
Germán Fernández
@1ZRR4H
🏴☠️ OFFENSIVE-INTEL 🏴☠️ Cyber Threat Intelligence by Hackers | Security Researcher en https://t.co/rDrSxZASB3 | @CuratedIntel Member | 🥷🧠🇨🇱
ID:37090957
http://www.offensive-intel.com 02-05-2009 00:36:28
30,4K Tweets
28,4K Followers
577 Following

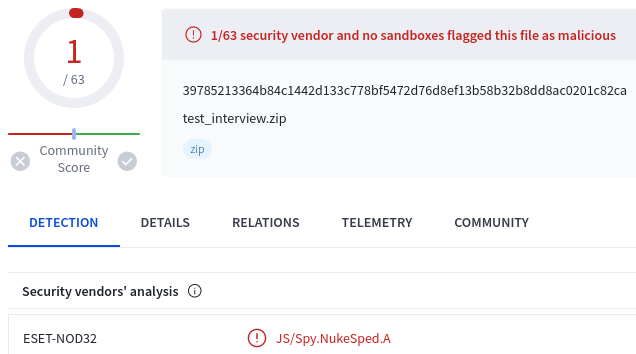
'test_interview.zip': 39785213364b84c1442d133c778bf5472d76d8ef13b58b32b8dd8ac0201c82ca
Maybe ESET caught something interesting here...
🤔
Shadow Chaser Group Jazi Florian Roth Germán Fernández

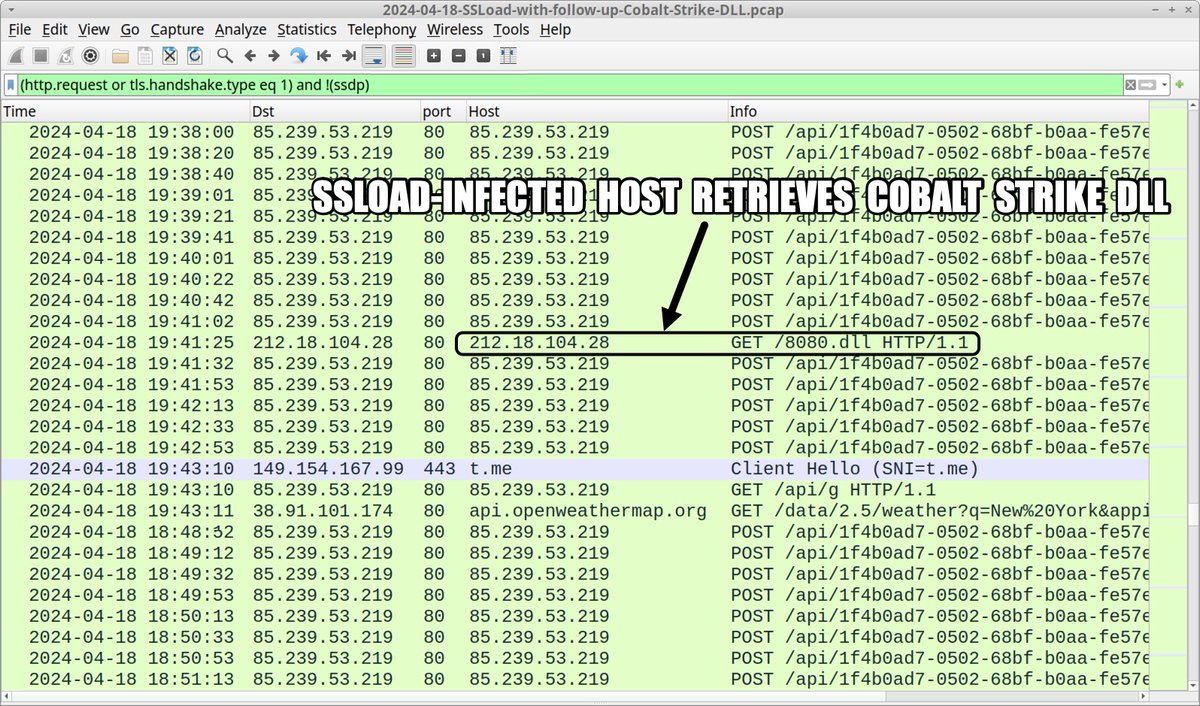
2024-04-18 (Thursday): #SSLoad infection leads to #CobaltStrike DLL. In this case we saw no follow-up Cobalt Strike C2 traffic. List of indicators available at bit.ly/3Q9SORR
#TimelyThreatIntel #Unit42ThreatIntel #Wireshark #InfectionAnalysis



'Indeed Resume Export 4001901\.zip': c796ea83815c2ea21228a5e4964cbe2f8a297648fd6e37928c1c722600c15051
'Indeed Resume Export 4001901.pdf.lnk': fba6c3f93838656c9627006913ad14a6d9645998e72df06f3df2107e0ddd4980
🤔
Germán Fernández




🔥 Tan solo han pasado 8 días desde mi alerta sobre #BlackHatSeo en distintos sitios web de la Fuerza Aérea del Perú Fuerza Aérea del Perú, y ahora el CSIRT GOB CL informa sobre la recepción de 🎣 #Phishing desde la dirección IP 38.43.155[.]5, la cual corresponde a fasmail.fap[.]mil[.]pe.
![Ven0m (@V3n0mStrike) on Twitter photo 2024-04-17 01:36:15 🔥 Tan solo han pasado 8 días desde mi alerta sobre #BlackHatSeo en distintos sitios web de la Fuerza Aérea del Perú @fapperu, y ahora el @CSIRTGOB informa sobre la recepción de 🎣#Phishing desde la dirección IP 38.43.155[.]5, la cual corresponde a fasmail.fap[.]mil[.]pe. 🔥 Tan solo han pasado 8 días desde mi alerta sobre #BlackHatSeo en distintos sitios web de la Fuerza Aérea del Perú @fapperu, y ahora el @CSIRTGOB informa sobre la recepción de 🎣#Phishing desde la dirección IP 38.43.155[.]5, la cual corresponde a fasmail.fap[.]mil[.]pe.](https://pbs.twimg.com/media/GLVIJaeXsAAL_bG.png)



Have you ever wondered what is going on with Vietnamese 🇻🇳 malware targeting Facebook accounts?
I did, so you can get a quick overview of these threat actors activities and how they are spending (and earning) millions of $$$
Read now! 👇👀 #dropshipping
g0njxa.medium.com/from-vietnam-t…

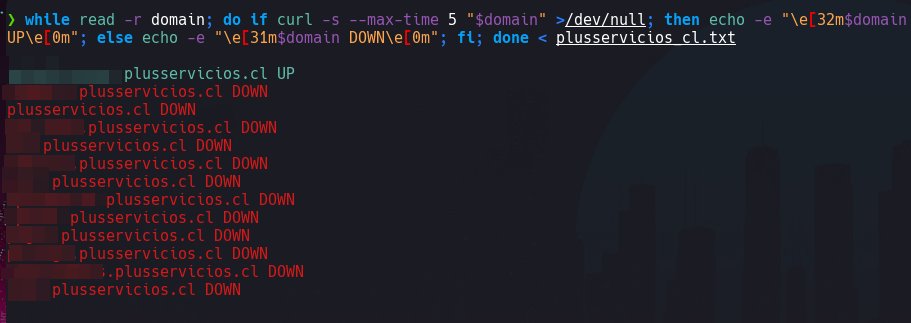
🚨🇨🇱 La empresa Plus Consulting (servicios de cobranza) está respondiendo a un nuevo ataque de #ransomware desde el pasado domingo 14 de abril.
'La naturaleza del incidente corresponde a un ransomware que afectó servidores Microsoft y VMware ESXi en la red de nuestra








![MalwareHunterTeam (@malwrhunterteam) on Twitter photo 2024-04-17 20:58:37 Opendir: https://tceh[.]us/ Maybe @Namecheap will nuke it... Opendir: https://tceh[.]us/ Maybe @Namecheap will nuke it...](https://pbs.twimg.com/media/GLZS2ajbAAABStM.png)


![Padawan (@johnk3r) on Twitter photo 2024-04-16 19:52:18 Submitted a few minutes ago on VT: MSI file from the first stage of #Ousaban signed with EV certificate. Sample: bazaar.abuse.ch/sample/6a94447… Payload: hxxp://94.103.83[.]221/tiru/ I've seen it before, but it's not that common. Submitted a few minutes ago on VT: MSI file from the first stage of #Ousaban signed with EV certificate. Sample: bazaar.abuse.ch/sample/6a94447… Payload: hxxp://94.103.83[.]221/tiru/ I've seen it before, but it's not that common.](https://pbs.twimg.com/media/GLT6f39a8AAin2e.jpg)
![MalwareHunterTeam (@malwrhunterteam) on Twitter photo 2024-04-16 13:37:52 191.96.225[.]117 🤔 @1ZRR4H 191.96.225[.]117 🤔 @1ZRR4H](https://pbs.twimg.com/media/GLSk8vsWYAEPYgI.jpg)
![Germán Fernández (@1ZRR4H) on Twitter photo 2024-04-16 02:58:22 ▪ Another python stealer targeting Facebook Business accounts (Ads Manager) and hosted on Github. https://github[.]com/sea2check/home The lure is a job offer impersonating the L'Oréal brand, so we can already imagine how they distribute this threat. ▪ Another python stealer targeting Facebook Business accounts (Ads Manager) and hosted on Github. https://github[.]com/sea2check/home The lure is a job offer impersonating the L'Oréal brand, so we can already imagine how they distribute this threat.](https://pbs.twimg.com/media/GLQMeAcXAAAWH2m.png)
![Cyber Team (@Cyberteam008) on Twitter photo 2024-04-15 06:46:42 #Fofabot Query for #APT41 / #Barium #APT Infra Query: cert.subject.cn='as.website' Link: en.fofa.info/result?qbase64… Infra: 194.156.99[.]115 173.199.71[.]210 45.77.65[.]219 107.191.47[.]199 185.174.172[.]41 65.20.98[.]31 195.85.250[.]254 #Malware #ioc #CTI #Fofabot Query for #APT41 / #Barium #APT Infra Query: cert.subject.cn='as.website' Link: en.fofa.info/result?qbase64… Infra: 194.156.99[.]115 173.199.71[.]210 45.77.65[.]219 107.191.47[.]199 185.174.172[.]41 65.20.98[.]31 195.85.250[.]254 #Malware #ioc #CTI](https://pbs.twimg.com/media/GLL9HIOa0AAvyOl.jpg)