0xSudip
@0xsudip
Bug Hunter |
YouTube ( BugBounty POC's): youtube.com/channel/UCzrYD…
ID: 1192968841665470464
https://0xsudip.github.io 09-11-2019 00:55:18
1,1K Tweet
577 Followers
871 Following


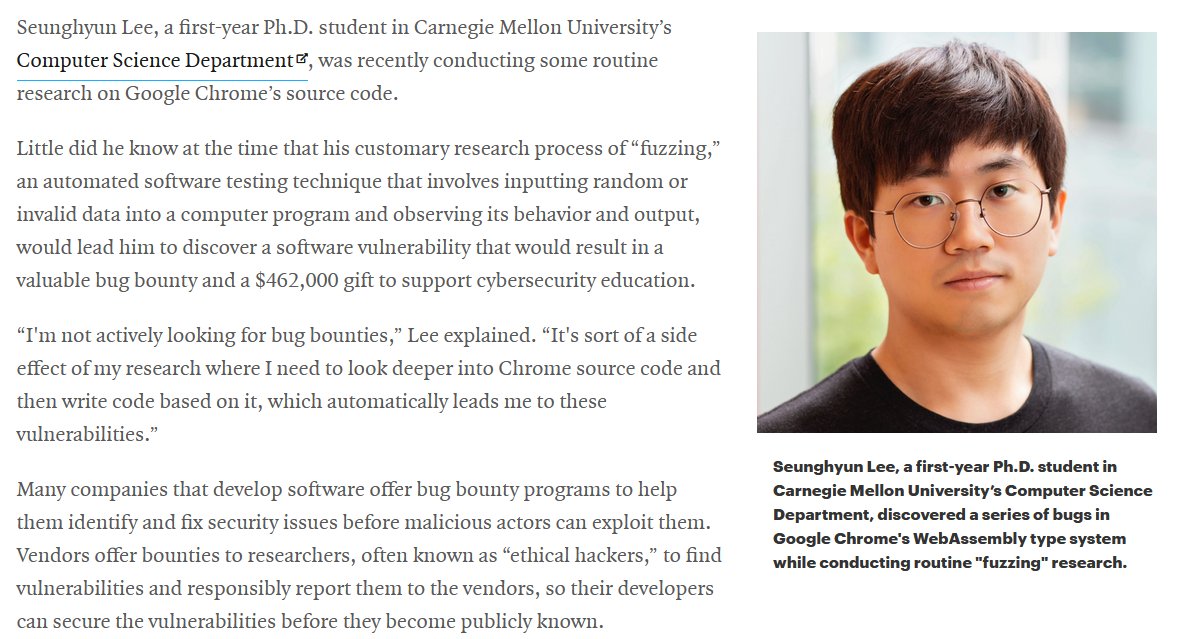
This guy gave away $462,000 of the #bugbounty he earned on Google VRP (Google Bug Hunters) to picoCTF – a massive show of gratitude for the skills he gained by playing their CTFs. Talk about giving back to the community! What a chad. cylab.cmu.edu/news/2025/01/0… #infosec #cybersecurity #infosec












Gareth Heyes \u2028 The final HTML would look like this: <img src="/images/tracker.gif?search=a" srcset="FFF" onerror="alert();//""> In this case we can still trigger the onerror event handler by setting invalid image path for srcset even though src has the valid path. #bugbounty





tl;dr of today > rastaland.TV gets crypto drained > he has stage 4 cancer > hes targeted specifically for his cancer treatment money > loses $32,000 > nerds band together > Alex Becker 🍊🏆🥇 donates $30,000 to him > malware nerds come together > drainer infra found > pull all victim