerShell to abuse AutodialDLL registry key. AutodialDLL loads DLL for C2 framework. Details at bit.ly/4aIQDMU

This week on #ThreatVector : David Moulton, Director of Thought Leadership at Unit 42, welcomes Donnie Hasseltine, VP of Security at Second Front Systems and former Recon Marine, to discuss the value of a military mindset in cybersecurity.
Listen in. bit.ly/3TKVfLF



2024-04-04 (Thursday): We generated an infection in a lab environment based on the latest round of #KoiLoader / #KoiStealer activity. Initial bank-themed lures started earlier this week on 2024-04-02. Some indicators available at bit.ly/3PQut3r
#Unit42ThreatIntel


Two Chinese-linked APTs targeted entities or countries affiliated with ASEAN in March. #StatelyTaurus ( #MustangPanda ) distributed #malware using interest in the ASEAN-Australia Special Summit to create lures. The second targeted government infrastructure. bit.ly/3TtqE58